 Technology peripherals
Technology peripherals
 AI
AI
 How robust identity verification supports your sustainability strategy
How robust identity verification supports your sustainability strategy
How robust identity verification supports your sustainability strategy

Every company now needs to develop a sound sustainability strategy, regardless of its industry or business size. With the increasingly stringent requirements of legislators, it has become irreplaceable and no one can leave it. The main association with the term “sustainability” remains ecological. The first thing that comes to most people's minds is climate protection or the responsible use of natural resources. But sustainability encompasses much more than that. In addition to the "green" aspects, a comprehensive sustainability strategy also includes economic and social aspects, such as employee treatment, equity issues and the overall social mission that the company fulfills.
Sustainability and Certification? Yes, they belong together
Sustainability is not a problem that can be solved once and then shelved. A sound sustainability strategy involves constant change, improvement and further development. It requires ongoing commitment from everyone, from management to trainees. It is made up of many small things. Countless actions we take every day in both private and professional settings all contribute to lowering our carbon footprint. Energy saving lamps. Reusable coffee cups replace disposable cups. Take the train instead of the car when traveling for business. While the contribution of our actions to sustainable development may not always be obvious, there are opportunities almost everywhere. For example, customized authentication strategies also make a valuable contribution. The right access solution can clearly have a positive impact on your CO2 footprint – but only if you give it careful thought when choosing your supplier. The selected access solutions partner should set high standards for product and process quality, offer state-of-the-art technology and have sustainability high on its agenda. Only then can the required level playing field be created.
In this blog post, we introduce four ways to reduce your carbon footprint through modern certification, thereby making a significant contribution to sustainability.
Measure 1: Prioritize the use of mobile authentication solutions
Mobile authentication is becoming increasingly popular, using Bluetooth Low Energy (BLE) or Near Field Communication (NFC) technology. Users can authenticate through their smartphones, eliminating the need for additional identification media. This convenience cannot be underestimated. All they need to do is pick up their smartphone, which they always have with them anyway. Since there is no need to issue plastic ID cards or key fobs, it is a more environmentally friendly solution. Doing so reduces the amount of plastic waste and eliminates the problem of disposing or recycling the ID media. It should also be emphasized that the use of this marking medium enables significant savings in the energy required for production and processing. This move toward mobile authentication can also happen gradually. Parallel operations of several technologies are common. This is especially true in environments where a card or keychain is sometimes indispensable. With universal RFID readers, more than 60 different relay technologies can be integrated. Here you have complete flexibility to implement your sustainability strategy step-by-step.
Measure 2: Focus on product quality and life cycle management
In addition to the ID media just discussed, the hardware also includes readers and other components. There's also a focus on quality, as using high-quality materials and workmanship can extend the life of your hardware. Experience shows that top-quality readers and ID media run longer, have lower error rates, and therefore need to be replaced less frequently – which in turn means less waste. If you choose to support an RFID-based access concept, the amount of waste is further reduced; since the verification process here is contactless, material wear is significantly reduced, which means that components can be used longer. But even the best hardware sometimes needs to be replaced – so what? Ensuring your authentication partner takes back old devices and properly disposes or recycles them provides solutions for the entire product lifecycle. This is the only way to consistently support your sustainability efforts.
Measure 3: Ensure future viability – use the right software
Software and hardware should be a powerful pair in your authentication solution. In the era of digital transformation, technology is constantly evolving and updating, so your access system needs to keep up with these developments and follow the trends of the times as much as possible. Experience shows that this always works best when the hardware is already "future-proofed" and can easily incorporate new technologies or map the company's changing needs without any problems. Otherwise, there is a risk that the hardware will have to be replaced again and again in a short period of time – which is not only financially disadvantageous, but also has a negative impact on the sustainability balance sheet due to the massive waste caused by readers and readers. ID media. Software components can now be operated by performing many routine tasks remotely such as updates, maintenance, etc. This also helps with environmental accounting; service staff don't have to go to them every time. This saves fuel and travel time and has a positive impact on the climate.
Measure 4: Aim for systems thinking, not siled solutions
Modern authentication solutions bundle more and more functionality into a single system, from building access and printer management to On-site parking access including electronic charging. All mappings use the same identification medium - if new functionality needs to be added or new technology implemented, the infrastructure is already there. Smart environments not only provide amazing conveniences to users but also enhance the attractiveness of organizations. They enable faster, more agile growth without sacrificing the environment. On the contrary: By integrating electronic charging in the company parking lot, employers actively support modern mobility, while smart printing minimizes the use of paper and the consumption of ink cartridges. Modern access control solutions not only offer the opportunity to continuously optimize processes, they also have a positive impact on energy consumption. User behavior within the building can be recorded, and room ventilation, lighting and heating can be automatically adjusted according to actual needs. If the office is empty on a Friday afternoon, the printer can go into standby or cool down operation without heating.
The above is the detailed content of How robust identity verification supports your sustainability strategy. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 How to implement single sign-on in PHP
Jun 11, 2023 pm 07:01 PM
How to implement single sign-on in PHP
Jun 11, 2023 pm 07:01 PM
Single sign-on (SSO) is an authentication mechanism that allows users to authenticate across multiple applications and sites using a single set of credentials, such as a username and password. This mechanism can improve user experience and efficiency while also enhancing security. In PHP, implementing single sign-on requires some specific methods. Below we will introduce how to implement single sign-on in PHP. We will divide it into the following steps: Create a user authentication center (AuthenticationCenter) using OAuth2
 How to disable private browsing authentication in Safari: How-to guide for iOS 17
Sep 11, 2023 pm 06:37 PM
How to disable private browsing authentication in Safari: How-to guide for iOS 17
Sep 11, 2023 pm 06:37 PM
In iOS 17, Apple introduced several new privacy and security features to its mobile operating system, one of which is the ability to require two-step authentication for private browsing tabs in Safari. Here's how it works and how to turn it off. On an iPhone or iPad running iOS 17 or iPadOS 17, if you have any Private Browsing tab open in Safari and then exit the session or app, Apple's browser now requires Face ID/TouchID authentication or a passcode to access again they. In other words, if someone gets their hands on your iPhone or iPad while it's unlocked, they still won't be able to view it without knowing your passcode
 Implementing user authentication using middleware in the Slim framework
Jul 29, 2023 am 10:22 AM
Implementing user authentication using middleware in the Slim framework
Jul 29, 2023 am 10:22 AM
Implementing user authentication using middleware in the Slim framework With the development of web applications, user authentication has become a crucial feature. In order to protect users' personal information and sensitive data, we need a reliable method to verify the user's identity. In this article, we will introduce how to implement user authentication using the Slim framework’s middleware. The Slim framework is a lightweight PHP framework that provides a simple and fast way to build web applications. One of the powerful features is the middle
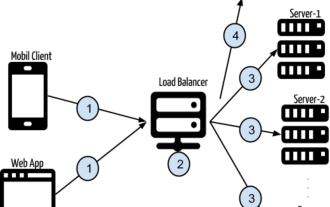 Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Authentication is one of the most important parts of any web application. This tutorial discusses token-based authentication systems and how they differ from traditional login systems. By the end of this tutorial, you will see a fully working demo written in Angular and Node.js. Traditional Authentication Systems Before moving on to token-based authentication systems, let’s take a look at traditional authentication systems. The user provides their username and password in the login form and clicks Login. After making the request, authenticate the user on the backend by querying the database. If the request is valid, a session is created using the user information obtained from the database, and the session information is returned in the response header so that the session ID is stored in the browser. Provides access to applications subject to
 How does AI artificial intelligence promote digital transformation?
Apr 12, 2024 pm 02:31 PM
How does AI artificial intelligence promote digital transformation?
Apr 12, 2024 pm 02:31 PM
It has been decades since artificial intelligence was proposed, but why has this technology experienced explosive growth only in recent years? This phenomenon is no accident. It is precisely thanks to the increasing maturity of digital technologies such as cloud computing, the Internet of Things, and big data that artificial intelligence has made substantial progress: cloud computing provides an open platform for artificial intelligence, and the Internet of Things ensures data security. Real-time sharing, and big data provides unlimited resources and algorithm support for deep learning. The integration of digital transformation of traditional enterprises and technologies in these fields has promoted the continuous upgrading of artificial intelligence technology, laying a solid foundation for its evolution from "intelligent perception" to "intelligent thinking" and "intelligent decision-making". Enterprises with strong digital innovation capabilities have an increasing influence on the market and consumers. Any digital transformation
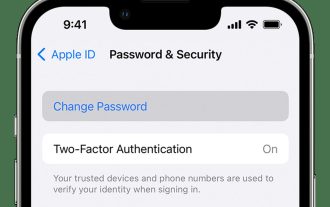 How to reset Apple ID password?
May 21, 2023 pm 05:01 PM
How to reset Apple ID password?
May 21, 2023 pm 05:01 PM
How to reset Apple ID password? If you forgot your AppleID password, don't worry. You can easily reset it using one of the following methods. Using your iPhone or other trusted Apple device is the fastest and easiest way to reset your password, as long as you have the device signed in with your Apple ID. Go to Settings and tap your name. Click Password & Security, then click Change Password. Follow the on-screen instructions to create a new password. Apple You can also use this method on a trusted iPad, iPod touch, or Apple Watch. Use the Apple Support App If you don't have an Apple device but have access to a trusted phone number, you can get a call from a friend or
 Cloudera announces new vice president of Greater China
Apr 09, 2024 pm 03:07 PM
Cloudera announces new vice president of Greater China
Apr 09, 2024 pm 03:07 PM
Beijing, China, April 9, 2024 - Cloudera, an enterprise big data and artificial intelligence platform company, today announced the appointment of a new vice president of Greater China. This move aims to further focus on customer success and business transformation, and help enterprises adapt to the development of big data and artificial intelligence applications and accelerate the digital transformation process by providing hybrid multi-cloud big data and big model capabilities. Cloudera now appoints Mr. Liu Fuchun as Vice President (RVP) of Greater China. He will be responsible for promoting Cloudera's further expansion in China and leading strategic sales, channel development and localization strategy. The appointment of Liu Fuchun, Vice President of Cloudera Greater China, as a new executive further demonstrates Cloudera’s commitment to
 Laravel development: How to manage user authentication with Laravel Guard?
Jun 13, 2023 pm 04:41 PM
Laravel development: How to manage user authentication with Laravel Guard?
Jun 13, 2023 pm 04:41 PM
Laravel development: How to manage user authentication with LaravelGuard? In web applications, security and user authentication are crucial. As your business grows, so does the number of users, and without a good user authentication scheme implemented, your application can be vulnerable to a variety of attacks, including malicious attacks, data leaks, and other security issues. Fortunately, the Laravel framework provides a simple yet effective way to handle user authentication. This method is called Gu



