Example analysis of Struts2 framework site risks
1. Overview
An open source project sponsored by the Apache Software Foundation (ASF) is Struts. The project started as a fork of the Jakarta project and was subsequently promoted to a top-level project of the ASF. By using Java Servlet/JSP technology, it implements the application framework [Web Framework] based on the Model-View-Controller [MVC] design pattern of Java EE Web applications. It is a classic product in the MVC classic design pattern.
In the early days of the development of Java EE Web applications, in addition to using Servlet technology, it was generally developed using a mixture of HTML and Java code in the source code of JavaServer Pages (JSP). These two methods are inevitable in mixing performance and business logic code, which brings huge complexity to early development and later maintenance. In order to get rid of the above constraints and limitations and clearly separate the business logic code from the presentation layer, in 2000, Craig McClanahan adopted the MVC design pattern to develop Struts. This framework product was once regarded as the most extensive and popular JAVA WEB application framework
Struts2 is a Web application framework based on the MVC design pattern. It is essentially equivalent to a servlet. In the MVC design pattern, Struts2 serves as a controller to establish data interaction between the model and the view. Struts 2 is the next generation product of Struts. It is a new Struts 2 framework that merges the technologies of struts 1 and WebWork
2. Vulnerability inventory
2.1. Vulnerability history
With the popularity of the Struts2 framework, more and more enterprise units are using the Struts2 framework for development. High-risk vulnerabilities have been exposed many times in recent years. Many government sites, banks, large Internet companies and other units have been affected, such as : In December 2016, Jingdong 12G user data was leaked, including usernames, passwords, emails, QQ numbers, phone numbers, ID cards and other dimensions. The data amounted to tens of millions of pieces. The reason originated from 2013 Security vulnerabilities in Struts 2. At that time, almost all Internet companies and a large number of banks and government agencies in the country were affected, resulting in a large number of data leaks. Every time a vulnerability broke out in struts2, major Internet vulnerability platforms also received multiple feedbacks such as:
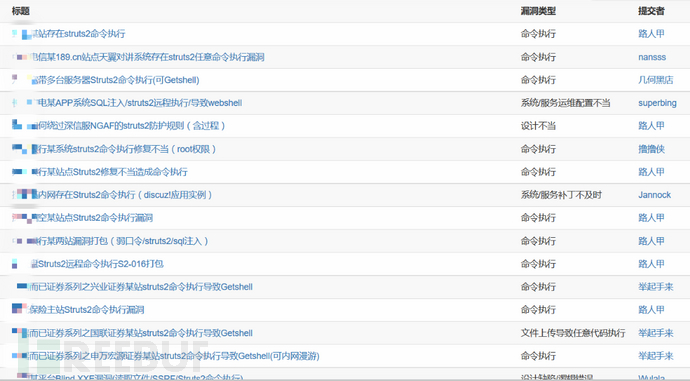
#The code execution problem of Struts2 dates back to 2010, when Meder Kydyraliev from the Google Security Team discovered that the parameter interceptor could be bypassed by using unicde encoding for special characters. The filtering of "#" caused code execution problems. The official vulnerability number was S2-003,
Looking back at the struts2 vulnerability history, we found that the official was not to blame. First of all, developers did not have strong security awareness. Although they took measures Basic security measures, but in name only. Secondly, we feel that the official repair measures lack strength and seem to be only perfunctory, without truly solving the root cause of the problem. Furthermore, the official openness spirit is really shocking. They even directly posted the PoC of the vulnerability on the official website. This gave many people the opportunity to further study the exploitation of the vulnerability. This is also one of the reasons why the problem is more serious.
2.2. Struts2 vulnerability inventory
Struts2 vulnerabilities that have a relatively large impact and are widely exploited:
CVE-2010-1870XWork ParameterInterceptors bypass allows OGNLstatement execution
CVE-2012-0392struts2 DevMod Remote Command Execution Vulnerability
CVE-2011-3923Struts
CVE-2013-1966Struts2
CVE-2013-2251Struts2
Struts2
Struts2
CNVD-2016-02506, CVE-2016-3081, affected versions Struts 2.3.20 - StrutsStruts 2.3.28 (2.3 .20.3 and 2.3.24.3 except)
CVE number: CVE-2016-4438 Struts (S2-037) remote code execution vulnerability, affected version: Struts 2.3.20 - Struts Struts 2.3.28.1
CVE-2017-5638 Affected versions: Struts 2.3.5 – Struts 2.3.31
Struts 2.5 –Struts 2.5.10
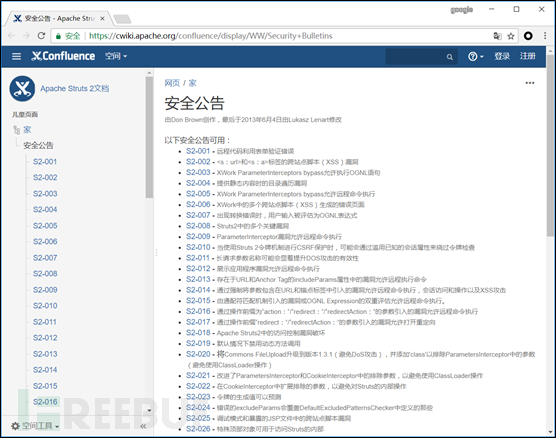
For other details, please refer to the struts2 official website Vulnerability history:
https://cwiki.apache.org/confluence/display/WW/Security Bulletins
3 . Distribution
In view of the Struts2 framework with frequent vulnerabilities, we conducted a survey and statistics on the distribution of the Struts framework in the province. By fingerprinting the sites of individual cities, we mapped out the use of the Strust2 framework in various cities in the province. The distribution chart is as follows:
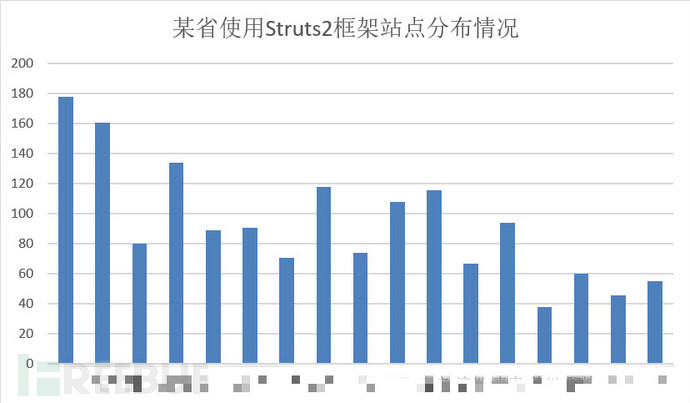
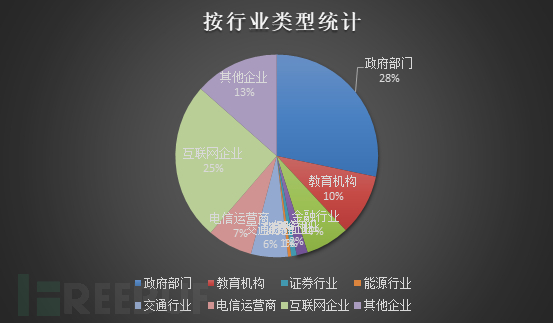
Specific table data:
| ##Serial number | Industry type | Quantity | Percentage |
| Government Department | 447 | 28.29% | |
| Educational Institution | 155 | 9.80% | |
| Financial Industry | 110 | 6.96% | |
| Insurance Industry | 28 | 1.77% | |
| Securities Industry | 14 | 0.88% | |
| Energy Industry | 8 | 0.50% | |
| Transportation Industry | 93 | 5.88% | |
| Telecom operator | 114 | 7.21% | |
| Internet enterprise | 398 | 25.18% | |
| Other companies | 213 | 13.48 % |
We conduct vulnerability detection on the collected sites using Struts2 middleware. This time, we use several high-risk vulnerabilities that have a relatively large impact on the Internet to verify and detect vulnerabilities (S2-045, S2-037, S2-032, S2-016). After testing 1580 site samples, it was found that there are still some sites where Struts2 vulnerabilities have not been repaired. The statistics of the sites with detected vulnerabilities are as follows:
| Number of vulnerabilities | ||
|---|---|---|
| 3 | 2 | |
| 2 | ##3 | |
| 1 | 4 | |
| 2 | 5 | |
| 2 | During the detection, we found that many websites had old vulnerabilities before Stuts2 that had not been repaired. Therefore, among the Stuts2 vulnerabilities, registered users of the website were nakedly exposed to hacker attacks. |
As the situation becomes increasingly complex, information security has become an issue that involves more than just technology. The development of science and technology is a double-edged sword. It can benefit mankind, but it can also have destructive effects. And this point, in addition to the technology itself, may be more grasped from the level of our consciousness. Faced with the huge impact of vulnerabilities, it is enough to alert information security practitioners in the Internet industry: a wake-up call for information security. , should be kept ringing all the time.
1. We should develop good development habits in information system development. Most loopholes exist from the development stage. Due to negligence during the development process, logical loopholes, etc. will also bring great harm to the system. Security Risk.
2. Back up the website data in a timely manner. When the system is attacked, the attacked system can be restored as soon as possible.
3. Install anti-virus software on the background service, conduct virus scans on the server regularly, and wait for security checks.
4. Pay attention to the latest Internet vulnerabilities in real time and repair the vulnerabilities in the information system in a timely manner.
5. Regularly conduct penetration testing, vulnerability testing and other work on the system to promptly discover problems and repair them in a timely manner to prevent vulnerabilities from being exposed on the Internet.
6. Take systems that are no longer in use offline in a timely manner. Generally, there are more security issues in old systems, and poor management may leak a large amount of sensitive information.
The above is the detailed content of Example analysis of Struts2 framework site risks. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
1. Introduction The Struts2 vulnerability is a classic series of vulnerabilities. The root cause is that Struts2 introduces OGNL expressions to make the framework flexible and dynamic. With the patching of the overall framework improved, it will now be much more difficult to discover new Struts2 vulnerabilities than before. Judging from the actual situation, most users have already repaired historical high-risk vulnerabilities. Currently, when doing penetration testing, Struts2 vulnerabilities are mainly left to chance, or it will be more effective to attack unpatched systems after being exposed to the intranet. Online analysis articles mainly analyze these Struts2 vulnerabilities from the perspective of attack and exploitation. As the new H3C offense and defense team, part of our job is to maintain the rule base of ips products. Today we will review this system.
 What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
The principle of the Struts2 framework: 1. The interceptor parses the request path; 2. Finds the complete class name of the Action; 3. Creates the Action object; 4. Execute the Action method; 5. Returns the result; 6. View parsing. Its principle is based on the interceptor mechanism, which completely separates the business logic controller from the Servlet API, improving the reusability and maintainability of the code. By using the reflection mechanism, the Struts2 framework can flexibly create and manage Action objects to process requests and responses.
 Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Vulhub vulnerability series: struts2 vulnerability S2-0011. Vulnerability description: struts2 vulnerability S2-001 is when the user submits form data and verification fails, the server uses OGNL expression to parse the parameter value previously submitted by the user, %{value} and refills the corresponding form data. For example, in a registration or login page. If the submission fails, the server will usually default to returning the previously submitted data. Since the server uses %{value} to perform OGNL expression parsing on the submitted data, the server can directly send the payload to execute the command. 2. Vulhub vulnerability exploitation: Using vulhub to reproduce vulnerabilities can save the environment construction process, which is very convenient. vu
 How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
0x00 Introduction Struts2 is a very powerful JavaWeb open source framework launched by the Apache software organization, which is essentially equivalent to a servlet. Struts2 is based on MVC architecture and has a clear framework structure. It is usually used as a controller to establish data interaction between models and views, and is used to create enterprise-level Java web applications. It utilizes and extends the JavaServletAPI and encourages developers to adopt the MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. 0x01 vulnerability
 Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Foreword On August 22, 2018, Apache Strust2 released the latest security bulletin. Apache Struts2 has a high-risk remote code execution vulnerability (S2-057/CVE-2018-11776). The vulnerability was discovered by ManYueMo, a security researcher from the SemmleSecurityResearch team. This vulnerability is due to the fact that when using the namespace function to define XML configuration in the Struts2 development framework, the namespace value is not set and is not set in the upper-layer action configuration (ActionConfiguration) or a wildcard namespace is used, which may lead to remote code execution. In the same way, u
 How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
0x00 Introduction The Struts2 framework is an open source web application architecture for developing JavaEE web applications. It utilizes and extends JavaServletAPI and encourages developers to adopt MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. Overview of the 0x01 vulnerability. The ApacheStruts22.3.x series has the struts2-struts1-plugin plug-in enabled and the struts2-showcase directory exists. The cause of the vulnerability is when ActionMe
 Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
1. Overview Struts is an open source project sponsored by the Apache Software Foundation (ASF). It started as a sub-project within the Jakarta project and later became a top-level project of ASF. By using JavaServlet/JSP technology, it implements the application framework [WebFramework] based on the Model-View-Controller [MVC] design pattern of JavaEE Web applications. It is a classic product in the MVC classic design pattern. In the early days of the development of JavaEE web applications, in addition to using Servlet technology, HTM was generally used in the source code of JavaServerPages (JSP).
 CNNVD report example analysis on Apache Struts2 S2-057 security vulnerability
May 11, 2023 pm 08:04 PM
CNNVD report example analysis on Apache Struts2 S2-057 security vulnerability
May 11, 2023 pm 08:04 PM
Currently, Apache has officially released a version update to fix the vulnerability. It is recommended that users confirm the Apache Struts product version in time. If affected, please take timely patching measures. 1. Vulnerability introduction ApacheStruts2 is a sub-project of the Jakarta project under the American Apache Software Foundation. It is a Web application framework based on MVC design. On August 22, 2018, Apache officially released the Apache Struts2S2-057 security vulnerability (CNNVD-201808-740, CVE-2018-11776). When enabling the pan-namespace function in the struts2 development framework




