AI voice cloning creates security vulnerability
According to McAfee (McAfee), AI technology is driving a surge in the number of online voice scams, and it only takes as little as three seconds of audio to clone the victim's voice.

McAfee surveyed 7,054 people from seven countries and found that one in four adults had experienced some kind of In the form of AI voice fraud, 10% of people said they had been defrauded, and 15% said someone they knew had been defrauded. 77% of victims claimed to have lost money as a result.
In addition, security researchers from McAfee Research Labs have drawn the following important conclusions after in-depth research on AI voice cloning technology and its use by cybercriminals.
Scammers use AI technology to clone voices
Everyone’s voice is unique, equivalent to a biometric fingerprint, which is why listening Speaking to someone is a widely accepted way of establishing trust.
But 53% of adults share voice data online at least once a week (through channels such as social media and voicemail), and 49% share it up to 10 times a week , cloning someone’s voice is now one of the most powerful tools in a cybercriminal’s arsenal.
As artificial intelligence tools rapidly proliferate and develop, it is easier than ever for criminals to manipulate the images, videos, and voices of friends and family (the latter is perhaps the most disturbing).
McAfee’s research shows that scammers are now using AI technology to clone voices and then send fake voicemails or call victims’ address book contacts to pretend they are in trouble. 70% of adults say it is difficult to distinguish cloned voices from real voices. No wonder this technology is becoming more and more popular among criminals.
45% of respondents said they would respond to a scam voicemail or voice note pretending to be from a friend or family member, especially if the voicemail came from their partner or spouse (40%) , parents (31%) or children (20%).
Victims of AI voice fraud have suffered heavy losses
Parents over the age of 50 are the group most likely to respond to their children’s voices, proportion Reached 41%. Messages most likely to be responded to are those claiming to have been in a car accident (48%), been robbed (47%), lost their phone or wallet (43%) or need help while traveling abroad (41%).
But if victims fall for AI voice fraud, they often face heavy losses. More than one-third of victims claimed to have lost more than $1,000, and 7% were defrauded out of $5,000 to $15,000.
The survey also found that the rise of deepfakes and disinformation has led to people becoming more wary of what they see online, with 32% of adults saying they are now less trusting than ever social media.
McAfee Chief Technology Officer Steve Grobman said: "Artificial intelligence presents incredible opportunities, but as with any technology, there is always the possibility that this technology will fall into the wrong hands. In the hands of criminals, they are then abused. This is what we are seeing today, as easy-to-use AI tools help cybercriminals scale fraud in increasingly realistic ways."
voicecloninggetseasier
As part of McAfee’s effort to analyze and evaluate this new trend, McAfee researchers spent three weeks investigating the accessibility of AI voice cloning tools , ease of use and effectiveness, his team found more than a dozen free AI voice cloning tools online.
Free and paid tools are readily available, and many require only basic experience and expertise to use. For one tool, just three seconds of speech was enough to generate a clone that matched 85% of the time. Accuracy could be further improved if criminals put in more effort.
By training the data model, McAfee researchers achieved a 95% speech match using only a small number of audio files.
The more accurate the cloned voice is, the more likely it is that cybercriminals can trick victims into handing over money or taking other requested actions. Because these scams exploit the emotional vulnerability inherent in human intimacy, scammers can make thousands of dollars in just a few hours.
The evolution of voice cloning technology
Grobman said: “Advanced artificial intelligence tools are changing the rules of the game for cybercriminals. Now, they With almost no effort, it is possible to clone someone's voice and trick friends and family into sending money."
Grobman concluded: "The important thing is to remain vigilant and take proactive measures. to keep you and your friends and family safe. If you receive a call from a spouse or family member in need asking to send money, be sure to verify the caller’s true identity—use a previously agreed-upon password, or ask a code that only the other person knows. issues. Identity and privacy protection services will also help limit the digital footprint of personal information, which criminals can use to craft compelling stories when cloning voices."
McAfee researchers used the cloning tool they discovered and found that it was easy to clone accents from around the world, whether the victim was from the United States, the United Kingdom, India or Australia, but more unique accents were more difficult to clone. For example, the voices of people who speak at an unusual speed, rhythm or style will take more effort to accurately clone and are therefore less likely to be targeted.
However, the research team generally believes that artificial intelligence has changed the rules of the game for cybercriminals. The barrier to entry has never been lower, which means committing cybercrime has never been easier.
AI voice cloning prevention tips
Agree on the voice password. Set a verbal code word with your children, family members or close friends that only they know. Make a plan that requires them to always provide a code word when calling, texting, or emailing for help, especially if they are older adults or children.
Always question the source. If it’s a call, text, or email from an unknown sender, or even a call from someone you know, you should think calmly when you receive a distress call: Does this really sound like their voice? Will they ask you this? Hang up the phone, answer the caller, or try to verify the authenticity of the message before responding (and of course before sending money).
Click and share with caution. Who is in your social media network? Do you really know and trust them? Be aware of your friends and contacts online. The wider your network and the more content you share, the greater the risk of your identity being maliciously cloned.
Use identity monitoring services to help ensure that your personally identifiable information cannot be accessed or exposed if your private information ends up on the dark web. Stay in control of your personal data and avoid being impersonated by cybercriminals.
The above is the detailed content of AI voice cloning creates security vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
This site reported on June 27 that Jianying is a video editing software developed by FaceMeng Technology, a subsidiary of ByteDance. It relies on the Douyin platform and basically produces short video content for users of the platform. It is compatible with iOS, Android, and Windows. , MacOS and other operating systems. Jianying officially announced the upgrade of its membership system and launched a new SVIP, which includes a variety of AI black technologies, such as intelligent translation, intelligent highlighting, intelligent packaging, digital human synthesis, etc. In terms of price, the monthly fee for clipping SVIP is 79 yuan, the annual fee is 599 yuan (note on this site: equivalent to 49.9 yuan per month), the continuous monthly subscription is 59 yuan per month, and the continuous annual subscription is 499 yuan per year (equivalent to 41.6 yuan per month) . In addition, the cut official also stated that in order to improve the user experience, those who have subscribed to the original VIP
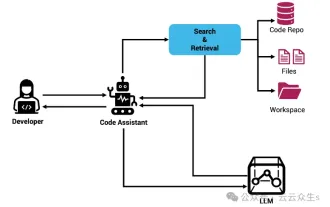 Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Improve developer productivity, efficiency, and accuracy by incorporating retrieval-enhanced generation and semantic memory into AI coding assistants. Translated from EnhancingAICodingAssistantswithContextUsingRAGandSEM-RAG, author JanakiramMSV. While basic AI programming assistants are naturally helpful, they often fail to provide the most relevant and correct code suggestions because they rely on a general understanding of the software language and the most common patterns of writing software. The code generated by these coding assistants is suitable for solving the problems they are responsible for solving, but often does not conform to the coding standards, conventions and styles of the individual teams. This often results in suggestions that need to be modified or refined in order for the code to be accepted into the application
 Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Large Language Models (LLMs) are trained on huge text databases, where they acquire large amounts of real-world knowledge. This knowledge is embedded into their parameters and can then be used when needed. The knowledge of these models is "reified" at the end of training. At the end of pre-training, the model actually stops learning. Align or fine-tune the model to learn how to leverage this knowledge and respond more naturally to user questions. But sometimes model knowledge is not enough, and although the model can access external content through RAG, it is considered beneficial to adapt the model to new domains through fine-tuning. This fine-tuning is performed using input from human annotators or other LLM creations, where the model encounters additional real-world knowledge and integrates it
 Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
To learn more about AIGC, please visit: 51CTOAI.x Community https://www.51cto.com/aigc/Translator|Jingyan Reviewer|Chonglou is different from the traditional question bank that can be seen everywhere on the Internet. These questions It requires thinking outside the box. Large Language Models (LLMs) are increasingly important in the fields of data science, generative artificial intelligence (GenAI), and artificial intelligence. These complex algorithms enhance human skills and drive efficiency and innovation in many industries, becoming the key for companies to remain competitive. LLM has a wide range of applications. It can be used in fields such as natural language processing, text generation, speech recognition and recommendation systems. By learning from large amounts of data, LLM is able to generate text
 Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Machine learning is an important branch of artificial intelligence that gives computers the ability to learn from data and improve their capabilities without being explicitly programmed. Machine learning has a wide range of applications in various fields, from image recognition and natural language processing to recommendation systems and fraud detection, and it is changing the way we live. There are many different methods and theories in the field of machine learning, among which the five most influential methods are called the "Five Schools of Machine Learning". The five major schools are the symbolic school, the connectionist school, the evolutionary school, the Bayesian school and the analogy school. 1. Symbolism, also known as symbolism, emphasizes the use of symbols for logical reasoning and expression of knowledge. This school of thought believes that learning is a process of reverse deduction, through existing
 To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
Editor |ScienceAI Question Answering (QA) data set plays a vital role in promoting natural language processing (NLP) research. High-quality QA data sets can not only be used to fine-tune models, but also effectively evaluate the capabilities of large language models (LLM), especially the ability to understand and reason about scientific knowledge. Although there are currently many scientific QA data sets covering medicine, chemistry, biology and other fields, these data sets still have some shortcomings. First, the data form is relatively simple, most of which are multiple-choice questions. They are easy to evaluate, but limit the model's answer selection range and cannot fully test the model's ability to answer scientific questions. In contrast, open-ended Q&A
 SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
Editor | KX In the field of drug research and development, accurately and effectively predicting the binding affinity of proteins and ligands is crucial for drug screening and optimization. However, current studies do not take into account the important role of molecular surface information in protein-ligand interactions. Based on this, researchers from Xiamen University proposed a novel multi-modal feature extraction (MFE) framework, which for the first time combines information on protein surface, 3D structure and sequence, and uses a cross-attention mechanism to compare different modalities. feature alignment. Experimental results demonstrate that this method achieves state-of-the-art performance in predicting protein-ligand binding affinities. Furthermore, ablation studies demonstrate the effectiveness and necessity of protein surface information and multimodal feature alignment within this framework. Related research begins with "S
 SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
According to news from this site on August 1, SK Hynix released a blog post today (August 1), announcing that it will attend the Global Semiconductor Memory Summit FMS2024 to be held in Santa Clara, California, USA from August 6 to 8, showcasing many new technologies. generation product. Introduction to the Future Memory and Storage Summit (FutureMemoryandStorage), formerly the Flash Memory Summit (FlashMemorySummit) mainly for NAND suppliers, in the context of increasing attention to artificial intelligence technology, this year was renamed the Future Memory and Storage Summit (FutureMemoryandStorage) to invite DRAM and storage vendors and many more players. New product SK hynix launched last year




