When AI encounters fraud
“Although I know that scams are common nowadays, I still can’t believe that I have actually encountered one. The experience of being scammed by telecommunications a few days ago still frightened reader Wu Jia (pseudonym). Among the scams Wu Jia encountered, The scammer used AI to change her face into someone she knew well.
Not only did Wu Jia encounter AI fraud that was difficult to guard against in her daily life, a reporter from Beijing Business Daily noticed that new telecommunications fraud models using AI technology have recently shown a high incidence. “The success rate of AI fraud is close to 100%. Topics such as "Technology company owner was defrauded of 4.3 million yuan in 10 minutes" have been on the hot searches one after another, which has also triggered discussions among users on the application of new technologies.

“AI face-changing” fraud
Artificial intelligence is popular again, this time around telecommunications fraud. Wu Jia told a Beijing Business Daily reporter that a social account that he had not used for a long time suddenly received greetings from a high school "friend" whom he had not contacted for many years. At first, he did not become suspicious. But after a brief exchange of pleasantries, the other party asked for an emergency loan of 2,000 yuan. Although a little confused, Wu Jia did not refuse immediately because of the familiar relationship in the past, but asked to verify his identity through voice and video.
"First she sent me a few voice messages, which sounded normal and more like her voice. Then I made a video call and she quickly connected. It was indeed her face." Wu Jia express. According to Wu Jia's recollection, due to frequent network lags, the conversation between the two was not smooth after the video call was connected. The other party only excused himself by saying that the network was not good, and also made remarks such as "You don't even recognize my face."
Wu Jia became wary because the other party did not explain in detail why he needed to borrow money. He just hung up the phone in a hurry after confirming his "face" and behaved abnormally. Later, Wu Jia asked the other party on the phone the surname of their common high school teacher, but the other party did not answer directly and still insisted that "I am who I am." After realizing that he might have encountered a scam, Wu Jia hung up the video call and further used other channels to seek help from the classmate, but received a reply that the borrower was not him.
Wu Jia feels very sad about this scam. Wu Jia said that although he knew that there were many methods of telecommunications fraud, he did not expect that the video verification method might not work. Later, I reminded the elders in my family that they could easily be defrauded if they encountered the same situation, so I emphasized to them again not to randomly trade funds through online channels. ”
Based on Wu Jia’s feedback, it is inferred that what she encountered was an AI fraud that has attracted much attention recently. On May 22, topics such as “The boss of a technology company was defrauded of 4.3 million yuan in 10 minutes”, “AI fraud success rate is close to 100%”, “AI fraud broke out in many places across the country”, etc., and many police officers also released AI Technology-related telecommunications fraud cases.
Information released by the Anti-Fraud Center of the Wenzhou Municipal Public Security Bureau on May 22 showed, "I think you will not treat me badly. Contact me as soon as you receive the text message picture." Mr. Chen, a Wenzhou citizen, received a message The blackmail text message came from a "private detective" and attached a screenshot of a so-called indecent video of Mr. Chen and a woman, but the related video was synthesized by AI. Mr. Chen called the police for help. The case is currently under investigation.
Coincidentally, Ping An Baotou’s official WeChat account disclosed on May 20 that the Telecommunications Cybercrime Investigation Bureau of Baotou City Public Security Bureau recently detected a case of telecom fraud using intelligent AI technology. Mr. Guo, the legal representative of a technology company in Fuzhou City, received a call from his friend WeChat video call, after confirming the friend's face and voice through the video, Mr. Guo transferred 4.3 million yuan to the other party's account within 10 minutes. It was not until he contacted his friend after transferring the money that Mr. Guo realized that he had been cheated. With the assistance of the Baotou police, 3.3684 million yuan of defrauded funds in the fraudulent account were finally intercepted, but a further 931,600 yuan was transferred away.
Su Xiaorui, a senior consultant in the financial industry of Analysys Analysis, said that as the application of AI technology gradually matures and the application threshold is lowered, using AI to commit fraud by pretending to be real has become a new trend for criminals.
Excessive disclosure of personal privacy
In fact, in recent years, combating telecommunications fraud has become a key task for regulators. Through online and offline channels such as the police, banks, communities, and media, detailed early warnings and disclosures of various telecommunications fraud methods have been carried out. However, Telecommunications frauds that come in all kinds of ways are still hard to guard against.
However, under multiple warnings, users are increasingly becoming more vigilant against telecom fraud. In this discussion on the topic of AI fraud, many users also raised the point of protecting personal privacy information and not taking anything involving money lightly.
Wang Pengbo, chief analyst of Broadcom Consulting, also believes that the advancement of technology has made it more difficult to prevent telecom fraud, but the reason for the frequent occurrence of telecom fraud is still the excessive leakage of users' personal privacy information in the information age. Beijing Business Daily reporters also asked many readers. One user who had encountered a return scam on an e-commerce platform pointed out that the scammer clearly provided his account name, purchased products and harvesting address on the phone, which ultimately caused his own large losses.
In an era of comprehensive advancement of digitalization, personal information is commonly collected by various platforms, which provides opportunities for the rise of a new model of AI fraud. When fraud meets AI, the success rate of fraud is close to 100%. Su Xiaorui pointed out that new technologies, including AI, should be neutral in themselves. While they can bring convenience to production and life, they also need to be alert to the various risks hidden in them.
The impact on face-swiping and palm-swiping payments
According to the content of the police report, the methods of using AI technology to commit fraud mainly include voice synthesis, AI face-changing, and stealing WeChat IDs, extracting voice files or installing unofficial versions (plug-ins), and forwarding previous messages to WeChat friends. Voice recordings gain trust. After careful screening, AI technology can be used to identify defrauded people and find target targets.
Compared with traditional fraud methods, AI fraud involves biometric information such as faces and voiceprints. In the digital age, biometric information such as fingerprints, voiceprints, faces and even irises have become the "keys" that can open financial accounts. This also means that in addition to conventional verification codes and ID number information, current users must protect their privacy. Information also increasingly includes personal biometric information.
According to past actual investigations by Beijing Business Daily reporters, especially in the financial field, the emergence of new technologies and new things can easily become leverage for scammers to carry out scams on unsuspecting users. After the AI "face-swapping" fraud method came out, many users also expressed concerns about the security of facial recognition and other methods, and asked whether scammers might use AI technology to steal personal financial accounts.
While AI fraud has been widely discussed, WeChat has also officially released a new payment method called palm payment. When discussing palm payment, some users also mentioned issues regarding palm print information collection and payment security. According to reports, unlike fingerprint recognition, which uses the epidermal lines of the fingertips, palmprint recognition uses the veins of the palm of the hand for identification.
While enjoying the convenience brought by new technologies, institutions should think about how to deal with problems such as fraud caused by new technologies. Talking about the application of new technologies in the financial field, Wang Pengbo pointed out that if an institution wants to implement new technologies, it must achieve a balance between how to protect personal privacy, anti-fraud and ease of use for users, and at least prepare prevention and response mechanisms in advance.
"Take palm payment as an example. The large-scale collection and application of personal information actually lacks legal support. How to avoid excessive collection of information and how to prevent personal biometric information that should be top-secret from being leaked? How to store data, and what method must be used to ensure the security of personal information before it can be retrieved... There is currently no good explanation for these issues. Wang Pengbo said that as the majority of users gradually accept personal privacy protection, new technologies must be popularized for individuals. The difficulty for users has become higher.
Cross verification before transfer
For consumers, it is more important to keep their "money bags" safe. In this regard, Wang Pengbo said that consumers must first be more vigilant. When it comes to transfers, they need to carefully verify the authenticity of the information and promptly contact relevant sources through formal channels for cross-verification.
Su Xiaorui pointed out that it needs to be viewed from three levels: First, on the regulatory side, risk reminders and early warnings need to be issued to the public in a timely manner, the introduction of scientific and technological talents should be further strengthened in the law enforcement team, and new methods of new electronic fraud should be summarized and refined. characteristics and new models, by setting up a number of major and important cases to shock the market; second, on the platform side, such as shopping platforms, social platforms, payment platforms, etc. where scammers are resident and frequently used, it is necessary to strengthen risk control management and take reasonable interception measures , promptly issue reminders to users when the account is abnormal or the chat content is abnormal; third, on the user side, do not trust unknown calls and text messages, and verify the identity information of the other party through official and other channels before transferring or making payment.
Beijing Business Daily reporter Liao Meng
The above is the detailed content of When AI encounters fraud. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Read CSV files and perform data analysis using pandas
Jan 09, 2024 am 09:26 AM
Read CSV files and perform data analysis using pandas
Jan 09, 2024 am 09:26 AM
Pandas is a powerful data analysis tool that can easily read and process various types of data files. Among them, CSV files are one of the most common and commonly used data file formats. This article will introduce how to use Pandas to read CSV files and perform data analysis, and provide specific code examples. 1. Import the necessary libraries First, we need to import the Pandas library and other related libraries that may be needed, as shown below: importpandasaspd 2. Read the CSV file using Pan
 Introduction to data analysis methods
Jan 08, 2024 am 10:22 AM
Introduction to data analysis methods
Jan 08, 2024 am 10:22 AM
Common data analysis methods: 1. Comparative analysis method; 2. Structural analysis method; 3. Cross analysis method; 4. Trend analysis method; 5. Cause and effect analysis method; 6. Association analysis method; 7. Cluster analysis method; 8 , Principal component analysis method; 9. Scatter analysis method; 10. Matrix analysis method. Detailed introduction: 1. Comparative analysis method: Comparative analysis of two or more data to find the differences and patterns; 2. Structural analysis method: A method of comparative analysis between each part of the whole and the whole. ; 3. Cross analysis method, etc.
 How to build a fast data analysis application using React and Google BigQuery
Sep 26, 2023 pm 06:12 PM
How to build a fast data analysis application using React and Google BigQuery
Sep 26, 2023 pm 06:12 PM
How to use React and Google BigQuery to build fast data analysis applications Introduction: In today's era of information explosion, data analysis has become an indispensable link in various industries. Among them, building fast and efficient data analysis applications has become the goal pursued by many companies and individuals. This article will introduce how to use React and Google BigQuery to build a fast data analysis application, and provide detailed code examples. 1. Overview React is a tool for building
 11 basic distributions that data scientists use 95% of the time
Dec 15, 2023 am 08:21 AM
11 basic distributions that data scientists use 95% of the time
Dec 15, 2023 am 08:21 AM
Following the last inventory of "11 Basic Charts Data Scientists Use 95% of the Time", today we will bring you 11 basic distributions that data scientists use 95% of the time. Mastering these distributions helps us understand the nature of the data more deeply and make more accurate inferences and predictions during data analysis and decision-making. 1. Normal Distribution Normal Distribution, also known as Gaussian Distribution, is a continuous probability distribution. It has a symmetrical bell-shaped curve with the mean (μ) as the center and the standard deviation (σ) as the width. The normal distribution has important application value in many fields such as statistics, probability theory, and engineering.
 11 Advanced Visualizations for Data Analysis and Machine Learning
Oct 25, 2023 am 08:13 AM
11 Advanced Visualizations for Data Analysis and Machine Learning
Oct 25, 2023 am 08:13 AM
Visualization is a powerful tool for communicating complex data patterns and relationships in an intuitive and understandable way. They play a vital role in data analysis, providing insights that are often difficult to discern from raw data or traditional numerical representations. Visualization is crucial for understanding complex data patterns and relationships, and we will introduce the 11 most important and must-know charts that help reveal the information in the data and make complex data more understandable and meaningful. 1. KSPlotKSPlot is used to evaluate distribution differences. The core idea is to measure the maximum distance between the cumulative distribution functions (CDF) of two distributions. The smaller the maximum distance, the more likely they belong to the same distribution. Therefore, it is mainly interpreted as a "system" for determining distribution differences.
 Machine learning and data analysis using Go language
Nov 30, 2023 am 08:44 AM
Machine learning and data analysis using Go language
Nov 30, 2023 am 08:44 AM
In today's intelligent society, machine learning and data analysis are indispensable tools that can help people better understand and utilize large amounts of data. In these fields, Go language has also become a programming language that has attracted much attention. Its speed and efficiency make it the choice of many programmers. This article introduces how to use Go language for machine learning and data analysis. 1. The ecosystem of machine learning Go language is not as rich as Python and R. However, as more and more people start to use it, some machine learning libraries and frameworks
 How to use ECharts and php interfaces to implement data analysis and prediction of statistical charts
Dec 17, 2023 am 10:26 AM
How to use ECharts and php interfaces to implement data analysis and prediction of statistical charts
Dec 17, 2023 am 10:26 AM
How to use ECharts and PHP interfaces to implement data analysis and prediction of statistical charts. Data analysis and prediction play an important role in various fields. They can help us understand the trends and patterns of data and provide references for future decisions. ECharts is an open source data visualization library that provides rich and flexible chart components that can dynamically load and process data by using the PHP interface. This article will introduce the implementation method of statistical chart data analysis and prediction based on ECharts and php interface, and provide
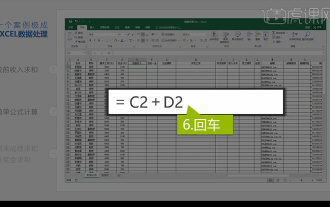 Integrated Excel data analysis
Mar 21, 2024 am 08:21 AM
Integrated Excel data analysis
Mar 21, 2024 am 08:21 AM
1. In this lesson, we will explain integrated Excel data analysis. We will complete it through a case. Open the course material and click on cell E2 to enter the formula. 2. We then select cell E53 to calculate all the following data. 3. Then we click on cell F2, and then we enter the formula to calculate it. Similarly, dragging down can calculate the value we want. 4. We select cell G2, click the Data tab, click Data Validation, select and confirm. 5. Let’s use the same method to automatically fill in the cells below that need to be calculated. 6. Next, we calculate the actual wages and select cell H2 to enter the formula. 7. Then we click on the value drop-down menu to click on other numbers.




