 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range
How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range
How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range
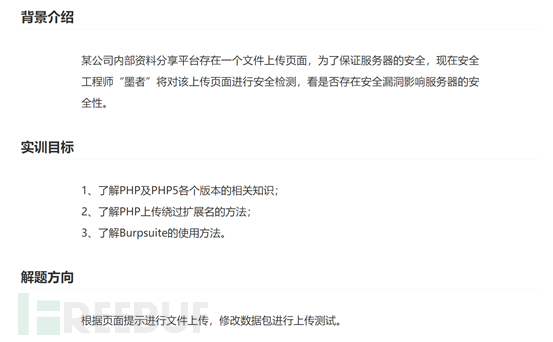
1. After opening the URL, I found that it is an upload page
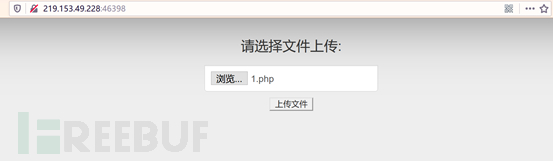
2. Directly upload the file with the suffix php and found that Unable to upload
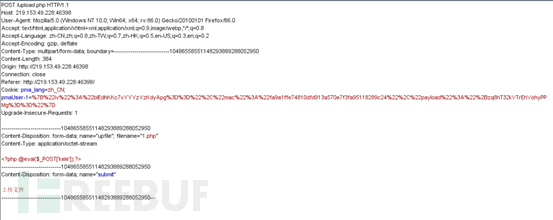
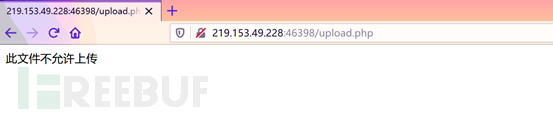
3. Use BurpSuite to capture packets and change the suffix of the uploaded file with the suffix php to php5. Bypass
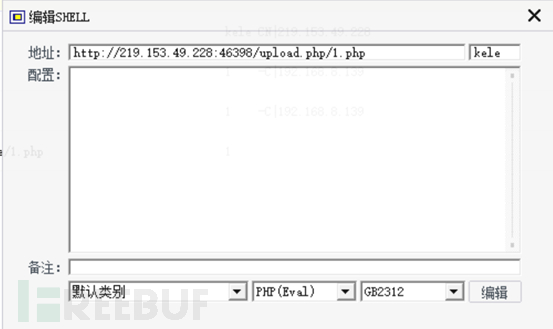
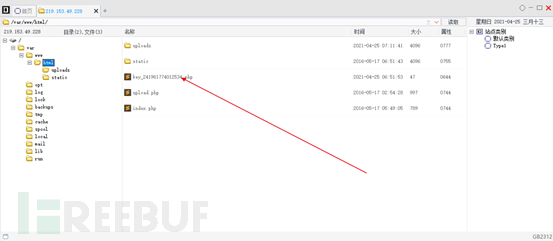
#4. Use a kitchen knife to connect. In the directory of var/www/html, a file with KEY is found. Open it and you will see the key
5. Open another URL, which is also an upload page, but the upload list is set to only allow files with the suffix .gif .jpg .png to pass through Upload
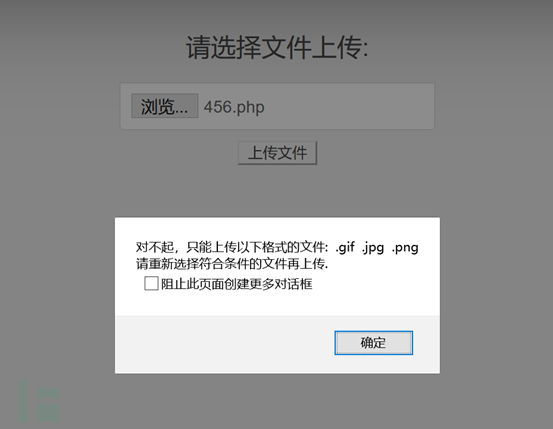
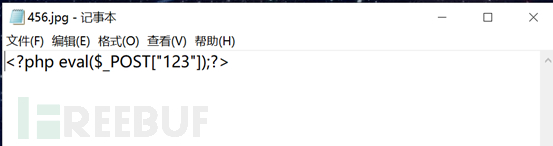
6. We write a txt one sentence Trojan and change its suffix to jpg
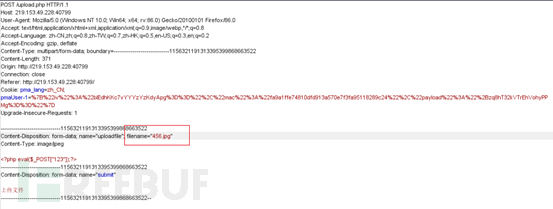
7. When uploading, use BurpSiuit to capture the packet and modify the file suffix to show that the upload was successful
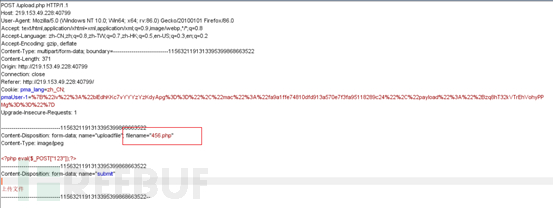
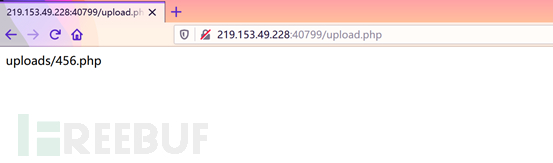
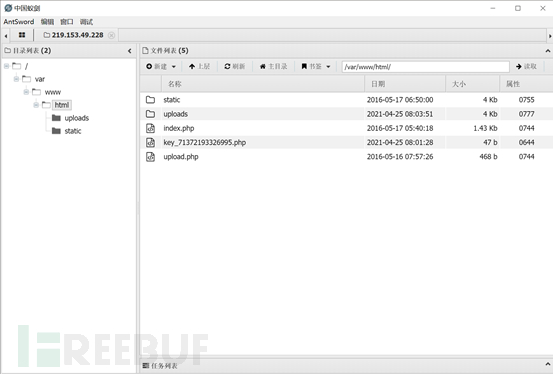 in var/www/html
in var/www/html
The above is the detailed content of How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 How to implement webshell upload under nginx load balancing
May 16, 2023 am 08:16 AM
How to implement webshell upload under nginx load balancing
May 16, 2023 am 08:16 AM
Scenario description assumes that in a real production environment, there is an RCE vulnerability, which allows us to obtain the installation of the WebShell environment. First, before pulling the vulnerable image on GetHub, we need to install nginx and tomcat on centos in advance and configure nginx and tomcat. Configuration file, use docker to pull down the image, and reproduce the vulnerability. 1. Set up the docker environment first. 2. Test whether tomcat can be accessed. As can be seen from the above figure, the back-end tomcat is accessible. 3. Check the load balancing of nginx reverse proxy in docker. 4. Check the ant in lbsnode1 in docker. .jsp text
 How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range
Jun 01, 2023 am 08:55 AM
How to analyze and trace the source of WebShell file upload vulnerability in Mozhe Shooting Range
Jun 01, 2023 am 08:55 AM
1. After opening the URL, it was found that it was an upload page. 2. Directly uploaded the file with the suffix php, but found that it could not be uploaded. 3. Use BurpSuite to capture the packet, and change the suffix of the uploaded file with the suffix php to php5 to bypass it. After 4. Use a kitchen knife to connect. In the directory of var/www/html, a file with KEY is found. Open it and you will see key5. Open another URL, which is also an upload page, but the upload list is set. Only Allow files with the suffix .gif.jpg.png to be uploaded through 6. We write a txt one-sentence Trojan and change its suffix to jpg7. When uploading, use BurpSiuit to capture the packet and modify the file suffix to display
 WebShell security settings of Pagoda panel
Jun 21, 2023 pm 04:35 PM
WebShell security settings of Pagoda panel
Jun 21, 2023 pm 04:35 PM
As Internet security issues become increasingly prominent, the security of major websites and applications has become an increasingly important issue. Especially in website operation and maintenance management, tools such as WebShell are often needed for maintenance and repair. However, WebShell is also often used by hackers and becomes an entry point for attackers to invade. This article will introduce the WebShell security settings of the Pagoda Panel to help website administrators improve the security of the site. 1. The concept and common uses of WebShell 1. Concept WebShell is
 A brief discussion on the Webshell of the Empire CMS framework
Mar 16, 2021 am 10:48 AM
A brief discussion on the Webshell of the Empire CMS framework
Mar 16, 2021 am 10:48 AM
This article introduces you to the Webshell of the Empire CMS framework. It has certain reference value. Friends in need can refer to it. I hope it will be helpful to everyone.
 What is the performance analysis of WAF on WebShell traffic detection?
May 16, 2023 pm 07:47 PM
What is the performance analysis of WAF on WebShell traffic detection?
May 16, 2023 pm 07:47 PM
Local environment setup Judging from the retained screenshots, the other party's PHP version is 5.6.40, so I want to set up a test environment of apache+php5.6.40. Open virtualbox, copy the link to the centos image system, and configure it according to the following process. 1.Install apacheyuminstall-yhttpdhttpd-vServerversion:Apache/2.4.6(CentOS)Serverbuilt:Aug8201911:41:182.Install php5.6yum-yinstallepel-releaserpm-Uvhhttps://mi
 Website vulnerability repair: Example analysis of uploading webshell vulnerability patching
May 30, 2023 pm 01:49 PM
Website vulnerability repair: Example analysis of uploading webshell vulnerability patching
May 30, 2023 pm 01:49 PM
SINE Security was conducting website vulnerability detection and repair on a customer's website and found that the website had serious SQL injection vulnerabilities and uploaded webshell website Trojan file vulnerabilities. The website used a CMS system, developed using PHP language, and the MySQL database architecture. The source code of this website is currently open source. A certain CMS is a social CMS system that focuses on providing paid knowledge. Payment for knowledge is in high demand on the current Internet. This system can share documents and download them for a fee. The knowledge content published by users can be hidden and provided to paying customers. read. The code is relatively streamlined and is well liked by the majority of webmasters. The vulnerability of this website mainly occurs when uploading the compressed package and constructing malicious decompression code to refer to the w in the zip package.
 What is the webshell analysis of obfuscated deformation?
May 19, 2023 pm 11:07 PM
What is the webshell analysis of obfuscated deformation?
May 19, 2023 pm 11:07 PM
What is WebShell? In the beginning, Webshell was often used as the abbreviation of a type of script used by Web server administrators to remotely manage the server. Later, with the birth of some Webshell management tools, the process of obtaining Web permissions was greatly simplified, so it was gradually called a Web intrusion tool script. Webshell is different from vulnerabilities, but uses application vulnerabilities or server vulnerabilities (file upload vulnerabilities, file inclusion vulnerabilities, etc.) to upload script files to the server for subsequent exploitation. It belongs to the subsequent exploitation of penetration testing and the TA0002Execution (execution) stage of ATT&CK. Figure 1TA0002 reference source: https
 Example analysis of webshell uploaded traceability events
May 12, 2023 pm 02:43 PM
Example analysis of webshell uploaded traceability events
May 12, 2023 pm 02:43 PM
First of all, I understand that what I have to do is not to find where the uploaded location appears. I should log on to the server to perform webshel inspection and inspection to see if it has been invaded by others, whether there is a backdoor, etc. etc. Although the IP address reported is our company's IP address, if a few webshells are missed and uploaded successfully by others but not detected, what can we do if the server is invaded? So I went up to inspect the server, uploaded this webshell killing tool for killing, used netstat-anpt and iptables-L to determine whether there was a backdoor established, checked whether there was a mining program occupying the CPU, etc., I will not go into details here. . Fortunately, the server was not compromised, and then



