How to use Masscan, Nmap, and ELK to collect intranet assets
Installation
Install masscan
# yum install git gcc make libpcap-devel # git clone https://github.com/robertdavidgraham/masscan # cd masscan # make # cp bin/masscan /bin
Install the latest nmap 7.8
wget https://nmap.org/dist/nmap-7.80-1.x86_64.rpm rpm -ivh nmap-7.80-1.x86_64.rpm
Install es and kibana
docker run -d --name es -p 127.0.0.1:9201:9200 -p 9300:9300 -e ES_JAVA_OPTS="-Xms2G -Xmx2G" -e "discovery.type=single-node" docker.elastic.co/elasticsearch/elasticsearch-oss:7.1.1 docker run --name kibana -d -p 5601:5601 -e ELASTICSEARCH_HOSTS=http://127.0.0.1:9201 docker.elastic.co/kibana/kibana-oss:7.1.1
The general logic is,
1, use Masscan to do a host survival scan
2, then use Nmap to scan the surviving hosts above, export xml
3, format the xml, write it into es, and then kibana for visualization
Upload the code
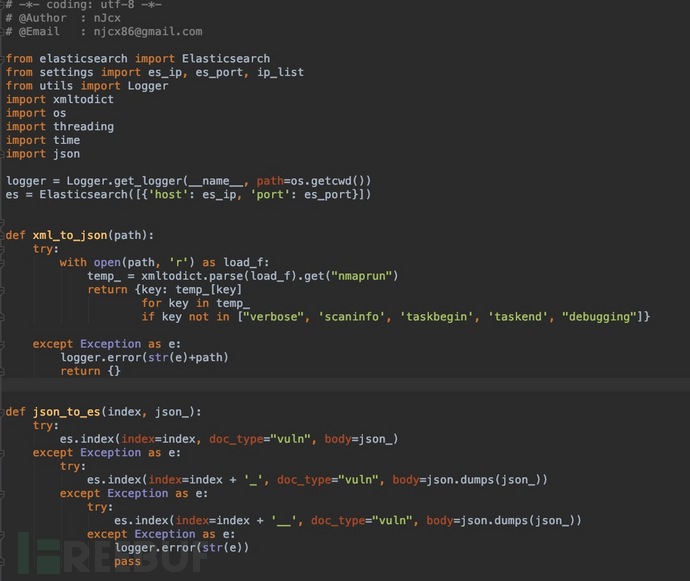
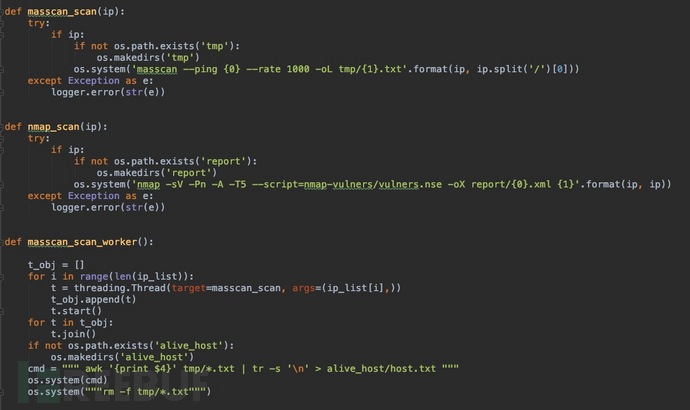
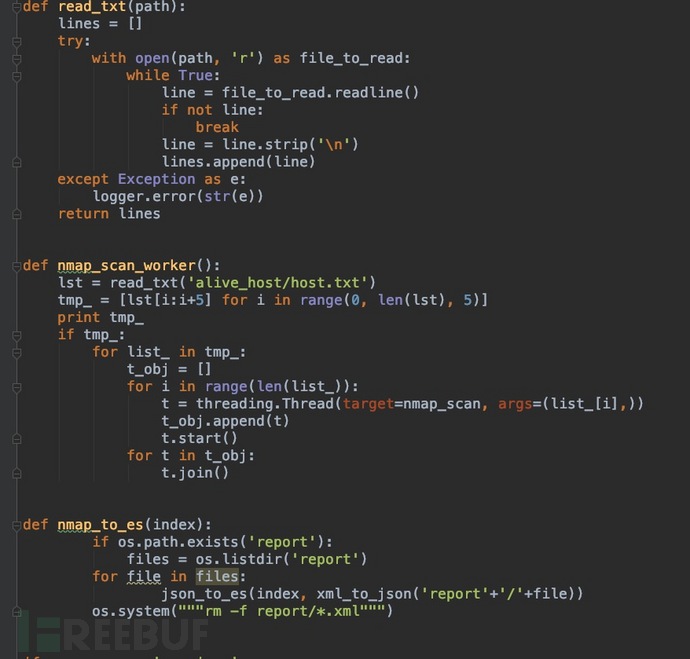
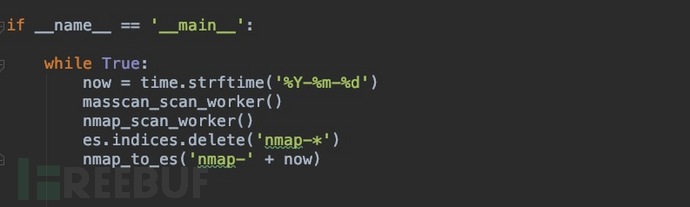 #
#
代码地址: https://github.com/njcx/nmap_to_es.git
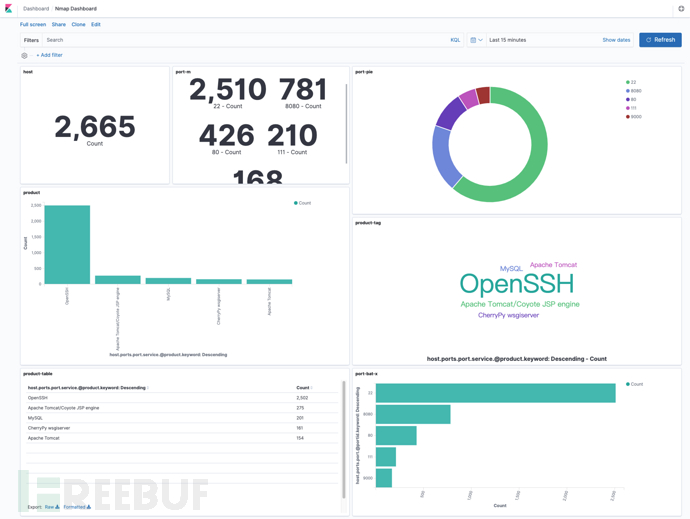
The above is the detailed content of How to use Masscan, Nmap, and ELK to collect intranet assets. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Example analysis of Nmap operations
May 17, 2023 pm 12:22 PM
Example analysis of Nmap operations
May 17, 2023 pm 12:22 PM
Background With the development of the security industry, the country attaches great importance to it. Various industries suffer from various threats. Some companies of Party A do not have relevant security departments or have relatively weak security capabilities, so they will hire Party B's security personnel to provide operational services. Then Party B's security engineers need to help customers deal with some security events that occur during business operations. For example, after a vulnerability occurs, our security engineers need to detect whether other business systems have the vulnerability and whether it needs to be repaired in time. We also need to output some results to facilitate customer reporting, as well as how to improve work efficiency, etc. Review of common parameter options for efficient scanning Fast live scanning nmap-T4-n-V–sn-iLip.txt-oNlive_host.
 what does elk mean
Dec 18, 2023 pm 02:11 PM
what does elk mean
Dec 18, 2023 pm 02:11 PM
ELK refers to the combination of three open source software: Elasticsearch, Logstash and Kibana. Detailed introduction: 1. Elasticsearch is a search server based on Lucene, providing a full-text search engine with distributed and multi-tenant capabilities; 2. Logstash is a powerful artifact flow tool for log collection, processing, conversion and delivery, which can be used for centralized Log management and log dump; 3. Kibana is a visual web application.
 How to use Masscan, Nmap, and ELK to collect intranet assets
Jun 03, 2023 pm 03:43 PM
How to use Masscan, Nmap, and ELK to collect intranet assets
Jun 03, 2023 pm 03:43 PM
Install install masscan#yuminstallgitgccmakelibpcap-devel#gitclonehttps://github.com/robertdavidgraham/masscan#cdmasscan#make#cpbin/masscan/bininstall the latest nmap7.8wgethttps://nmap.org/dist/nmap-7.80-1.x86_64 .rpmrpm-ivhnmap-7.80-1.x86_64.rpm install es and kibanadockerrun -d --namees-
 What is the nmap scan port command?
Jan 06, 2023 pm 02:29 PM
What is the nmap scan port command?
Jan 06, 2023 pm 02:29 PM
The nmap scan port command is "nmap -sU 202.96.128.86 -p 53 -Pn", where the parameter "-sU" indicates scanning the UDP port, and the parameter "-p 53" specifies the scanned port 53; through the results of the nmap scan, you can See whether the port is open or closed or whether there are other information reports, etc.
 How nmap hides itself from scanning
May 15, 2023 pm 09:22 PM
How nmap hides itself from scanning
May 15, 2023 pm 09:22 PM
192.168.1.216 is a zombie, 192.168.1.212 is the scanned end nmap-sn192.168.1.0/24 scans the online host nmap-Pn-sI192.168.1.216192.168.1.212 (-Pn hides itself, -sIidlescan) IDS can only detect When scanning 192.168.1.216 on 192.168.1.212, the scan of the nmap host cannot be detected.
 How to use Java to develop an ELK-based log management and analysis system
Sep 21, 2023 pm 04:57 PM
How to use Java to develop an ELK-based log management and analysis system
Sep 21, 2023 pm 04:57 PM
How to use Java to develop an ELK-based log management and analysis system. With the development and widespread application of information technology, system logs have become an indispensable part of every software system. During the running of the software, the system will generate a large amount of log information, which plays an important role in troubleshooting, performance optimization, security auditing, etc. Therefore, it is particularly important to develop an efficient and reliable log management and analysis system. ELK (Elasticsearch, Logstash, Kib
 How to use the network security audit tool Nmap
May 12, 2023 pm 03:34 PM
How to use the network security audit tool Nmap
May 12, 2023 pm 03:34 PM
1. Software download https://nmap.org/download.html 2. Scan IPnmap192.168.1.10#Scan single IPnmap192.168.1.10-100#Scan IP segment nmap192.168.1.10192.168.1.11#Scan single multiple IPnmap192 .168.1.1/24#Scan the entire network segment nmap-iLlist.txt#Scan according to the file list#list.txt192.168.1.20192.168.1.21nmap-iR3#Randomly scan 3 IPsnmap192.168.1.10-100--ex
 PHP implements open source ELK log analysis platform
Jun 18, 2023 pm 09:22 PM
PHP implements open source ELK log analysis platform
Jun 18, 2023 pm 09:22 PM
With the continuous development of the Internet and information technology, log analysis has become an indispensable part of enterprise business, network security and system optimization processes. In the past, log analysis methods mainly relied on manual reading, filtering and analysis, which was difficult for large amounts of data. The emergence of log analysis platforms can process log data efficiently and accurately, further increasing the value of the data. This article will introduce an open source ELK log analysis platform implemented using PHP. 1. Introduction to ELK ELK is Elasticsearch, L




