Nginx best practices in secure programming
Nginx is a reliable and efficient web server and reverse proxy server. It not only provides basic web service functions, but also supports advanced features such as load balancing, caching, and SSL encryption. In the process of web application development, secure programming is a crucial part. Next, we will analyze the best practices for using Nginx in secure programming to improve the security of web applications.
- Use the latest Nginx version
The first step to using Nginx safely is to make sure you are using the latest version. The Nginx community regularly releases new versions that fix security-related vulnerabilities and add new security features, so it is recommended to use the latest Nginx version at all times. - HTTPS
It is crucial to use HTTPS to encrypt and protect user data. You can enable HTTPS in Nginx, and Nginx supports basic SSL/TLS protocols and encryption protocols. You can use a self-signed certificate or purchase a public certificate to protect your website. Configuring HTTPS can also prevent data theft when using unsecured networks such as public wireless networks. - Preventing DDoS attacks
DDoS attacks are one of the common threats to web application security. Nginx supports features such as limiting client request speed and limiting the number of concurrent connections, which can effectively prevent these attacks. These settings can be achieved by adjusting the nginx.conf file:
client_body_timeout 10s;
client_header_timeout 10s;
send_timeout 10s;
connection_pool_size 256;
limit_conn_zone $binary_remote_addr zone= addr:10m;
limit_conn addr 100;
Use these settings to limit the client's request behavior while avoiding overloading the server.
- Prevent SQL Injection Attacks
When writing code that queries data from a web application to a database, it is important to take safe programming measures to avoid SQL injection attacks. You can enable the SQL injection prevention plug-in through Nginx configuration to effectively prevent this attack. I recommend using ModSecurity - this is a free firewall component that works with Nginx via the nginx-module-security module. - Distinguish between local and external requests
When the web application and the database are not on the same server, you should ensure that only the local machine can access the database. You can use Nginx to set up a reverse proxy server, which can only be accessed by this machine. - Limit upload file size
The security of web applications is often limited by the size of uploaded files. The size of uploaded files can be limited through Nginx configuration, which can effectively prevent attackers from uploading excessively large files to occupy server resources or perform other attacks.
client_max_body_size 10m;
client_body_buffer_size 128k;
- Hide server information
An attacker may obtain server information when using a web application. This will help them understand the vulnerabilities of web applications and exploit them for attacks. Server version information, including nginx version information, can be hidden in each request through Nginx configuration. An example is as follows:
server_tokens off;
Summary
The security of web applications is crucial. Not only do the above best practices help improve the security of your web applications, but using these practices can also improve your application's performance and scalability. Therefore, use Nginx best practices to build a robust and secure web application.
The above is the detailed content of Nginx best practices in secure programming. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1359
1359
 52
52
 What are the best practices for the golang framework?
Jun 01, 2024 am 10:30 AM
What are the best practices for the golang framework?
Jun 01, 2024 am 10:30 AM
When using Go frameworks, best practices include: Choose a lightweight framework such as Gin or Echo. Follow RESTful principles and use standard HTTP verbs and formats. Leverage middleware to simplify tasks such as authentication and logging. Handle errors correctly, using error types and meaningful messages. Write unit and integration tests to ensure the application is functioning properly.
 In-depth comparison: best practices between Java frameworks and other language frameworks
Jun 04, 2024 pm 07:51 PM
In-depth comparison: best practices between Java frameworks and other language frameworks
Jun 04, 2024 pm 07:51 PM
Java frameworks are suitable for projects where cross-platform, stability and scalability are crucial. For Java projects, Spring Framework is used for dependency injection and aspect-oriented programming, and best practices include using SpringBean and SpringBeanFactory. Hibernate is used for object-relational mapping, and best practice is to use HQL for complex queries. JakartaEE is used for enterprise application development, and the best practice is to use EJB for distributed business logic.
 How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
To successfully deploy and maintain a PHP website, you need to perform the following steps: Select a web server (such as Apache or Nginx) Install PHP Create a database and connect PHP Upload code to the server Set up domain name and DNS Monitoring website maintenance steps include updating PHP and web servers, and backing up the website , monitor error logs and update content.
 How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
An important task for Linux administrators is to protect the server from illegal attacks or access. By default, Linux systems come with well-configured firewalls, such as iptables, Uncomplicated Firewall (UFW), ConfigServerSecurityFirewall (CSF), etc., which can prevent a variety of attacks. Any machine connected to the Internet is a potential target for malicious attacks. There is a tool called Fail2Ban that can be used to mitigate illegal access on the server. What is Fail2Ban? Fail2Ban[1] is an intrusion prevention software that protects servers from brute force attacks. It is written in Python programming language
 Best practices for using C++ in IoT and embedded systems
Jun 02, 2024 am 09:39 AM
Best practices for using C++ in IoT and embedded systems
Jun 02, 2024 am 09:39 AM
Introduction to Best Practices for Using C++ in IoT and Embedded Systems C++ is a powerful language that is widely used in IoT and embedded systems. However, using C++ in these restricted environments requires following specific best practices to ensure performance and reliability. Memory management uses smart pointers: Smart pointers automatically manage memory to avoid memory leaks and dangling pointers. Consider using memory pools: Memory pools provide a more efficient way to allocate and free memory than standard malloc()/free(). Minimize memory allocation: In embedded systems, memory resources are limited. Reducing memory allocation can improve performance. Threads and multitasking use the RAII principle: RAII (resource acquisition is initialization) ensures that the object is released at the end of its life cycle.
 How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to Implement PHP Security Best Practices PHP is one of the most popular backend web programming languages used for creating dynamic and interactive websites. However, PHP code can be vulnerable to various security vulnerabilities. Implementing security best practices is critical to protecting your web applications from these threats. Input validation Input validation is a critical first step in validating user input and preventing malicious input such as SQL injection. PHP provides a variety of input validation functions, such as filter_var() and preg_match(). Example: $username=filter_var($_POST['username'],FILTER_SANIT
 Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
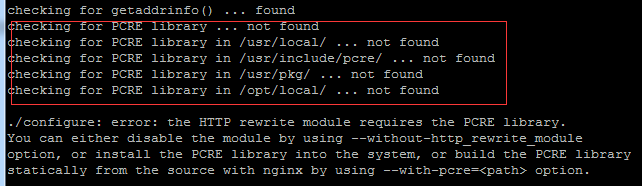
Today, I will lead you to install Nginx in a Linux environment. The Linux system used here is CentOS7.2. Prepare the installation tools 1. Download Nginx from the Nginx official website. The version used here is: 1.13.6.2. Upload the downloaded Nginx to Linux. Here, the /opt/nginx directory is used as an example. Run "tar-zxvfnginx-1.13.6.tar.gz" to decompress. 3. Switch to the /opt/nginx/nginx-1.13.6 directory and run ./configure for initial configuration. If the following prompt appears, it means that PCRE is not installed on the machine, and Nginx needs to
 What are the latest trends and best practices for Java functions?
Apr 29, 2024 pm 12:36 PM
What are the latest trends and best practices for Java functions?
Apr 29, 2024 pm 12:36 PM
The latest trends and best practices in functional Java include: lambda expressions: anonymous functions used to enhance code readability. Method reference: Concise syntax for referencing existing methods, instead of lambda expressions. Functional interface: An interface that contains only one abstract method, which can be implemented using lambda expressions or method references. Streaming API: used to process data collections, providing rich filtering, mapping and aggregation operations. Practical case: using Java functions in event processing, data processing and functional components.




