TPM installation and configuration steps
TPM installation and configuration steps
TPM (Trusted Platform Module) is a hardware security module used to encrypt and securely store keys, passwords and other sensitive information. It protects data and keys in computer systems from unauthorized access and theft. In this article, we will cover the installation and configuration steps of TPM.
Step One: Check whether your computer supports TPM
Before installing TPM, you need to determine whether your computer supports TPM. TPM usually needs to be enabled in the BIOS. To check whether your computer supports TPM, press the Win R key combination to open the run command box, enter "tpm.msc" and press Enter. If you see the "TPM Manager" window, it means your computer supports TPM.
Step 2: Purchase a TPM
If your computer does not have a built-in TPM, you need to purchase a TPM that matches your computer model. You can buy them at computer repair stores or electronic parts websites.
Step Three: TPM Installation
To install the TPM into the computer, you usually need to open the computer case and insert the TPM device into the designated slot on the motherboard. Some computers may require changing BIOS settings to have the TPM activated and recognized.
Step 4: Installation of TPM driver and software
TPM driver and software can be downloaded from the computer manufacturer's website. You need to download and install the drivers and software that match your TPM device model and operating system version.
Step Five: TPM Configuration
Once the TPM is recognized and the drivers and software are installed, you can begin configuring it. Before running "TPM Manager", make sure you have administrator rights. Then, press the Win R key combination to open the run command box, enter "tpm.msc" and press Enter to open the "TPM Manager".
In the TPM Manager, you can see an overview of the current TPM status. If the TPM is in the "Not Configured" state, you need to configure it first.
Before configuring TPM, please make sure that your computer has set a BIOS password. This is because the TPM protects your computer from unauthorized changes, but without a BIOS password, anyone can make unauthorized changes to your computer's BIOS settings, rendering your TPM unprotected.
Then, follow the steps in the TPM manager to configure the TPM. The configuration process may require the use of BIOS passwords and other security verification methods.
Step 6: Using TPM
Once the TPM is configured and enabled, you can start using it. TPM protects data and keys in a computer, such as password verification during computer startup or encryption during data storage and transmission.
It should be noted that if you reinstall the operating system or replace the hard drive, you may need to configure the TPM again. In addition, when the operating system is upgraded or the system is repaired, the TPM driver and software may need to be reinstalled.
In short, TPM is a hardware security module that can protect data and keys in a computer system. During the installation and configuration process, please make sure you have administrator rights and always pay attention to the security of your computer. Through the installation and configuration of TPM, you can protect your computer from unauthorized access and theft.
The above is the detailed content of TPM installation and configuration steps. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Solution to the problem that Win11 system cannot install Chinese language pack
Mar 09, 2024 am 09:48 AM
Solution to the problem that Win11 system cannot install Chinese language pack
Mar 09, 2024 am 09:48 AM
Solution to the problem that Win11 system cannot install Chinese language pack With the launch of Windows 11 system, many users began to upgrade their operating system to experience new functions and interfaces. However, some users found that they were unable to install the Chinese language pack after upgrading, which troubled their experience. In this article, we will discuss the reasons why Win11 system cannot install the Chinese language pack and provide some solutions to help users solve this problem. Cause Analysis First, let us analyze the inability of Win11 system to
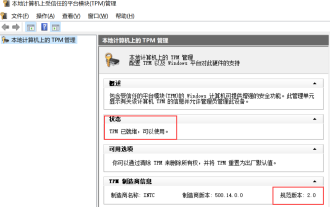 Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Recently, some Lenovo notebook partners have upgraded their systems to Win11. At this time, they need to check the computer to see if it supports TPM. If the computer supports TPM, it can be turned on in the motherboard BIOS. But how to enable the tpm function on Lenovo computers? Does it support opening? The following tutorial will introduce in detail the TPM activation of Lenovo notebooks. 1. Check whether TPM is supported 1. Right-click the start menu-Run (or press the Win+R keys on the keyboard), enter TPM.msc-press Enter. 2. As shown in the red box in the figure below, "TPM is ready for use" indicates that the machine supports TPM, and the version is version 2.0 shown in the red box below. 3. If
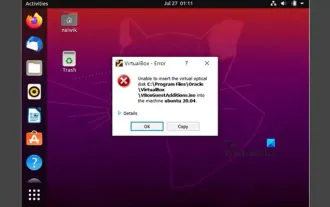 Unable to install guest additions in VirtualBox
Mar 10, 2024 am 09:34 AM
Unable to install guest additions in VirtualBox
Mar 10, 2024 am 09:34 AM
You may not be able to install guest additions to a virtual machine in OracleVirtualBox. When we click on Devices>InstallGuestAdditionsCDImage, it just throws an error as shown below: VirtualBox - Error: Unable to insert virtual disc C: Programming FilesOracleVirtualBoxVBoxGuestAdditions.iso into ubuntu machine In this post we will understand what happens when you What to do when you can't install guest additions in VirtualBox. Unable to install guest additions in VirtualBox If you can't install it in Virtua
 What should I do if Baidu Netdisk is downloaded successfully but cannot be installed?
Mar 13, 2024 pm 10:22 PM
What should I do if Baidu Netdisk is downloaded successfully but cannot be installed?
Mar 13, 2024 pm 10:22 PM
If you have successfully downloaded the installation file of Baidu Netdisk, but cannot install it normally, it may be that there is an error in the integrity of the software file or there is a problem with the residual files and registry entries. Let this site take care of it for users. Let’s introduce the analysis of the problem that Baidu Netdisk is successfully downloaded but cannot be installed. Analysis of the problem that Baidu Netdisk downloaded successfully but could not be installed 1. Check the integrity of the installation file: Make sure that the downloaded installation file is complete and not damaged. You can download it again, or try to download the installation file from another trusted source. 2. Turn off anti-virus software and firewall: Some anti-virus software or firewall programs may prevent the installation program from running properly. Try disabling or exiting the anti-virus software and firewall, then re-run the installation
 How to install Android apps on Linux?
Mar 19, 2024 am 11:15 AM
How to install Android apps on Linux?
Mar 19, 2024 am 11:15 AM
Installing Android applications on Linux has always been a concern for many users. Especially for Linux users who like to use Android applications, it is very important to master how to install Android applications on Linux systems. Although running Android applications directly on Linux is not as simple as on the Android platform, by using emulators or third-party tools, we can still happily enjoy Android applications on Linux. The following will introduce how to install Android applications on Linux systems.
 Understand Linux Bashrc: functions, configuration and usage
Mar 20, 2024 pm 03:30 PM
Understand Linux Bashrc: functions, configuration and usage
Mar 20, 2024 pm 03:30 PM
Understanding Linux Bashrc: Function, Configuration and Usage In Linux systems, Bashrc (BourneAgainShellruncommands) is a very important configuration file, which contains various commands and settings that are automatically run when the system starts. The Bashrc file is usually located in the user's home directory and is a hidden file. Its function is to customize the Bashshell environment for the user. 1. Bashrc function setting environment
 How to install Podman on Ubuntu 24.04
Mar 22, 2024 am 11:26 AM
How to install Podman on Ubuntu 24.04
Mar 22, 2024 am 11:26 AM
If you have used Docker, you must understand daemons, containers, and their functions. A daemon is a service that runs in the background when a container is already in use in any system. Podman is a free management tool for managing and creating containers without relying on any daemon such as Docker. Therefore, it has advantages in managing containers without the need for long-term backend services. Additionally, Podman does not require root-level permissions to be used. This guide discusses in detail how to install Podman on Ubuntu24. To update the system, we first need to update the system and open the Terminal shell of Ubuntu24. During both installation and upgrade processes, we need to use the command line. a simple
 How to Install and Run the Ubuntu Notes App on Ubuntu 24.04
Mar 22, 2024 pm 04:40 PM
How to Install and Run the Ubuntu Notes App on Ubuntu 24.04
Mar 22, 2024 pm 04:40 PM
While studying in high school, some students take very clear and accurate notes, taking more notes than others in the same class. For some, note-taking is a hobby, while for others, it is a necessity when they easily forget small information about anything important. Microsoft's NTFS application is particularly useful for students who wish to save important notes beyond regular lectures. In this article, we will describe the installation of Ubuntu applications on Ubuntu24. Updating the Ubuntu System Before installing the Ubuntu installer, on Ubuntu24 we need to ensure that the newly configured system has been updated. We can use the most famous "a" in Ubuntu system




