How to protect smartphones from hackers?
With the popularity of smartphones and the increasingly widespread use of network applications, mobile phone users use the Internet to process a large amount of sensitive information, including personal credit card information, personal contact information, social media accounts and email passwords, etc. Hackers are also constantly developing new technologies Attack techniques to invade and steal this information. Therefore, how to effectively protect your smartphone from hackers is very important.
One of the most common hacking methods is phishing, which involves tricking users into opening links disguised as legitimate websites or applications and then obtaining sensitive information such as login credentials and credit card information. Developers should try their best to avoid this attack method, especially when using website redirects and inline links in applications, they must ensure that their links are real and legal.
System updates are also one of the necessary means to prevent hacker attacks, because potential vulnerabilities in the firmware or operating system may be exploited by hackers. Updating systems can prevent future attacks by closing exposed vulnerabilities. If a mobile phone system or application upgrade prompts users to install updates, it is best not to delay and install updates promptly, as this may be the best way to deal with potential risks.
Passwords are an important means of protecting user privacy. When setting passwords, users should choose passwords that are difficult to crack, such as at least eight characters, uppercase and lowercase letters, numbers and special symbols, and do not reuse the same password. password. In addition, two-factor authentication methods such as fingerprint recognition and facial recognition should be enabled to ensure that the phone is more secure.
Another way hackers work is through custom-made malicious apps to carry out attacks on user devices. Be especially careful when downloading and using third-party apps, and only download apps from legitimate app stores and reliable developers, as these apps have been tested and verified many times to ensure that they do not compromise the security of the user’s phone and privacy.
You can also use anti-virus software, which has special code to protect the security of your phone. It can detect and scan malware, website links, viruses, etc. and directly block them, thereby protecting your phone from hackers and other Malware attacks.
To sum up, preventing hacker attacks requires multiple protection measures, such as correct passwords, two-factor authentication, complete system updates, caution when downloading applications, etc. Although hacker attacks are becoming increasingly difficult to deal with, if users can take the above precautions, they can reduce the risk of hacker attacks while maintaining privacy and information security.
The above is the detailed content of How to protect smartphones from hackers?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
Many friends who use win10 system find that there is a firewall logo on the icon on the computer desktop. What is going on? This makes many friends with obsessive-compulsive disorder particularly uncomfortable. In fact, we only need to open the control panel and click " It can be solved by changing "Change User Account Control Settings". Let's take a look at the specific tutorial. How to cancel the firewall logo on the desktop icon in Windows 10 1. First, right-click the Start menu button next to the computer startup screen, and then select the Control Panel function from the pop-up menu. 2. Then select the "User Account" option and select the "Change User Account Control Settings" item from the new interface that appears. 3. After adjusting the slider in the window to the bottom, click Confirm to exit.
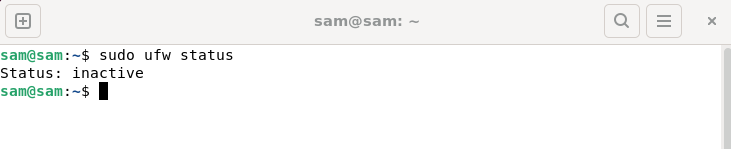 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
 How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve the problem that the Edge browser is blocked by the firewall? Edge browser is Microsoft's own browser. Some users found that this browser was blocked by the firewall during use. So what's going on? Let this site give users a detailed introduction on how to recover the Edge browser if it is blocked by the firewall. How to restore the Edge browser if it is blocked by the firewall? 1. Check the firewall settings: - Click the "Start" button on the Windows taskbar, and then open "Settings". -In the Settings window, select Update & Security. -exist
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Some friends want to protect their files, but don’t know how to encrypt win11 documents. In fact, we can directly use folder encryption or use third-party software to encrypt files. Detailed tutorial on win11 document encryption: 1. First find the file you want to encrypt, right-click to select it, and open "Properties" 2. Then click "Advanced" in the properties column 3. Select "Encrypt content to protect data" in Advanced and click " OK" 4. Then click "OK" to save. 5. Finally, select the desired encryption mode and "OK" to save the document to encrypt the document.




