 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 What are the key technologies and algorithms of trusted computing technology?
What are the key technologies and algorithms of trusted computing technology?
What are the key technologies and algorithms of trusted computing technology?
What are the key technologies and algorithms of trusted computing technology?
With the development of the Internet, various types of computers and network equipment have become increasingly popular, and people have higher and higher requirements for data security. Threats such as fraud attacks, privacy leaks, and network viruses continue to emerge, placing high demands on the security and credibility of computer systems. Trusted computing technology emerged as the times require. It is a method that combines hardware and software to protect and ensure the security and reliability of computer systems. So, what are the key technologies and algorithms of trusted computing technology?
1. Trusted Platform Module (TPM technology)
The Trusted Platform Module (TPM for short) is one of the core technologies of trusted computing. It is a hardware chip that is installed on the computer's motherboard and is difficult to modify and attack. Used to store security-related information, such as keys and digital certificates, to ensure system authentication, encryption, and authorization.
The main function of TPM technology is to provide functions such as system random number generation, boot password negotiation, authorization encryption and plug-in mechanism. Through these functions, TPM technology can provide security protection for the entire computer system to prevent unauthorized access and data leakage.
2. Two-way authentication (SSL/TLS technology)
Two-way authentication means that the client and the server verify each other's identities to ensure that the identities of the communicating parties are true. The implementation of two-way authentication requires the help of SSL/TLS technology, which is an important secure transmission protocol in trusted computing technology.
SSL/TLS technology realizes message encryption and integrity verification by using public key encryption and digital signature technology. It can encrypt and protect data during data transmission to ensure data security. At the same time, SSL/TLS technology can also prevent man-in-the-middle attacks and tampering, ensuring the authenticity and reliability of messages.
3. Encryption algorithm (AES/SM4 algorithm)
Encryption algorithm is an important part of trusted computing technology and the core implementation to ensure data security. Currently, AES and SM4 are two widely used encryption algorithms.
The AES algorithm is a symmetric cryptosystem that uses the same key for encryption and decryption. Therefore, it is fast and efficient and is one of the most widely used encryption algorithms currently. The SM4 algorithm is a high-security symmetric cryptographic algorithm with excellent performance, high speed and high efficiency. It is one of the cryptographic algorithms recommended by the State Cryptozoology Bureau.
4. Virtualization technology
Virtualization technology is an important technology in trusted computing technology. It can convert physical resources into virtual resources and flexibly allocate and allocate virtual resources. manage. Through virtualization technology, users can create multiple virtual machines to implement different application scenarios, and isolate, collaborate and manage them.
Virtualization technology can achieve isolation and protection at the hardware level, reduce the sharing and pollution of physical resources, and increase resource usage efficiency and reliability. At the same time, virtualization technology can also provide multi-level protection for virtual machines to ensure the security environment and data security of virtual machines.
To sum up, the key technologies and algorithms of trusted computing technology include trusted platform module (TPM technology), two-way authentication (SSL/TLS technology), encryption algorithm (AES/SM4 algorithm) and virtualization technology. These technologies and algorithms play a full role in practical applications to ensure the security and reliability of computer systems and improve the overall performance and efficiency of computer systems.
The above is the detailed content of What are the key technologies and algorithms of trusted computing technology?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1371
1371
 52
52
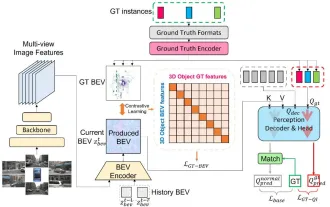 CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
Written above & the author’s personal understanding: At present, in the entire autonomous driving system, the perception module plays a vital role. The autonomous vehicle driving on the road can only obtain accurate perception results through the perception module. The downstream regulation and control module in the autonomous driving system makes timely and correct judgments and behavioral decisions. Currently, cars with autonomous driving functions are usually equipped with a variety of data information sensors including surround-view camera sensors, lidar sensors, and millimeter-wave radar sensors to collect information in different modalities to achieve accurate perception tasks. The BEV perception algorithm based on pure vision is favored by the industry because of its low hardware cost and easy deployment, and its output results can be easily applied to various downstream tasks.
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.
 Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
The convergence of artificial intelligence (AI) and law enforcement opens up new possibilities for crime prevention and detection. The predictive capabilities of artificial intelligence are widely used in systems such as CrimeGPT (Crime Prediction Technology) to predict criminal activities. This article explores the potential of artificial intelligence in crime prediction, its current applications, the challenges it faces, and the possible ethical implications of the technology. Artificial Intelligence and Crime Prediction: The Basics CrimeGPT uses machine learning algorithms to analyze large data sets, identifying patterns that can predict where and when crimes are likely to occur. These data sets include historical crime statistics, demographic information, economic indicators, weather patterns, and more. By identifying trends that human analysts might miss, artificial intelligence can empower law enforcement agencies
 Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
01 Outlook Summary Currently, it is difficult to achieve an appropriate balance between detection efficiency and detection results. We have developed an enhanced YOLOv5 algorithm for target detection in high-resolution optical remote sensing images, using multi-layer feature pyramids, multi-detection head strategies and hybrid attention modules to improve the effect of the target detection network in optical remote sensing images. According to the SIMD data set, the mAP of the new algorithm is 2.2% better than YOLOv5 and 8.48% better than YOLOX, achieving a better balance between detection results and speed. 02 Background & Motivation With the rapid development of remote sensing technology, high-resolution optical remote sensing images have been used to describe many objects on the earth’s surface, including aircraft, cars, buildings, etc. Object detection in the interpretation of remote sensing images
 Practice and reflections on Jiuzhang Yunji DataCanvas multi-modal large model platform
Oct 20, 2023 am 08:45 AM
Practice and reflections on Jiuzhang Yunji DataCanvas multi-modal large model platform
Oct 20, 2023 am 08:45 AM
1. The historical development of multi-modal large models. The photo above is the first artificial intelligence workshop held at Dartmouth College in the United States in 1956. This conference is also considered to have kicked off the development of artificial intelligence. Participants Mainly the pioneers of symbolic logic (except for the neurobiologist Peter Milner in the middle of the front row). However, this symbolic logic theory could not be realized for a long time, and even ushered in the first AI winter in the 1980s and 1990s. It was not until the recent implementation of large language models that we discovered that neural networks really carry this logical thinking. The work of neurobiologist Peter Milner inspired the subsequent development of artificial neural networks, and it was for this reason that he was invited to participate in this project.
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction
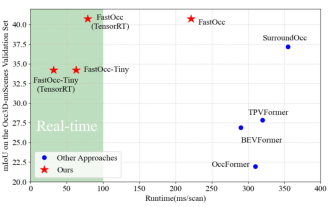 Add SOTA in real time and skyrocket! FastOcc: Faster inference and deployment-friendly Occ algorithm is here!
Mar 14, 2024 pm 11:50 PM
Add SOTA in real time and skyrocket! FastOcc: Faster inference and deployment-friendly Occ algorithm is here!
Mar 14, 2024 pm 11:50 PM
Written above & The author’s personal understanding is that in the autonomous driving system, the perception task is a crucial component of the entire autonomous driving system. The main goal of the perception task is to enable autonomous vehicles to understand and perceive surrounding environmental elements, such as vehicles driving on the road, pedestrians on the roadside, obstacles encountered during driving, traffic signs on the road, etc., thereby helping downstream modules Make correct and reasonable decisions and actions. A vehicle with self-driving capabilities is usually equipped with different types of information collection sensors, such as surround-view camera sensors, lidar sensors, millimeter-wave radar sensors, etc., to ensure that the self-driving vehicle can accurately perceive and understand surrounding environment elements. , enabling autonomous vehicles to make correct decisions during autonomous driving. Head



