What is Trusted Platform Module (TPM)?
Trusted Platform Module (TPM) is a security component that is usually embedded on computer or server hardware. It is a chip used to provide secure processing and storage of sensitive information, improving the security and trustworthiness of the device.
TPM is a hardware-implemented security solution that can be used to implement encryption, authentication, and authorization functions. It is a secure embedded chip that works with a computer’s central processing unit (CPU) and operating system (OS). A TPM can be thought of as a safe for storing data such as passwords, certificates, encryption keys, etc.
TPM is commonly used in corporate and government agency environments to increase security and protect confidential data. It protects the confidentiality, integrity and availability of a business's confidential information by preventing threats such as malware, hackers and unauthorized access.
TPM usually includes the following main components:
- Internal memory: used to store security code and data.
- RSA public key encryption engine: can be used to encrypt and decrypt data.
- True random number generator: used to generate high-quality random numbers.
- Authentication quantity generator: used to generate various certificates and authentication tokens.
- Key hierarchy: used to manage and store keys.
TPM can provide the following security features:
- Encryption: TPM can store encryption keys, thereby providing data encryption and decryption functions.
- Authentication: TPM can provide authentication functions, such as using digital certificates for identity verification.
- Tamper-proof: TPM can detect file and data tampering to ensure that it has not been maliciously changed.
- Copyright Protection: TPM prevents unauthorized access to protected content.
- Secure Boot: TPM ensures a secure boot, preventing the computer from being tampered with by malware.
In short, TPM is an important security solution used to protect data security and the credibility of computer systems. It can provide a variety of security functions such as encryption, authentication, tamper resistance, copyright protection, and secure boot, and is worthy of attention from all walks of life.
The above is the detailed content of What is Trusted Platform Module (TPM)?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1384
1384
 52
52
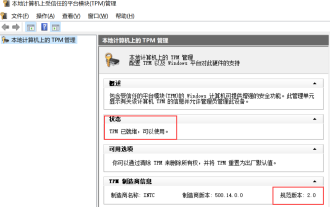 Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Recently, some Lenovo notebook partners have upgraded their systems to Win11. At this time, they need to check the computer to see if it supports TPM. If the computer supports TPM, it can be turned on in the motherboard BIOS. But how to enable the tpm function on Lenovo computers? Does it support opening? The following tutorial will introduce in detail the TPM activation of Lenovo notebooks. 1. Check whether TPM is supported 1. Right-click the start menu-Run (or press the Win+R keys on the keyboard), enter TPM.msc-press Enter. 2. As shown in the red box in the figure below, "TPM is ready for use" indicates that the machine supports TPM, and the version is version 2.0 shown in the red box below. 3. If
 How to Fix Valorant Vanguard Windows 11 Error
Apr 15, 2023 pm 08:55 PM
How to Fix Valorant Vanguard Windows 11 Error
Apr 15, 2023 pm 08:55 PM
These two Vanguard errors appear when players try to launch Valorant in Windows 11. Therefore, players cannot play Valorant due to these bugs. If you need to resolve one of these issues, check out the potential fixes below. What is Vanguard? Vanguard is anti-cheat software for the Valorant game. Riot software is installed with the game to prevent players from cheating in Valorant. You will not be able to play Valorant without the RiotVanguard software installed and activated. This software is somewhat controversial because it blocks applications. Players complain about Vanguard viz.
 Rufus 3.18 bypasses Windows 11 TPM restrictions for in-place upgrade, fixes ISO to ESP error
Apr 16, 2023 am 10:49 AM
Rufus 3.18 bypasses Windows 11 TPM restrictions for in-place upgrade, fixes ISO to ESP error
Apr 16, 2023 am 10:49 AM
The latest 3.18 pre-release (beta) version of popular bootable USB media creation software Rufus also adds the ability to bypass Windows 11 system requirements for in-place upgrades. Earlier, in the 3.16Beta2 version, Rufus had been given the option to bypass Windows 11's strict system requirements through the "Extended" installation feature. However, this option is only available for fresh installations. However, now with Rufus3.18, this feature is also available for in-place upgrades. The official changelog says: Added bypass for Windows 11 restrictions for in-place upgrades though we can’t say for sure, based on the latest AdDuplex numbers
 How to clear TPM in Windows 11: A step-by-step guide
May 04, 2023 pm 11:34 PM
How to clear TPM in Windows 11: A step-by-step guide
May 04, 2023 pm 11:34 PM
Starting with Windows 10 and Windows 11, TPMs are now initialized immediately and granted ownership by the operating system, making them more secure. This is in contrast to previous operating systems where you would initialize the TPM and generate the owner password before proceeding. Before proceeding to clear the TPM in Windows 11, make sure you have a backup and recovery solution set up for any data protected or encrypted by it. Although the TPM must be wiped before a new operating system can be installed, the vast majority of TPM functionality will likely continue to function normally after the TPM is cleared. There are several ways to clear Windows 11’s TPM chip
 Win11tpm2.0 opens MSI motherboard
Jan 07, 2024 pm 10:10 PM
Win11tpm2.0 opens MSI motherboard
Jan 07, 2024 pm 10:10 PM
The method of upgrading Win11 and enabling TPM2.0 varies between different motherboards, so many MSI motherboard users wonder how to enable their own motherboards. In fact, you only need to operate in the BIOS to turn on the MSI motherboard with win11tpm2.0: 1. Intel platform 1. First restart the computer and repeatedly press the "Delete" key on the keyboard to enter the BIOS settings. What you need to do is: 2. Enter the BIOS settings, press the "F7" key on the keyboard to open the advanced options. The content that needs to be rewritten is: 3. Click the "Security" button in the lower right corner again, and then select "Trusted Computing". After entering, change "SecurityDeviceSupport" Change the "TPM" option below to "Enable"
 Encryption and decryption technology in PHP
May 11, 2023 am 08:03 AM
Encryption and decryption technology in PHP
May 11, 2023 am 08:03 AM
PHP is a widely used web development language, and its encryption and decryption technology is of great significance in data security. This article will introduce encryption and decryption technology in PHP and explore its practical application in web applications. 1. Encryption technology Encryption technology is a process of converting ordinary text into encrypted text. In PHP, encryption technology is mainly used to ensure the security of transmitted data, such as user login information, transaction data, etc. Common encryption technologies in PHP are as follows: Hash encryption Hash encryption is to convert an arbitrary length
 How to disable TPM and Secure Boot in Rufus when creating a Windows 11 bootable USB drive
May 16, 2023 am 08:04 AM
How to disable TPM and Secure Boot in Rufus when creating a Windows 11 bootable USB drive
May 16, 2023 am 08:04 AM
Microsoft allows you to install Windows 11 via registry cracking, but that's not the only way to bypass required checks like TPM2.0, Secure Boot, and more. You can simply delete the appraiserres.dll file in the Windows 11 ISO file to make the installer avoid these checks and install Windows 11 on any unsupported hardware. This method requires you to edit the ISO file to remove the appraiserres.dll file, which is not difficult, but thanks to Rufus, you have an easier way to do this. Read on to learn how to disable Windows 11 requirements like TPM2
 Former SEC Crypto Assets Director Resigns! Refuting rumors about joining Meme coin issuance platform Pump.fun
Jun 18, 2024 pm 07:53 PM
Former SEC Crypto Assets Director Resigns! Refuting rumors about joining Meme coin issuance platform Pump.fun
Jun 18, 2024 pm 07:53 PM
Yesterday, rumors abounded that David Hirsch, the former head of crypto assets at the Securities and Exchange Commission (SEC), had resigned and was about to join the team of meme currency issuance platform Pump.fun. It is said that all the rumors started when Pump.fun posted a message on social media X A tweet with a mocking metaphor congratulated him on becoming the trading director of the team, and the relevant content was even forwarded by various media. Pump.fun's fake news is fake. Yesterday evening (17th), with the release of a tweet from Pump.fun, the meme currency issuance platform on Solana, rumors began about Hirsch, the former SEC cryptoassets and head of the network department, jumping ship to the Pump.fun platform. Spread the word. Binance tweets about Pump.fun




