How to implement confidential computation in TPM?
With the continuous development of cloud computing and the Internet of Things, confidential computing has become a hot topic. Although secure computing can protect data security during computing, its application is still limited by many limitations, one of which is the lack of security equipment and appropriate security equipment. This article will introduce how to implement confidential computing in TPM.
TPM, or Trusted Platform Module, is a hardware security device used to protect sensitive data and encryption keys stored on computers or other devices. The TPM contains a specialized chip that securely authenticates the computer to prevent unauthorized access and stores specific encryption keys and certificates to ensure secure communication between the computer and other devices.
The principle of confidential computing is to decompose the computing process into multiple parts, and then run these parts on different devices. During execution, only the final results will be sent over the network, and once the results are confirmed, all intermediate results will be destroyed to ensure the confidentiality of the results. This method effectively solves the security problem, but also increases the computational delay and communication cost.
In order to solve these problems, TPM is introduced into confidential computing. TPM can be regarded as a secure computing device that protects sensitive data and keys, prevents unauthorized access, and supports the acceleration and optimization of secure computing processes.
Using TPM to implement confidential computing requires the following steps:
The first step is to break down the computing task into multiple parts. These parts can be executed on different devices, or at different levels of protection on the same device. For example, TPM can be used to protect keys or sensitive data during computing.
The second step is to delegate the decomposed tasks to different computing devices for execution. These devices can be computing nodes with varying security levels, or specialized secure computing devices. A TPM can be viewed as a secure computing device that protects data and keys while supporting efficient computing processes.
The third step is to coordinate the execution of tasks to ensure safety and efficiency. To do this, a key agreement protocol is used to ensure that each device has access to the data and keys it needs. Additionally, provable encryption protocols are required to protect data integrity and confidentiality during communications.
The fourth step is to combine the results to ensure the correctness of the calculation. Since this article mainly focuses on how to implement confidential computation in TPM, this article will not go into depth on how to make the merge process more secure and reliable.
It should be noted that although TPM can provide advantages in security and efficiency, there are also some challenges in using TPM. For example, the TPM is a specialized device, which may cause cost issues. In addition, performing complex computing tasks on TPM requires some additional programming work and the development of corresponding software tools and applications.
In general, TPM is an important security device that can provide an infrastructure for confidential computing. Efficient and secure can be achieved by decomposing secure computing tasks into multiple parts, securely coordinating task execution across multiple devices, protecting the tasks' symmetric keys and sensitive data via TPMs, and using provable cryptographic protocols. Keep the calculation process confidential. Although using TPM may increase some programming work and equipment costs, it provides great help in the security protection of data and computing.
The above is the detailed content of How to implement confidential computation in TPM?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
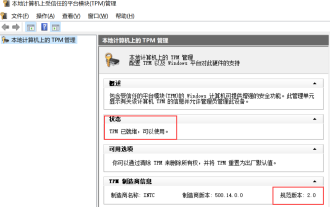 Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Check if Lenovo laptop supports TPM? How to turn on and off TPM on Lenovo laptop?
Mar 14, 2024 am 08:30 AM
Recently, some Lenovo notebook partners have upgraded their systems to Win11. At this time, they need to check the computer to see if it supports TPM. If the computer supports TPM, it can be turned on in the motherboard BIOS. But how to enable the tpm function on Lenovo computers? Does it support opening? The following tutorial will introduce in detail the TPM activation of Lenovo notebooks. 1. Check whether TPM is supported 1. Right-click the start menu-Run (or press the Win+R keys on the keyboard), enter TPM.msc-press Enter. 2. As shown in the red box in the figure below, "TPM is ready for use" indicates that the machine supports TPM, and the version is version 2.0 shown in the red box below. 3. If
 What is the way to implement polling in Android?
Sep 21, 2023 pm 08:33 PM
What is the way to implement polling in Android?
Sep 21, 2023 pm 08:33 PM
Polling in Android is a key technology that allows applications to retrieve and update information from a server or data source at regular intervals. By implementing polling, developers can ensure real-time data synchronization and provide the latest content to users. It involves sending regular requests to a server or data source and getting the latest information. Android provides multiple mechanisms such as timers, threads, and background services to complete polling efficiently. This enables developers to design responsive and dynamic applications that stay in sync with remote data sources. This article explores how to implement polling in Android. It covers the key considerations and steps involved in implementing this functionality. Polling The process of periodically checking for updates and retrieving data from a server or source is called polling in Android. pass
 Win11tpm2.0 opens MSI motherboard
Jan 07, 2024 pm 10:10 PM
Win11tpm2.0 opens MSI motherboard
Jan 07, 2024 pm 10:10 PM
The method of upgrading Win11 and enabling TPM2.0 varies between different motherboards, so many MSI motherboard users wonder how to enable their own motherboards. In fact, you only need to operate in the BIOS to turn on the MSI motherboard with win11tpm2.0: 1. Intel platform 1. First restart the computer and repeatedly press the "Delete" key on the keyboard to enter the BIOS settings. What you need to do is: 2. Enter the BIOS settings, press the "F7" key on the keyboard to open the advanced options. The content that needs to be rewritten is: 3. Click the "Security" button in the lower right corner again, and then select "Trusted Computing". After entering, change "SecurityDeviceSupport" Change the "TPM" option below to "Enable"
 How to implement image filter effects in PHP
Sep 13, 2023 am 11:31 AM
How to implement image filter effects in PHP
Sep 13, 2023 am 11:31 AM
How to implement PHP image filter effects requires specific code examples. Introduction: In the process of web development, image filter effects are often used to enhance the vividness and visual effects of images. The PHP language provides a series of functions and methods to achieve various picture filter effects. This article will introduce some commonly used picture filter effects and their implementation methods, and provide specific code examples. 1. Brightness adjustment Brightness adjustment is a common picture filter effect, which can change the lightness and darkness of the picture. By using imagefilte in PHP
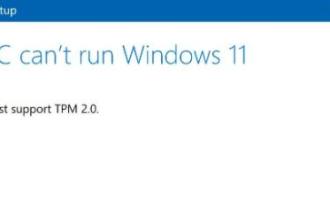 How to solve the problem that Win11 installation requires TPM2.0
Dec 26, 2023 pm 09:50 PM
How to solve the problem that Win11 installation requires TPM2.0
Dec 26, 2023 pm 09:50 PM
Many users have encountered problems titled "ThePCmustsupportTPM2.0" during the installation process of Windows 11 systems. We can successfully enable the TMP function in the BIOS settings interface or cleverly replace the corresponding files to bypass TPM detection. be resolved effectively! Let’s explore these solutions in depth together! What to do if win11 installation prompts tpm2.0? Method 1: 1. First restart the computer, restart the computer and use shortcut keys (hot keys) to enter the BIOS setting interface. 2. In this BIOS setting, look for TMP or CMOC related options and start them successfully. 2. Replace files 1. If in front of the BIOS setup interface
 How UniApp implements camera and video calls
Jul 04, 2023 pm 04:57 PM
How UniApp implements camera and video calls
Jul 04, 2023 pm 04:57 PM
UniApp is a cross-platform development framework developed based on HBuilder, which can enable one code to run on multiple platforms. This article will introduce how to implement camera and video call functions in UniApp, and give corresponding code examples. 1. Obtain the user's camera permissions In UniApp, we need to first obtain the user's camera permissions. In the mounted life cycle function of the page, use the authorize method of uni to call the camera permission. The code example is as follows: mounte
 How to implement the shortest path algorithm in C#
Sep 19, 2023 am 11:34 AM
How to implement the shortest path algorithm in C#
Sep 19, 2023 am 11:34 AM
How to implement the shortest path algorithm in C# requires specific code examples. The shortest path algorithm is an important algorithm in graph theory and is used to find the shortest path between two vertices in a graph. In this article, we will introduce how to use C# language to implement two classic shortest path algorithms: Dijkstra algorithm and Bellman-Ford algorithm. Dijkstra's algorithm is a widely used single-source shortest path algorithm. Its basic idea is to start from the starting vertex, gradually expand to other nodes, and update the discovered nodes.
 Introduction to the implementation methods and steps of PHP email verification login registration function
Aug 18, 2023 pm 10:09 PM
Introduction to the implementation methods and steps of PHP email verification login registration function
Aug 18, 2023 pm 10:09 PM
Introduction to the implementation methods and steps of the PHP email verification login registration function. With the rapid development of the Internet, user registration and login functions have become one of the necessary functions for almost all websites. In order to ensure user security and reduce spam registration, many websites use email verification for user registration and login. This article will introduce how to use PHP to implement the login and registration function of email verification, and come with code examples. Set up the database First, we need to set up a database to store user information. You can use MySQL or




