On the Necessity of Remote Security Control
With the continuous development of modern network technology, remote security control has become a necessity. Remote security control refers to the technology of remote control and management between computers and network devices in different locations. In the modern digital environment, remote security control will undoubtedly play an increasingly important role.
First of all, remote security control can improve work efficiency. Workers only need to remotely access their computers and network equipment through remote security control without having to travel to computer rooms and data centers. This not only improves work efficiency, but also reduces unnecessary time and costs, while enabling staff to respond quickly to work tasks when working remotely or traveling.
Secondly, under remote security control, data security can be better protected. Data security has always been an important concern for various enterprises and institutions. Different departments need to share data and information, but with this comes the risk of data leakage and loss. Through remote security control, it is possible to coordinate the equipment and facilities used by various departments and ensure strong implementation of data protection and privacy protection. This effectively ensures the security of important data and privacy, and avoids illegal use of data and unnecessary organizational losses.
Third, remote security control can reduce dependence on equipment. Remote security control can reduce dependence on different equipment and ensure the efficient operation of important equipment. For some enterprises and institutions, through remote security control, they can be freed from limitations such as system hardware, physical space, and operator location, and thus have better choices. Through remote security control, multiple devices can be easily controlled and managed remotely to improve device operation efficiency.
Finally, remote security control has a high degree of flexibility and personalized customization capabilities. Remote security controls can be customized and adapted to meet the requirements of different user groups. Through configuration and customization, users can make personalized settings according to actual needs and special needs, improving the intelligence, reliability and applicability of the remote security control system.
In general, the necessity of remote security control is that it can bring higher work efficiency, better data security, reduced dependence on devices, flexibility and personalization to businesses and organizations Customization features and many other advantages. With the continuous development of new technologies such as cloud computing and the Internet of Things, remote security control will have a wider application range and play a more important role. Therefore, remote security control must become an essential part of the modern digital environment.
The above is the detailed content of On the Necessity of Remote Security Control. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
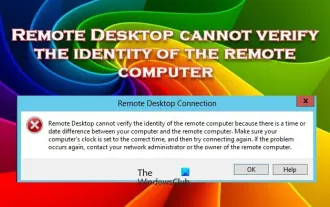 Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Windows Remote Desktop Service allows users to access computers remotely, which is very convenient for people who need to work remotely. However, problems can be encountered when users cannot connect to the remote computer or when Remote Desktop cannot authenticate the computer's identity. This may be caused by network connection issues or certificate verification failure. In this case, the user may need to check the network connection, ensure that the remote computer is online, and try to reconnect. Also, ensuring that the remote computer's authentication options are configured correctly is key to resolving the issue. Such problems with Windows Remote Desktop Services can usually be resolved by carefully checking and adjusting settings. Remote Desktop cannot verify the identity of the remote computer due to a time or date difference. Please make sure your calculations
 What is Intel TXT?
Jun 11, 2023 pm 06:57 PM
What is Intel TXT?
Jun 11, 2023 pm 06:57 PM
IntelTXT is a hardware-assisted security technology launched by Intel. It can ensure the integrity and security of the server during startup by establishing a protected space between the CPU and BIOS. The full name of TXT is TrustedExecutionTechnology, which is Trusted Execution Technology. Simply put, TXT is a security technology that provides hardware-level protection to ensure that the server has not been modified by malicious programs or unauthorized software when it is started. this one
 Using PHP to control the camera: analysis of the entire process from connection to shooting
Jul 30, 2023 pm 03:21 PM
Using PHP to control the camera: analysis of the entire process from connection to shooting
Jul 30, 2023 pm 03:21 PM
Use PHP to control the camera: Analyze the entire process from connection to shooting. Camera applications are becoming more and more widespread, such as video calls, surveillance systems, etc. In web applications, we often need to control and operate cameras through PHP. This article will introduce how to use PHP to realize the entire process from camera connection to shooting. Confirm the connection status of the camera. Before starting to operate the camera, we first need to confirm the connection status of the camera. PHP provides an extension library video to operate the camera. We can pass the following code
 BYD cooperates with Stingray to create a safe and enjoyable in-car entertainment space
Aug 11, 2023 pm 02:09 PM
BYD cooperates with Stingray to create a safe and enjoyable in-car entertainment space
Aug 11, 2023 pm 02:09 PM
BYD's official WeChat public account announced that BYD has reached a cooperation agreement with Stingray, a music media technology company, and plans to introduce Stingray interactive car KTV products in new energy vehicles from 2023 and promote them in multiple markets around the world. According to reports, BYD and Stingray The entertainment system jointly developed by Stingray will add more entertainment functions to BYD's new energy vehicles to meet the diverse needs of users. The entertainment system will support multiple languages and provide a user-friendly interface design, allowing users to easily search by song title, artist, lyrics or genre. In addition, the system will automatically update tracks every month, bringing users a new music experience. In order to ensure driving safety, when the vehicle is in driving mode,
 How to prevent HTTP response splitting attacks using PHP
Jun 24, 2023 am 10:40 AM
How to prevent HTTP response splitting attacks using PHP
Jun 24, 2023 am 10:40 AM
HTTP response splitting attack (HTTP response splitting attack) is a vulnerability that uses web applications to process HTTP responses. The attacker constructs a malicious HTTP response and injects malicious code into the legitimate response to achieve the purpose of attacking the user. As a commonly used web development language, PHP also faces the threat of HTTP response splitting attacks. This article will introduce how to use PHP to prevent HTTP response splitting attacks. Understanding HTTP response splitting attacks
![How to disable media volume control popups [permanently]](https://img.php.cn/upload/article/000/000/164/168493981948502.png?x-oss-process=image/resize,m_fill,h_207,w_330) How to disable media volume control popups [permanently]
May 24, 2023 pm 10:50 PM
How to disable media volume control popups [permanently]
May 24, 2023 pm 10:50 PM
When you use the corresponding shortcut key to fine-tune the volume level, a media volume control pop-up will appear on the screen. This can be annoying, so read on to find out different ways to permanently disable media volume control pop-ups. How to disable media volume control popup? 1. Click the Windows icon on the taskbar in Google Chrome, type chrome in the search bar at the top, and select the relevant search results to launch Google Chrome. Type or copy-paste the following into the address bar and press the key. Enterchrome://flags type media keys in the search box at the top and select Disable in the Hardware Media Key Handling drop-down list. Now exit the Google Chrome app and relaunch it. Google
 How to make a remote desktop connection display the other party's taskbar
Jan 03, 2024 pm 12:49 PM
How to make a remote desktop connection display the other party's taskbar
Jan 03, 2024 pm 12:49 PM
There are many users using Remote Desktop Connection. Many users will encounter some minor problems when using it, such as the other party's taskbar not being displayed. In fact, it is probably a problem with the other party's settings. Let's take a look at the solutions below. How to display the other party's taskbar during Remote Desktop Connection: 1. First, click "Settings". 2. Then open "Personalization". 3. Then select "Taskbar" on the left. 4. Turn off the Hide Taskbar option in the picture.
 How to implement robot control using Java
Jun 16, 2023 am 10:36 AM
How to implement robot control using Java
Jun 16, 2023 am 10:36 AM
In recent years, robotic technology has been widely used, which shows its importance in the field of science and technology. Robot control is also one of the core parts of robot development. Using Java language to realize robot control can achieve fast robot control and provide strong support for the further development of robots. Java is a high-level language that has become a widely used programming language due to its good cross-platform, efficiency and security. It also provides good support in implementing robot control. First of all, you need to understand the robot control






