 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Application of trusted computing technology in the field of environmental monitoring
Application of trusted computing technology in the field of environmental monitoring
Application of trusted computing technology in the field of environmental monitoring
As environmental problems continue to intensify, environmental monitoring has become an indispensable part of the environmental protection industry. However, traditional environmental monitoring technology faces many shortcomings, such as low data security, low reliability, etc. The emergence of trusted computing technology has brought more efficient, reliable and secure solutions to environmental monitoring.
Trusted computing technology is a security assurance technology based on hardware and software. It ensures the security, reliability and integrity of computer systems and data by establishing a trusted environment and recovery mechanism, thereby preventing malicious intent. Attacks and illegal access. The emergence of trusted computing technology makes data protection more reliable and provides more certain and reliable results for environmental monitoring.
In the field of environmental monitoring, the applications of trusted computing technology mainly include the following aspects.
First, the application of distributed environmental monitoring systems. Traditional environmental monitoring systems often face problems such as scattered data collection points and communication security, resulting in data tampering and loss. By introducing trusted computing technology, a distributed environment monitoring system can be established to increase data security and reliability. For example, in air quality monitoring, using trusted computing technology to upload data to the chain can ensure that the data is traced without being tampered with, improving the integrity and credibility of the monitoring data.
Second, the application of data encryption and decryption mechanisms based on trusted computing technology. A large amount of data generated in environmental monitoring may be controlled, stolen, tampered with, damaged, etc. during the processes of backup, transmission, and storage. Through the application of trusted computing technology, cryptography-based data encryption and decryption mechanisms can be strengthened to better protect data and ensure data security, integrity and confidentiality. For example, the encryption technology of X-ray films not only ensures the security of patient privacy data, but also provides technical support to experts from other hospitals. It also assists hospitals in actively promoting the use of CT platforms and promoting the rapid development of the medical industry.
Third, the application of trusted computing technology in the process of environmental monitoring data sharing. The data collected by environmental information can be shared to many different destinations. However, due to issues such as data security, data sharing often makes it difficult to control people's access to these data. Trusted computing technology can achieve access control and static data encryption protection in a safe and trusted environment, thereby improving the credibility and reuse rate of environmental data and protecting the interests of the environment and residents.
In short, the application of trusted computing technology in the field of environmental monitoring can not only improve the security and reliability of data, but also establish a shared security environment, providing strong support for the smooth advancement of environmental protection. As trusted computing technology continues to develop, we can expect it to make more contributions to the further development of environmental protection.
The above is the detailed content of Application of trusted computing technology in the field of environmental monitoring. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
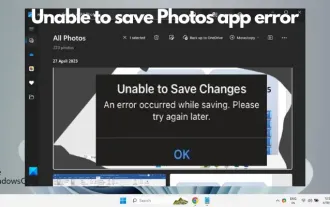 Unable to save changes to Photos app error in Windows 11
Mar 04, 2024 am 09:34 AM
Unable to save changes to Photos app error in Windows 11
Mar 04, 2024 am 09:34 AM
If you encounter the Unable to save changes error while using the Photos app for image editing in Windows 11, this article will provide you with solutions. Unable to save changes. An error occurred while saving. Please try again later. This problem usually occurs due to incorrect permission settings, file corruption, or system failure. So, we’ve done some deep research and compiled some of the most effective troubleshooting steps to help you resolve this issue and ensure you can continue to use the Microsoft Photos app seamlessly on your Windows 11 device. Fix Unable to Save Changes to Photos App Error in Windows 11 Many users have been talking about Microsoft Photos app error on different forums
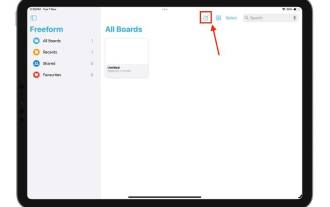 Learn how to use the Boundless Notes app on iPhone and iPad
Nov 18, 2023 pm 01:45 PM
Learn how to use the Boundless Notes app on iPhone and iPad
Nov 18, 2023 pm 01:45 PM
What is Boundless Notes on iPhone? Like the iOS17 Diary app, Boundless Notes is a productivity app with tons of creative potential. It’s a great place to turn ideas into reality. You can schedule projects, brainstorm ideas, or create mood boards so you never run out of space to express your ideas. The app allows you to add photos, videos, audios, documents, PDFs, web links, stickers, and more anywhere on an unlimited canvas. Many of the tools in Boundless Notes (like brushes, shapes, and more) will be familiar to anyone who uses iWork apps like Keynote or Notes. Real-time collaboration with colleagues, teammates, and group project members is also easy because Freeform allows
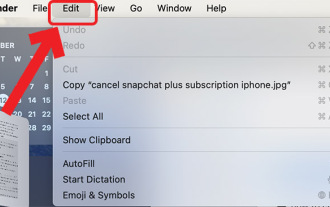 How to view clipboard history on Mac
Sep 14, 2023 pm 12:09 PM
How to view clipboard history on Mac
Sep 14, 2023 pm 12:09 PM
View macOS Clipboard History from Finder When you copy anything on your Mac (text, images, files, URLs, etc.), it goes to the Clipboard. Here's how to see what was last copied on your Mac. Go to Finder and click "Edit" in the menu bar. Click "Show Clipboard". This will open a window showing the contents of the macOS clipboard. Get Clipboard History Containing Multiple Items in Mac Of course, native Mac Clipboard History isn't the most versatile tool you can have. It only shows the last thing you copied, so if you want to copy multiple things at once and then paste them all together, you simply can't do that. However, if you are looking for
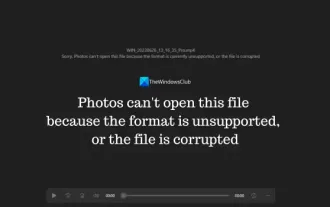 Photos cannot open this file because the format is not supported or the file is corrupted
Feb 22, 2024 am 09:49 AM
Photos cannot open this file because the format is not supported or the file is corrupted
Feb 22, 2024 am 09:49 AM
In Windows, the Photos app is a convenient way to view and manage photos and videos. Through this application, users can easily access their multimedia files without installing additional software. However, sometimes users may encounter some problems, such as encountering a "This file cannot be opened because the format is not supported" error message when using the Photos app, or file corruption when trying to open photos or videos. This situation can be confusing and inconvenient for users, requiring some investigation and fixes to resolve the issues. Users see the following error when they try to open photos or videos on the Photos app. Sorry, Photos cannot open this file because the format is not currently supported, or the file
 How to connect Apple Vision Pro to PC
Apr 08, 2024 pm 09:01 PM
How to connect Apple Vision Pro to PC
Apr 08, 2024 pm 09:01 PM
The Apple Vision Pro headset is not natively compatible with computers, so you must configure it to connect to a Windows computer. Since its launch, Apple Vision Pro has been a hit, and with its cutting-edge features and extensive operability, it's easy to see why. Although you can make some adjustments to it to suit your PC, and its functionality depends heavily on AppleOS, so its functionality will be limited. How do I connect AppleVisionPro to my computer? 1. Verify system requirements You need the latest version of Windows 11 (Custom PCs and Surface devices are not supported) Support 64-bit 2GHZ or faster fast processor High-performance GPU, most
 How to solve application startup error 0xc000012d problem
Jan 02, 2024 pm 12:53 PM
How to solve application startup error 0xc000012d problem
Jan 02, 2024 pm 12:53 PM
When a friend's computer is missing certain files, the application cannot start normally with error code 0xc000012d. In fact, it can be solved by re-downloading the files and installing them. The application cannot start normally 0xc000012d: 1. First, the user needs to download ".netframework". 2. Then find the download address and download it to your computer. 3. Then double-click on the desktop to start running. 4. After the installation is completed, return to the wrong program location and open the program again.
 MS Paint not working properly in Windows 11
Mar 09, 2024 am 09:52 AM
MS Paint not working properly in Windows 11
Mar 09, 2024 am 09:52 AM
Microsoft Paint not working in Windows 11/10? Well, this seems to be a common problem and we have some great solutions to fix it. Users have been complaining that when trying to use MSPaint, it doesn't work or open. Scrollbars in the app don't work, paste icons don't show up, crashes, etc. Luckily, we've collected some of the most effective troubleshooting methods to help you resolve issues with Microsoft Paint app. Why doesn't Microsoft Paint work? Some possible reasons why MSPaint is not working on Windows 11/10 PC are as follows: The security identifier is corrupted. hung system
 Fix caa90019 Microsoft Teams error
Feb 19, 2024 pm 02:30 PM
Fix caa90019 Microsoft Teams error
Feb 19, 2024 pm 02:30 PM
Many users have been complaining about encountering error code caa90019 every time they try to log in using Microsoft Teams. Even though this is a convenient communication app, this mistake is very common. Fix Microsoft Teams Error: caa90019 In this case, the error message displayed by the system is: "Sorry, we are currently experiencing a problem." We have prepared a list of ultimate solutions that will help you resolve Microsoft Teams error caa90019. Preliminary steps Run as administrator Clear Microsoft Teams application cache Delete settings.json file Clear Microsoft from Credential Manager



