 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Research and implementation of network intrusion detection technology based on deep learning
Research and implementation of network intrusion detection technology based on deep learning
Research and implementation of network intrusion detection technology based on deep learning
With the continuous development of network technology, network intrusion and data leakage have become one of the most important challenges in the field of Internet security. Traditional network security technology often relies on rules and signatures, but this approach cannot keep up with increasingly sophisticated attack techniques. Therefore, in the increasingly complex Internet environment, network intrusion detection technology based on deep learning has become a new trend in the field of modern network security.
This article will introduce the research and implementation of network intrusion detection technology based on deep learning technology. This article will focus on introducing the basic knowledge of deep learning and network intrusion detection methods, expounding the application of deep learning in network intrusion detection, and specifically implementing a network intrusion detection model based on deep learning. Finally, the implementation of network intrusion detection technology based on deep learning will be discussed. The advantages and disadvantages are discussed.
1. Introduction to the basic knowledge of deep learning
Deep learning is a type of machine learning that imitates the working way of the human brain's neural network. Deep learning uses multi-layered neural networks to learn and solve complex problems. Simple neurons form a multi-layer neural network, and each neuron calculates its output through weights and biases.
The most commonly used neural network architectures in deep learning include convolutional neural networks (CNN) and long short-term memory networks (LSTM). Convolutional neural networks are suitable for image recognition, while LSTM is suitable for language processing. These networks can be trained to learn a mapping from input to output, updating weights on each neuron in the network.
2. Network intrusion detection technology
Network intrusion detection technology refers to the use of specific algorithms and tools to detect network traffic to discover possible security vulnerabilities or malicious behaviors. Common network intrusion detection methods include rule-based, statistics-based and machine learning-based.
Traditional detection methods based on rules and statistics can handle known attacks well, but it is difficult to deal with unknown and changing attack methods, while network intrusion detection methods based on machine learning can learn Patterns in data to identify new attacks.
3. Network intrusion detection technology based on deep learning
Network intrusion detection technology based on deep learning is a network intrusion detection method based on machine learning. This method mainly detects abnormal behaviors in network traffic by training deep neural networks to quickly identify network intrusion behaviors.
In deep learning methods, convolutional neural networks (CNN) and long short-term memory networks (LSTM) can be used to process network data. Convolutional neural networks can learn the spatial and temporal characteristics of network data, improving the accuracy of network intrusion detection. LSTM can learn the time series characteristics of network data to further improve the effect of network intrusion detection methods based on deep learning.
4. Implementation of network intrusion detection based on deep learning
This article implements a network intrusion detection model based on deep learning, using the KDD’99 data set for training and testing. The specific implementation process is as follows:
- Data preprocessing
The KDD'99 data set contains five sub-data sets: training set, test set, training attack set, and test attack set and small data sets. This article uses the training set and test set for model training and testing. The data set contains 42 features, which require data preprocessing. First remove duplicate records, then encode non-numeric features and standardize the features.
- Training model
This article uses convolutional neural network (CNN) and long short-term memory network (LSTM) for model training. Developed using the Keras deep learning framework in Python.
First use the convolutional neural network to process the network intrusion data, and then use the long short-term memory network to process the time series characteristics of the network data. During the model training process, cross-validation techniques are used to evaluate the training effect.
- Test the model
Use the test set to test the model and evaluate the accuracy and efficiency of the model. Use the test data set to evaluate the model's performance and perform analysis.
5. Analysis of the advantages and disadvantages of network intrusion detection technology based on deep learning
Network intrusion detection technology based on deep learning has the following advantages:
- Can handle unknowns and changing attack patterns.
- Can improve the accuracy of network intrusion detection.
- Can reduce the false alarm rate.
However, network intrusion detection technology based on deep learning also has the following shortcomings:
- Requires large computing resources.
- The requirements for training data are relatively high.
- The model has poor interpretability.
6. Summary
This article introduces the research and implementation of network intrusion detection technology based on deep learning technology, and analyzes the advantages and disadvantages of network intrusion detection technology based on deep learning. analyze. This paper proposes a method for network intrusion detection using convolutional neural networks and long short-term memory networks, and implements it on the KDD'99 data set. Network intrusion detection based on deep learning technology will become an important research direction in the field of network security in the future.
The above is the detailed content of Research and implementation of network intrusion detection technology based on deep learning. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
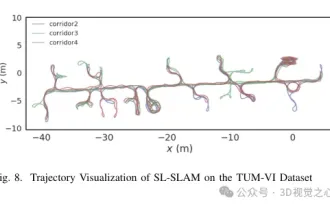 Beyond ORB-SLAM3! SL-SLAM: Low light, severe jitter and weak texture scenes are all handled
May 30, 2024 am 09:35 AM
Beyond ORB-SLAM3! SL-SLAM: Low light, severe jitter and weak texture scenes are all handled
May 30, 2024 am 09:35 AM
Written previously, today we discuss how deep learning technology can improve the performance of vision-based SLAM (simultaneous localization and mapping) in complex environments. By combining deep feature extraction and depth matching methods, here we introduce a versatile hybrid visual SLAM system designed to improve adaptation in challenging scenarios such as low-light conditions, dynamic lighting, weakly textured areas, and severe jitter. sex. Our system supports multiple modes, including extended monocular, stereo, monocular-inertial, and stereo-inertial configurations. In addition, it also analyzes how to combine visual SLAM with deep learning methods to inspire other research. Through extensive experiments on public datasets and self-sampled data, we demonstrate the superiority of SL-SLAM in terms of positioning accuracy and tracking robustness.
 How to implement dual WeChat login on Huawei mobile phones?
Mar 24, 2024 am 11:27 AM
How to implement dual WeChat login on Huawei mobile phones?
Mar 24, 2024 am 11:27 AM
How to implement dual WeChat login on Huawei mobile phones? With the rise of social media, WeChat has become one of the indispensable communication tools in people's daily lives. However, many people may encounter a problem: logging into multiple WeChat accounts at the same time on the same mobile phone. For Huawei mobile phone users, it is not difficult to achieve dual WeChat login. This article will introduce how to achieve dual WeChat login on Huawei mobile phones. First of all, the EMUI system that comes with Huawei mobile phones provides a very convenient function - dual application opening. Through the application dual opening function, users can simultaneously
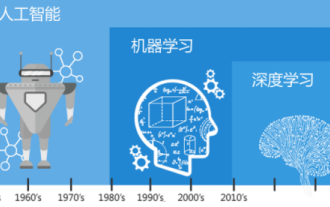 Understand in one article: the connections and differences between AI, machine learning and deep learning
Mar 02, 2024 am 11:19 AM
Understand in one article: the connections and differences between AI, machine learning and deep learning
Mar 02, 2024 am 11:19 AM
In today's wave of rapid technological changes, Artificial Intelligence (AI), Machine Learning (ML) and Deep Learning (DL) are like bright stars, leading the new wave of information technology. These three words frequently appear in various cutting-edge discussions and practical applications, but for many explorers who are new to this field, their specific meanings and their internal connections may still be shrouded in mystery. So let's take a look at this picture first. It can be seen that there is a close correlation and progressive relationship between deep learning, machine learning and artificial intelligence. Deep learning is a specific field of machine learning, and machine learning
 Super strong! Top 10 deep learning algorithms!
Mar 15, 2024 pm 03:46 PM
Super strong! Top 10 deep learning algorithms!
Mar 15, 2024 pm 03:46 PM
Almost 20 years have passed since the concept of deep learning was proposed in 2006. Deep learning, as a revolution in the field of artificial intelligence, has spawned many influential algorithms. So, what do you think are the top 10 algorithms for deep learning? The following are the top algorithms for deep learning in my opinion. They all occupy an important position in terms of innovation, application value and influence. 1. Deep neural network (DNN) background: Deep neural network (DNN), also called multi-layer perceptron, is the most common deep learning algorithm. When it was first invented, it was questioned due to the computing power bottleneck. Until recent years, computing power, The breakthrough came with the explosion of data. DNN is a neural network model that contains multiple hidden layers. In this model, each layer passes input to the next layer and
 PHP Programming Guide: Methods to Implement Fibonacci Sequence
Mar 20, 2024 pm 04:54 PM
PHP Programming Guide: Methods to Implement Fibonacci Sequence
Mar 20, 2024 pm 04:54 PM
The programming language PHP is a powerful tool for web development, capable of supporting a variety of different programming logics and algorithms. Among them, implementing the Fibonacci sequence is a common and classic programming problem. In this article, we will introduce how to use the PHP programming language to implement the Fibonacci sequence, and attach specific code examples. The Fibonacci sequence is a mathematical sequence defined as follows: the first and second elements of the sequence are 1, and starting from the third element, the value of each element is equal to the sum of the previous two elements. The first few elements of the sequence
 How to implement the WeChat clone function on Huawei mobile phones
Mar 24, 2024 pm 06:03 PM
How to implement the WeChat clone function on Huawei mobile phones
Mar 24, 2024 pm 06:03 PM
How to implement the WeChat clone function on Huawei mobile phones With the popularity of social software and people's increasing emphasis on privacy and security, the WeChat clone function has gradually become the focus of people's attention. The WeChat clone function can help users log in to multiple WeChat accounts on the same mobile phone at the same time, making it easier to manage and use. It is not difficult to implement the WeChat clone function on Huawei mobile phones. You only need to follow the following steps. Step 1: Make sure that the mobile phone system version and WeChat version meet the requirements. First, make sure that your Huawei mobile phone system version has been updated to the latest version, as well as the WeChat App.
 AlphaFold 3 is launched, comprehensively predicting the interactions and structures of proteins and all living molecules, with far greater accuracy than ever before
Jul 16, 2024 am 12:08 AM
AlphaFold 3 is launched, comprehensively predicting the interactions and structures of proteins and all living molecules, with far greater accuracy than ever before
Jul 16, 2024 am 12:08 AM
Editor | Radish Skin Since the release of the powerful AlphaFold2 in 2021, scientists have been using protein structure prediction models to map various protein structures within cells, discover drugs, and draw a "cosmic map" of every known protein interaction. . Just now, Google DeepMind released the AlphaFold3 model, which can perform joint structure predictions for complexes including proteins, nucleic acids, small molecules, ions and modified residues. The accuracy of AlphaFold3 has been significantly improved compared to many dedicated tools in the past (protein-ligand interaction, protein-nucleic acid interaction, antibody-antigen prediction). This shows that within a single unified deep learning framework, it is possible to achieve
 Master how Golang enables game development possibilities
Mar 16, 2024 pm 12:57 PM
Master how Golang enables game development possibilities
Mar 16, 2024 pm 12:57 PM
In today's software development field, Golang (Go language), as an efficient, concise and highly concurrency programming language, is increasingly favored by developers. Its rich standard library and efficient concurrency features make it a high-profile choice in the field of game development. This article will explore how to use Golang for game development and demonstrate its powerful possibilities through specific code examples. 1. Golang’s advantages in game development. As a statically typed language, Golang is used in building large-scale game systems.



