 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Preventive measures for common security incidents under Linux systems
Preventive measures for common security incidents under Linux systems
Preventive measures for common security incidents under Linux systems
With the continuous development and popularization of the Internet, computer network security issues have increasingly attracted more and more people's attention. Under the Linux system, due to its high security, it is not absolutely safe, and there is still the possibility of some security incidents. This article introduces some common security incident prevention measures under Linux systems to help users better protect their system security.
- Update and upgrade software
Since the Linux system is open source, there are many open loopholes and doubts. Updating and upgrading software is a must-do task for Linux system administrators. System security can be ensured by regularly updating and upgrading installed software. Administrators should regularly check the installed software packages on the system and upgrade to the latest version to prevent some known vulnerabilities from being exploited by hackers.
- Set a strong password policy
Password policy is the first line of defense to protect administrator and user accounts. It is essential for administrators and users to set strong password policies. A strong password should be of sufficient length and complexity and include uppercase and lowercase letters, numbers, and symbols. In addition, you can also strengthen the complexity of the password, such as setting the password expiration time, etc., to ensure the security of the password.
- Restrict access permissions
On a Linux system, there are many sensitive files and directories, such as /etc/passwd, /etc/shadow, etc. To protect these files and directories, administrators should restrict access rights. For ordinary users, there is no need for them to access these directories and files. Therefore, administrators can restrict ordinary users' access rights. Additionally, different access rights can be set up for different users and roles to protect the system from insider attacks.
- Using a Firewall
A firewall is an important method of controlling network traffic in and out of your system. In Linux systems, you can use tools such as iptables to set firewall rules. By setting up appropriate firewall rules, administrators can limit unnecessary network connections and communications and perform port and protocol filtering. This protects the system from malicious and unknown attacks.
- Use encrypted communication protocol
Using encrypted communication protocol in Linux system can enhance the security of data transmission. For example, for SSH, it can be configured to only allow strong password and public key authentication. In addition, using the HTTPS protocol in a Linux system can encrypt network communications to protect the security of data during transmission.
- Regular backup of data and system
Backup is one of the important means to protect the system and data. If a system is compromised or data is damaged or lost, backups can restore data and system integrity. Therefore, for Linux system administrators, regular backup of data and systems is very necessary. It is best to store your backup data in another place, such as cloud storage or an external hard drive, to avoid backup data and system corruption and loss.
Summary
Under the Linux system, it is very important to protect the security of the system and data. These security incident prevention measures can help administrators better protect their system security and avoid sensitive data and files from being attacked and leaked by hackers. Whether you use Linux as a server or Linux as a desktop operating system, you need to take certain security measures to ensure the security of your system and data.
The above is the detailed content of Preventive measures for common security incidents under Linux systems. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 How to use Vue for permission management and access control
Aug 02, 2023 pm 09:01 PM
How to use Vue for permission management and access control
Aug 02, 2023 pm 09:01 PM
How to use Vue for permission management and access control In modern web applications, permission management and access control is a critical feature. As a popular JavaScript framework, Vue provides a simple and flexible way to implement permission management and access control. This article will introduce how to use Vue to implement basic permission management and access control functions, and attach code examples. Defining Roles and Permissions Before you begin, you first need to define the roles and permissions in your application. A role is a specific set of permissions, and
 How to use PHP scripts for log monitoring in Linux systems
Oct 05, 2023 am 11:36 AM
How to use PHP scripts for log monitoring in Linux systems
Oct 05, 2023 am 11:36 AM
How to use PHP scripts for log monitoring in Linux systems. With the widespread application of Linux systems, system monitoring and log analysis have become more and more important. Among them, using PHP scripts for log monitoring is a common way. This article will introduce how to use PHP scripts to implement simple log monitoring and provide specific code examples. 1. Create a PHP script file. First, create a file named "log_monitor.php" on the Linux system. This file will be used to monitor the specified
 How to implement log monitoring and alerting through Linux tools?
Jul 28, 2023 pm 08:41 PM
How to implement log monitoring and alerting through Linux tools?
Jul 28, 2023 pm 08:41 PM
How to implement log monitoring and alerting through Linux tools? In the daily server management and operation and maintenance process, real-time monitoring and analysis of logs is very important. The Linux system provides some powerful tools that can help us implement log monitoring and alarm functions. This article explains how to use Linux tools to monitor and alert logs, and provides some code examples. Use the tail command to view logs in real time. The tail command can view the updated content of log files in real time. By using the tail command, we can
 Use Go language to solve large-scale access control problems
Jun 15, 2023 pm 02:59 PM
Use Go language to solve large-scale access control problems
Jun 15, 2023 pm 02:59 PM
With the development of the Internet, access control issues have increasingly become an important topic. In traditional permission management, role authorization or access control lists are generally used to control resources. However, this method is often unable to adapt to large-scale access control needs because it is difficult to flexibly implement access control for different roles and resources. To solve this problem, using Go language to solve large-scale access control problems has become an effective method. Go language is a language for concurrent programming. It has excellent concurrency performance and fast compilation.
 How Nginx implements access control configuration based on request source IP
Nov 08, 2023 am 10:09 AM
How Nginx implements access control configuration based on request source IP
Nov 08, 2023 am 10:09 AM
How Nginx implements access control configuration based on the request source IP requires specific code examples. In network application development, protecting the server from malicious attacks is a very important step. Using Nginx as a reverse proxy server, we can configure IP access control to restrict access to specific IP addresses to improve server security. This article will introduce how to implement access control configuration based on request source IP in Nginx and provide specific code examples. First, we need to edit the Nginx configuration file
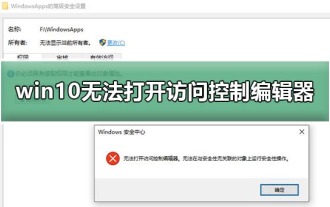 Access Control Editor cannot be opened in Win10
Jan 03, 2024 pm 10:05 PM
Access Control Editor cannot be opened in Win10
Jan 03, 2024 pm 10:05 PM
The inability to open the access control editor in win10 is an uncommon problem. This problem usually occurs in external hard drives and USB flash drives. In fact, the solution is very simple. Just open it in safe mode and take a look. Let’s take a look at the details below. tutorial. Win10 cannot open the access control editor 1. In the login interface, hold down shift, click the button, click 2.--, click 3. After restarting, press F5 to try to enter and see if you can enter. Articles related to win10 safe mode>>>How to enter win10 safe mode<<<>>>How to repair the system in win10 safe mode<<<
 An in-depth exploration of Nginx's traffic analysis and access control methods
Aug 05, 2023 pm 05:46 PM
An in-depth exploration of Nginx's traffic analysis and access control methods
Aug 05, 2023 pm 05:46 PM
An in-depth discussion of Nginx's traffic analysis and access control methods. Nginx is a high-performance open source web server. It is powerful and scalable, so it is widely used in the Internet field. In practical applications, we usually need to analyze Nginx traffic and control access. This article will delve into Nginx's traffic analysis and access control methods and provide corresponding code examples. 1. Nginx traffic analysis Nginx provides many built-in variables that can be used to analyze traffic. Among them, commonly used
 How does PHP handle cross-domain requests and access control?
Jun 30, 2023 pm 11:04 PM
How does PHP handle cross-domain requests and access control?
Jun 30, 2023 pm 11:04 PM
How does PHP handle cross-domain requests and access control? Abstract: With the development of Internet applications, cross-domain requests and access control have become an important issue in PHP development. This article will introduce methods and techniques on how PHP handles cross-domain requests and access control, aiming to help developers better understand and deal with these issues. What is a cross-domain request? Cross-domain request means that in the browser, a web page in one domain requests to access resources in another domain. Cross-domain requests generally occur in AJAX requests, image/script/css references, etc. Depend on



