PHP Form Guard Tips: Using Guard Web Application Scripts
In today's digital age, Web applications play an increasingly important role in people's daily lives. However, with the increase in web applications, network security risks are also increasing. In particular, online forms are becoming more and more common in various web applications, which allows attackers to use various methods to attack forms, such as SQL injection, cross-site scripting attacks, etc.
To protect web applications, developers should take appropriate measures to guard against these attacks. This article will introduce some PHP form defense tips, including how to use guard web application scripts to prevent attacks.
- Use secure PHP functions
In PHP programs, there are some secure built-in functions that can help developers protect web applications from attacks. For example, use the htmlspecialchars function to convert special characters into HTML entities to prevent cross-site scripting attacks. SQL injection attacks can be prevented using the mysqli_real_escape_string function. Therefore, developers should use these secure built-in functions to handle form data to ensure the security of web applications.
- Perform input verification
Input verification is one of the key steps to prevent attacks. Developers should validate form data to ensure they conform to the expected format and type. For example, if the form is for entering an email address, the entered email addresses should be validated to ensure that they contain the @ symbol and a valid domain name. If the form is used to enter numbers, the entered data should be validated to ensure that they are of a legal numeric type.
- Use verification codes
Verification codes are a common prevention mechanism that can help developers prevent automated attacks. By requiring the user to enter a verification code, developers can verify that this is a real user and prevent automation code from trying to submit the form. CAPTCHA is a simple yet effective prevention mechanism and a good way to protect web applications from attacks.
- Use Protective Web Application Scripts
Finally, developers can use Protective Web Application Scripts to protect against attacks. These scripts can detect and block various attacks, such as SQL injection, cross-site scripting attacks, etc. Developers can use some popular scripts to protect web applications, such as ModSecurity, PHPIDS, etc. These scripts can help developers detect and block attacks and provide detailed logging and reporting.
Summary
Forms play an important role in web applications, but due to their open nature, they also become the target of attackers. Developers should take appropriate measures to secure web applications. The PHP form protection techniques introduced above can help developers prevent various attacks and protect the security of web applications.
The above is the detailed content of PHP Form Guard Tips: Using Guard Web Application Scripts. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 CakePHP Working with Database
Sep 10, 2024 pm 05:25 PM
CakePHP Working with Database
Sep 10, 2024 pm 05:25 PM
Working with database in CakePHP is very easy. We will understand the CRUD (Create, Read, Update, Delete) operations in this chapter.
 CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
To work with date and time in cakephp4, we are going to make use of the available FrozenTime class.
 CakePHP File upload
Sep 10, 2024 pm 05:27 PM
CakePHP File upload
Sep 10, 2024 pm 05:27 PM
To work on file upload we are going to use the form helper. Here, is an example for file upload.
 Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
CakePHP is an open-source framework for PHP. It is intended to make developing, deploying and maintaining applications much easier. CakePHP is based on a MVC-like architecture that is both powerful and easy to grasp. Models, Views, and Controllers gu
 CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
Validator can be created by adding the following two lines in the controller.
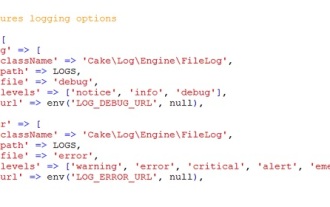 CakePHP Logging
Sep 10, 2024 pm 05:26 PM
CakePHP Logging
Sep 10, 2024 pm 05:26 PM
Logging in CakePHP is a very easy task. You just have to use one function. You can log errors, exceptions, user activities, action taken by users, for any background process like cronjob. Logging data in CakePHP is easy. The log() function is provide
 How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
Visual Studio Code, also known as VS Code, is a free source code editor — or integrated development environment (IDE) — available for all major operating systems. With a large collection of extensions for many programming languages, VS Code can be c




