 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Website Security Architecture Design Guide: Protection against Reflection Attacks in PHP
Website Security Architecture Design Guide: Protection against Reflection Attacks in PHP
Website Security Architecture Design Guide: Protection against Reflection Attacks in PHP
With the continuous development and popularization of the Internet, website security is particularly important. When developing a website, we must not only consider functionality and user experience, but also pay attention to the security of the website. In the design of website security architecture, reflection attacks are one of the common attack methods. Especially when using PHP to develop websites, we need to take corresponding protective measures.
Reflection attack is an attack method that uses user input data to execute malicious code on the server side. It takes advantage of the unique characteristics of dynamic programming languages (such as PHP) and executes user-entered data as part of the code, leading to security vulnerabilities. In PHP, this attack method mainly uses the reflection API.
The Reflection API is a set of tools provided by PHP for obtaining and manipulating information such as classes, methods, properties, etc. at runtime. Its role is to enhance the flexibility and dynamics of PHP, but it also provides convenience for reflection attacks.
In order to prevent reflection attacks, we can adopt the following protection strategies:
- Input verification and filtering: Before receiving user input data, strict verification and filtering must be performed , to ensure that the data entered is as expected. You can use filter functions (such as filter_var) or regular expressions to validate the input data and filter it according to the expected format.
- Parameterized query: When constructing a SQL query statement, be sure to use parameterized queries (prepared statements) instead of splicing strings. Parameterized queries can process user input data and query statements separately to avoid SQL injection attacks. In PHP, parameterized queries can be implemented using PDO or mysqli extensions.
- Input data encoding: Before using user-entered data for dynamic code execution, the input data must be appropriately encoded. You can use functions such as htmlspecialchars or htmlentities to escape special characters to avoid the injection of malicious code.
- Strictly limit the permissions of the reflection API: When using the reflection API, be sure to set appropriate permissions and strictly limit the scope of its executable dynamic code. You can use classes such as ReflectionClass and ReflectionMethod to obtain class information and adopt appropriate permission control strategies.
- Regular updates and maintenance: Timely track and fix PHP security vulnerabilities, use the latest version of PHP, and apply security patches in a timely manner. Regularly review and update your own code to promptly fix possible security risks.
In short, website security is an important aspect that cannot be ignored in website development. In PHP, protecting against reflection attacks is an important aspect of ensuring website security. Through reasonable input validation and filtering, parameterized queries, input data encoding, strict restriction of reflection API permissions, and regular updates and maintenance, we can improve the security of the website and reduce the threat of reflection attacks to the website. I hope this article will help everyone understand and prevent reflection attacks in PHP.
The above is the detailed content of Website Security Architecture Design Guide: Protection against Reflection Attacks in PHP. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 What is the architecture and working principle of Spring Data JPA?
Apr 17, 2024 pm 02:48 PM
What is the architecture and working principle of Spring Data JPA?
Apr 17, 2024 pm 02:48 PM
SpringDataJPA is based on the JPA architecture and interacts with the database through mapping, ORM and transaction management. Its repository provides CRUD operations, and derived queries simplify database access. Additionally, it uses lazy loading to only retrieve data when necessary, thus improving performance.
 How steep is the learning curve of golang framework architecture?
Jun 05, 2024 pm 06:59 PM
How steep is the learning curve of golang framework architecture?
Jun 05, 2024 pm 06:59 PM
The learning curve of the Go framework architecture depends on familiarity with the Go language and back-end development and the complexity of the chosen framework: a good understanding of the basics of the Go language. It helps to have backend development experience. Frameworks that differ in complexity lead to differences in learning curves.
 Hand-tearing Llama3 layer 1: Implementing llama3 from scratch
Jun 01, 2024 pm 05:45 PM
Hand-tearing Llama3 layer 1: Implementing llama3 from scratch
Jun 01, 2024 pm 05:45 PM
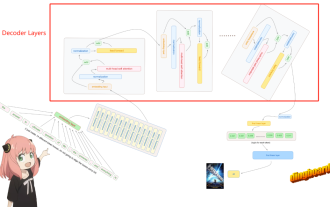
1. Architecture of Llama3 In this series of articles, we implement llama3 from scratch. The overall architecture of Llama3: Picture the model parameters of Llama3: Let's take a look at the actual values of these parameters in the Llama3 model. Picture [1] Context window (context-window) When instantiating the LlaMa class, the variable max_seq_len defines context-window. There are other parameters in the class, but this parameter is most directly related to the transformer model. The max_seq_len here is 8K. Picture [2] Vocabulary-size and AttentionL
 Review! Comprehensively summarize the important role of basic models in promoting autonomous driving
Jun 11, 2024 pm 05:29 PM
Review! Comprehensively summarize the important role of basic models in promoting autonomous driving
Jun 11, 2024 pm 05:29 PM
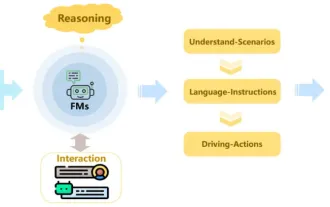
Written above & the author’s personal understanding: Recently, with the development and breakthroughs of deep learning technology, large-scale foundation models (Foundation Models) have achieved significant results in the fields of natural language processing and computer vision. The application of basic models in autonomous driving also has great development prospects, which can improve the understanding and reasoning of scenarios. Through pre-training on rich language and visual data, the basic model can understand and interpret various elements in autonomous driving scenarios and perform reasoning, providing language and action commands for driving decision-making and planning. The base model can be data augmented with an understanding of the driving scenario to provide those rare feasible features in long-tail distributions that are unlikely to be encountered during routine driving and data collection.
 Tips for turning off real-time protection in Windows Security Center
Mar 27, 2024 pm 10:09 PM
Tips for turning off real-time protection in Windows Security Center
Mar 27, 2024 pm 10:09 PM
In today's digital society, computers have become an indispensable part of our lives. As one of the most popular operating systems, Windows is widely used around the world. However, as network attack methods continue to escalate, protecting personal computer security has become particularly important. The Windows operating system provides a series of security functions, of which "Windows Security Center" is one of its important components. In Windows systems, "Windows Security Center" can help us
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access



