How to implement role permission management system in PHP?
PHP is a widely used programming language that is widely used to create and develop various web applications. In many web applications, the role permission management system is an important feature to ensure that different users have appropriate access rights. This article will introduce how to use PHP to implement a simple and practical role permission management system.
The basic concept of the role permission management system is to divide users into different roles and assign corresponding permissions to each role. In this way, users can only perform operations they have permission to perform, thereby ensuring system security.
First, we need to create a database to store user information, role information and permission information. You can use MySQL or other relational databases to create this database. In the database, we can create three tables: user table, role table and permission table.
The user table contains the user's basic information, such as user name, password, role ID, etc. The role table contains role information, such as role name and description. The permission table contains various permissions of the system, such as accessing a certain page or performing a certain operation.
Next, we use PHP to write some functions to implement the role permission management system.
First, we need to implement a function to verify the user's login information:
function login($username, $password) {
// 查询数据库,验证用户名和密码的正确性
// 如果验证通过,返回用户ID和角色ID,否则返回false
}
Next, we implement a function to check whether the user has permission to perform an operation:
function checkPermission($roleId, $permission) {
// 查询数据库,验证角色ID和权限的对应关系
// 如果验证通过,返回true,否则返回false
}
Finally, we implement a function to obtain the user's role information:
function getRole($userId) {
// 查询数据库,获取用户的角色ID
// 返回角色ID
}
With these functions, we can use them in specific business logic to implement role permission management. For example, when a user logs in to the system, we can call the login function for verification and save the returned user ID and role ID in the Session. In business logic, we can use the checkPermission function to check whether the user has permission to perform an operation.
Of course, the above is just a simple implementation example. The actual role permission management system may also involve more complex functions, such as role inheritance and multi-level permission control. This needs to be expanded and refined based on specific business needs.
In short, PHP is a powerful and flexible programming language that can be used to implement various web applications. By rationally using PHP's database operation functions and programming skills, we can relatively easily implement a role authority management system to ensure the security and reliability of the system.
The above is the detailed content of How to implement role permission management system in PHP?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
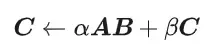 CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
General Matrix Multiplication (GEMM) is a vital part of many applications and algorithms, and is also one of the important indicators for evaluating computer hardware performance. In-depth research and optimization of the implementation of GEMM can help us better understand high-performance computing and the relationship between software and hardware systems. In computer science, effective optimization of GEMM can increase computing speed and save resources, which is crucial to improving the overall performance of a computer system. An in-depth understanding of the working principle and optimization method of GEMM will help us better utilize the potential of modern computing hardware and provide more efficient solutions for various complex computing tasks. By optimizing the performance of GEMM
 Enable root permissions with one click (quickly obtain root permissions)
Jun 02, 2024 pm 05:32 PM
Enable root permissions with one click (quickly obtain root permissions)
Jun 02, 2024 pm 05:32 PM
It allows users to perform more in-depth operations and customization of the system. Root permission is an administrator permission in the Android system. Obtaining root privileges usually requires a series of tedious steps, which may not be very friendly to ordinary users, however. By enabling root permissions with one click, this article will introduce a simple and effective method to help users easily obtain system permissions. Understand the importance and risks of root permissions and have greater freedom. Root permissions allow users to fully control the mobile phone system. Strengthen security controls, customize themes, and users can delete pre-installed applications. For example, accidentally deleting system files causing system crashes, excessive use of root privileges, and inadvertent installation of malware are also risky, however. Before using root privileges
 Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
On July 29, at the roll-off ceremony of AITO Wenjie's 400,000th new car, Yu Chengdong, Huawei's Managing Director, Chairman of Terminal BG, and Chairman of Smart Car Solutions BU, attended and delivered a speech and announced that Wenjie series models will be launched this year In August, Huawei Qiankun ADS 3.0 version was launched, and it is planned to successively push upgrades from August to September. The Xiangjie S9, which will be released on August 6, will debut Huawei’s ADS3.0 intelligent driving system. With the assistance of lidar, Huawei Qiankun ADS3.0 version will greatly improve its intelligent driving capabilities, have end-to-end integrated capabilities, and adopt a new end-to-end architecture of GOD (general obstacle identification)/PDP (predictive decision-making and control) , providing the NCA function of smart driving from parking space to parking space, and upgrading CAS3.0
 How many characters are there in Blazlan Chaos Effect?
Mar 21, 2024 pm 10:56 PM
How many characters are there in Blazlan Chaos Effect?
Mar 21, 2024 pm 10:56 PM
Blue Wings Chaos Effect features a diverse cast of characters, each with a unique identity and backstory. For this reason, the editor has specially compiled an introduction to the characters of BlazBlue Chaos Effect for all players. How many characters are there in BlazBlue Chaos Effect? Answer: There are 7 characters. 1. [God of Death] Ragnar Chad Bradedge (nicknamed RG, Nissan), his brother and sister were raised by church nuns. One day, one of the six heroes of the villain broke in, killed the nuns, and burned them down. Church, took his sister away, leaving behind his younger brother "The Weapon of Things" Ice Sword Snow Girl. 2. Noel Vermillion The adopted daughter of the Vermillion family looks almost the same as Ragnar's sister. After graduation, he joined the governing body as secretary to Ragnar's younger brother. 3. λ-11 is collectively known as Lambda and Eleventh Sister. After the original developer gave up, Kokonoe rescued and
 The best alternative to CrushOn.AI that offers unlimited free messages
Mar 06, 2024 pm 12:10 PM
The best alternative to CrushOn.AI that offers unlimited free messages
Mar 06, 2024 pm 12:10 PM
In this article we will introduce you to the best alternatives to CrushOn.AI with free and unlimited messaging capabilities. There are many artificial intelligence platforms on the market now that allow users to talk to characters from various media such as animation, which provides users with a more interesting and interactive experience. What is CrushOn.AI? CrushonAI is an AI chatbot platform that allows users to experience the fun of interaction by having conversations with virtual characters. Users have the opportunity to communicate with, build connections with, and create storylines related to their favorite characters across a variety of media including anime. The best alternative to CrushOn.AI that offers unlimited free messages If you are looking for the best Crush
 Anchor Point Advent Novice Ten Company Character Recommendations
Feb 20, 2024 pm 02:30 PM
Anchor Point Advent Novice Ten Company Character Recommendations
Feb 20, 2024 pm 02:30 PM
Anchor Arrival is a 3D turn-based card game with a high-definition beautiful girl two-dimensional theme. It provides a rich and exciting combination of characters for players to explore and experience. It has many powerful combinations of high-quality lineups. New players are also curious novices. What powerful characters are recommended in the pool? Let’s take a look at the selection reference for novices to win ten consecutive golds! Anchor Point Advent is a powerful character recommendation for novice pools. The first ten-consecutive pick is Alice. She is mainly a single-target lightning-type burst character. The output is very explosive, and the experience will be very friendly to newcomers, so it is highly recommended to choose it. It is recommended to choose the combination of "Alice" + "Antelope" for 10 points. Alice is the most worthy character to output the goldpire attribute, and is not even a bit stronger than the other two characters in the novice card pool. Alice can pass special
 Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
The best version of the Apple 16 system is iOS16.1.4. The best version of the iOS16 system may vary from person to person. The additions and improvements in daily use experience have also been praised by many users. Which version of the Apple 16 system is the best? Answer: iOS16.1.4 The best version of the iOS 16 system may vary from person to person. According to public information, iOS16, launched in 2022, is considered a very stable and performant version, and users are quite satisfied with its overall experience. In addition, the addition of new features and improvements in daily use experience in iOS16 have also been well received by many users. Especially in terms of updated battery life, signal performance and heating control, user feedback has been relatively positive. However, considering iPhone14
 Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
On April 11, Huawei officially announced the HarmonyOS 4.2 100-machine upgrade plan for the first time. This time, more than 180 devices will participate in the upgrade, covering mobile phones, tablets, watches, headphones, smart screens and other devices. In the past month, with the steady progress of the HarmonyOS4.2 100-machine upgrade plan, many popular models including Huawei Pocket2, Huawei MateX5 series, nova12 series, Huawei Pura series, etc. have also started to upgrade and adapt, which means that there will be More Huawei model users can enjoy the common and often new experience brought by HarmonyOS. Judging from user feedback, the experience of Huawei Mate60 series models has improved in all aspects after upgrading HarmonyOS4.2. Especially Huawei M




