 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Improve Linux system security: optimize and adjust file permission settings
Improve Linux system security: optimize and adjust file permission settings
Improve Linux system security: optimize and adjust file permission settings
How to optimize and adjust the file permission settings of Linux systems to improve security
Introduction
In today’s digital age, data security is crucial. For Linux systems, file permission settings are a key security measure, which can effectively protect important system data from being accessed or tampered with by unauthorized personnel. This article will introduce how to optimize and adjust the file permission settings of Linux systems to improve security.
1. Understand file permissions
Before we start optimizing and adjusting file permissions, we need to understand the basic concepts of file permissions. In a Linux system, every file and directory has three basic permissions: read (r), write (w), and execute (x). These permissions can be set between users (owners), user groups (groups) and other users (others) respectively. By setting these permissions correctly, we can ensure that only authorized users can access and modify files.
2. Use the principle of least privileges
The "principle of least privileges" is one of the important principles for setting file permissions. This means we should assign minimal permissions to each user and user group to prevent unnecessary file access and modification. Users are given only the permissions they need based on their needs, rather than giving them all permissions. This reduces the opportunities for potential attackers and increases the security of your system.
3. Follow the correct ownership and group settings
Correct ownership and group settings are very important to restrict specific users' access to files. Every file and directory has an owner and a group that belongs to a specific group. With the correct settings, we can ensure that only the owner and group members have access to the file.
We can use the chown command to change the owner of a file or directory, for example:
1 |
|
We can also use the chgrp command to change the group of a file or directory, for example:
1 |
|
4. Use the chmod command correctly
The chmod command is the key command to adjust file permissions. It can use numbers or symbols to represent permission settings. The following are some commonly used chmod command examples:
1) Use numbers to represent permissions
1 2 |
|
2) Use symbols to represent permissions
1 2 |
|
Using the chmod command correctly can ensure that only authorized users Able to perform specific operations to improve system security.
5. Use ACL (Access Control List)
In addition to basic Linux file permission settings, we can also use ACL (Access Control List) to more accurately control access permissions to files and directories. ACL allows us to set permissions for multiple users and groups on a single file or directory. We can use the setfacl and getfacl commands to add, delete and modify ACLs.
For example, we can use the setfacl command to add read and write permissions to user 1:
1 |
|
Use the getfacl command to view the ACL settings of a file or directory:
1 |
|
6. Regularly review permission settings
File permission settings are not a one-time task, but require regular review and adjustment. We should regularly check permissions on files and directories and remove access permissions from users and groups that are no longer needed. This ensures that the system is always in optimal security.
Conclusion
By optimizing and adjusting the file permission settings of the Linux system, we can effectively improve the security of the system. Using the principle of least privilege, following correct ownership and group settings, using the chmod command correctly, and using ACLs for more granular permission control can help us prevent potential attacks and protect the system's important data. At the same time, we should also regularly review permission settings to ensure that the system is always maintained in an optimal security state.
Reference materials:
- Linux permission setting guide: https://www.thegeekstuff.com/2010/04/unix-file-and-directory-permissions/
- Use ACL to manage file permissions: https://linux.die.net/man/1/setfacl
The above is the detailed content of Improve Linux system security: optimize and adjust file permission settings. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 PHP changes current umask
Mar 22, 2024 am 08:41 AM
PHP changes current umask
Mar 22, 2024 am 08:41 AM
This article will explain in detail about changing the current umask in PHP. The editor thinks it is quite practical, so I share it with you as a reference. I hope you can gain something after reading this article. Overview of PHP changing current umask umask is a php function used to set the default file permissions for newly created files and directories. It accepts one argument, which is an octal number representing the permission to block. For example, to prevent write permission on newly created files, you would use 002. Methods of changing umask There are two ways to change the current umask in PHP: Using the umask() function: The umask() function directly changes the current umask. Its syntax is: intumas
 Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation? With the wide application of Golang in the field of programming, more and more developers choose to use Golang to develop various types of applications. However, like other programming languages, there are security challenges in Golang development. In particular, Golang's power and flexibility also make it a potential virus creation tool. This article will delve into security issues in Golang development and provide some methods to avoid G
 What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
Memory management in Java involves automatic memory management, using garbage collection and reference counting to allocate, use and reclaim memory. Effective memory management is crucial for security because it prevents buffer overflows, wild pointers, and memory leaks, thereby improving the safety of your program. For example, by properly releasing objects that are no longer needed, you can avoid memory leaks, thereby improving program performance and preventing crashes.
 C++ program optimization: time complexity reduction techniques
Jun 01, 2024 am 11:19 AM
C++ program optimization: time complexity reduction techniques
Jun 01, 2024 am 11:19 AM
Time complexity measures the execution time of an algorithm relative to the size of the input. Tips for reducing the time complexity of C++ programs include: choosing appropriate containers (such as vector, list) to optimize data storage and management. Utilize efficient algorithms such as quick sort to reduce computation time. Eliminate multiple operations to reduce double counting. Use conditional branches to avoid unnecessary calculations. Optimize linear search by using faster algorithms such as binary search.
 How to optimize the startup items of WIN7 system
Mar 26, 2024 pm 06:20 PM
How to optimize the startup items of WIN7 system
Mar 26, 2024 pm 06:20 PM
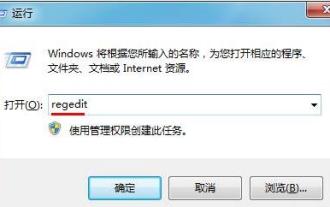
1. Press the key combination (win key + R) on the desktop to open the run window, then enter [regedit] and press Enter to confirm. 2. After opening the Registry Editor, we click to expand [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorer], and then see if there is a Serialize item in the directory. If not, we can right-click Explorer, create a new item, and name it Serialize. 3. Then click Serialize, then right-click the blank space in the right pane, create a new DWORD (32) bit value, and name it Star
 Vivox100s parameter configuration revealed: How to optimize processor performance?
Mar 24, 2024 am 10:27 AM
Vivox100s parameter configuration revealed: How to optimize processor performance?
Mar 24, 2024 am 10:27 AM
Vivox100s parameter configuration revealed: How to optimize processor performance? In today's era of rapid technological development, smartphones have become an indispensable part of our daily lives. As an important part of a smartphone, the performance optimization of the processor is directly related to the user experience of the mobile phone. As a high-profile smartphone, Vivox100s's parameter configuration has attracted much attention, especially the optimization of processor performance has attracted much attention from users. As the "brain" of the mobile phone, the processor directly affects the running speed of the mobile phone.
 What are some ways to resolve inefficiencies in PHP functions?
May 02, 2024 pm 01:48 PM
What are some ways to resolve inefficiencies in PHP functions?
May 02, 2024 pm 01:48 PM
Five ways to optimize PHP function efficiency: avoid unnecessary copying of variables. Use references to avoid variable copying. Avoid repeated function calls. Inline simple functions. Optimizing loops using arrays.
 Iterator safety guarantees for C++ container libraries
Jun 05, 2024 pm 04:07 PM
Iterator safety guarantees for C++ container libraries
Jun 05, 2024 pm 04:07 PM
The C++ container library provides the following mechanisms to ensure the safety of iterators: 1. Container immutability guarantee; 2. Copy iterator; 3. Range for loop; 4. Const iterator; 5. Exception safety.



