 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 PHP secure coding practices: preventing session hijacking and pinning
PHP secure coding practices: preventing session hijacking and pinning
PHP secure coding practices: preventing session hijacking and pinning
PHP secure coding practices: preventing session hijacking and fixation
With the development and popularization of the Internet, network security issues have become increasingly prominent. As a widely used server-side scripting language, PHP also faces various security risks. Among them, session hijacking and session fixation attacks are one of the common attack methods. This article will focus on PHP secure coding practices to prevent session hijacking and fixation and improve application security.
1. Session hijacking
Session hijacking means that the attacker obtains the session ID of a legitimate user by some means, thereby controlling the user's session. Once an attacker successfully hijacks a user's session, he or she can impersonate the user and perform various malicious operations. To prevent session hijacking, developers can take the following measures:
- Use HTTPS to transmit sensitive data
Using HTTPS can encrypt data transmission to ensure that sensitive information will not be eavesdropped or tamper. By configuring an SSL certificate in the application, developers can implement HTTPS transport and use HTTPS for operations involving sensitive information such as logins.
- Set secure cookie attributes
By setting the security attributes of cookies, you can ensure that cookies can only be transmitted under HTTPS connections. Developers can achieve this by setting the secure attribute of the cookie to true, for example:
ini_set('session.cookie_secure', true);- Use the HTTPOnly attribute
When setting a cookie, adding the HTTPOnly attribute can prevent JavaScript from being used. The script obtains the cookie contents, thereby reducing the risk of session hijacking. Developers can set the HTTPOnly attribute of Cookie through the following code:
ini_set('session.cookie_httponly', true);- Limit the session life cycle
Set the session life cycle appropriately to reduce the session being exploited by attackers for a long time possibility. Developers can control the maximum lifetime of the session by setting the session.gc_maxlifetime parameter, for example:
ini_set('session.gc_maxlifetime', 3600);- Randomize session ID
By randomly generating session ID, it can be effective Prevent attackers from hijacking sessions by guessing session IDs. Developers can specify the entropy source file used to randomize session IDs by setting the session.entropy_file parameter, for example:
ini_set('session.entropy_file', '/dev/urandom');
ini_set('session.entropy_length', '32');2. Session fixation
Session fixation means that the attacker passes some kind of Means to obtain the session ID of a legitimate user and force the user to use the session ID to log in, thereby controlling the user session. To prevent session fixation attacks, developers can take the following measures:
- Detect and prevent IP address changes
An attacker may implement a session fixation attack through IP address changes. Developers can detect the user's IP address before a login page or sensitive operation, compare it with the previously saved IP address, and interrupt the session if it changes. For example:
if ($_SESSION['user_ip'] !== $_SERVER['REMOTE_ADDR']) {
session_unset();
session_destroy();
exit;
}- Generate new session ID
After the user logs in, generate a new session ID to avoid using the original session ID. Developers can use the session_regenerate_id function to generate a new session ID, for example:
session_regenerate_id(true);
- Set the validity period of the session ID
Set the validity period of the session ID reasonably to prevent the session ID from being used for a long time efficient. Developers can control the validity period of the session ID by setting the session.cookie_lifetime parameter, for example:
ini_set('session.cookie_lifetime', 3600);- Use redirection
Use redirection after user login or sensitive operation Direct the user to a new page. This prevents attackers from obtaining session IDs through malicious links or other means. For example:
header('Location: secure_page.php');Through the above secure coding practices, developers can effectively prevent session hijacking and session fixation attacks and improve application security. However, secure coding is only one aspect. Reasonable permission control and input verification are also important measures to ensure application security. Developers should constantly learn and update security knowledge, fix vulnerabilities in a timely manner, and ensure the security of applications.
The above is the detailed content of PHP secure coding practices: preventing session hijacking and pinning. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
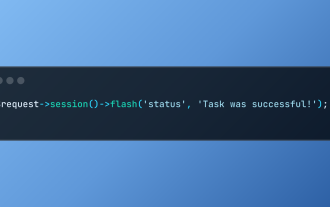 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
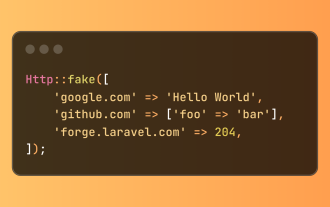 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
The article discusses adding custom functionality to frameworks, focusing on understanding architecture, identifying extension points, and best practices for integration and debugging.
 Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Article discusses essential security features in frameworks to protect against vulnerabilities, including input validation, authentication, and regular updates.



