Analysis of security logging technology in PHP
PHP is a widely used development language, and many websites and applications use PHP as their back-end technology. However, due to its open source nature, PHP also faces security risks. Malicious attackers can exploit PHP's weaknesses to attack and intrude, so secure logging technology is crucial to protecting the security of PHP applications.
Security logging refers to the process of recording security events and exceptions that occur in an application. By analyzing and monitoring these logs, potential threats can be discovered in time and corresponding defensive measures can be taken. In PHP applications, security logging can help developers track attackers' behavior, detect vulnerabilities, and perform intrusion detection and response.
Security logging in PHP applications includes the following important aspects:
- Detecting and blocking malicious requests: By using appropriate security firewalls and filters, you can detect and Block malicious requests. For example, you can use a WAF (Web Application Firewall) to detect and block common attack methods such as SQL injection and cross-site scripting attacks.
- Record access log: record the user's access behavior, including IP address, access time, request method and other information. These logs can be used for subsequent analysis and investigation, helping to discover abnormal access and illegal operations.
- Record error log: record errors and exceptions in the program, including warnings, fatal errors, exceptions, etc. These logs can help developers fix vulnerabilities and defects in a timely manner and improve the stability and security of applications.
- Record security events: Record security-related events and behaviors, such as login failure, permission violation, file upload, etc. Through these logs, potential security threats can be discovered and corresponding measures can be taken for defense.
In order to achieve secure logging, PHP provides some built-in functions and extensions:
- error_log function: used to write error information to a log file or send it to other Targets such as emails, databases, etc. You can specify the log type, storage location and format by setting the parameters of the error_log function.
- syslog function: used to send log information to the system's logger, such as syslogd. Through the syslog function, log information can be distributed to multiple targets and filtered and classified according to priority and type.
- PHP extension: PHP provides many security logging extensions, such as Suhosin, PHPIDS, etc. These extensions can help developers enhance PHP's security and logging capabilities and provide more comprehensive security defense measures.
In addition to the above methods and technologies, developers can also use PHP frameworks and third-party tools to achieve more advanced security logging. For example, the user authentication and authorization functions of the Laravel framework can be used to record user login and permission operations; the ELK (Elasticsearch, Logstash, and Kibana) stack can be used to achieve real-time log analysis and visualization.
In actual applications, security logging needs to be configured and used according to specific needs and risk assessment. On the one hand, excessive logging needs to be avoided to avoid affecting the performance and availability of the application; on the other hand, the security of the logs needs to be ensured to prevent malicious attackers from tampering and deleting the logs. At the same time, with the implementation of regulations such as GDPR (General Data Protection Regulation), protecting users' privacy and sensitive information has become one of the requirements for security logging.
In short, security logging is one of the important means to protect the security of PHP applications. By properly configuring and using security logging technology, potential security threats can be discovered and responded to in a timely manner, improving the security and stability of applications. Developers should fully understand and master the security logging technology in PHP to provide more reliable and secure protection for PHP applications.
The above is the detailed content of Analysis of security logging technology in PHP. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
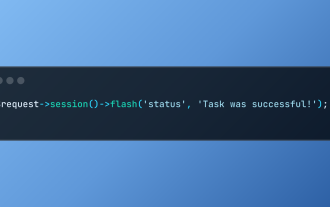 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
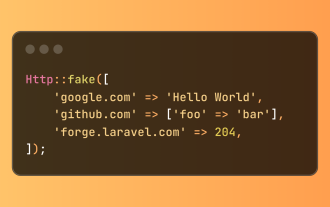 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot
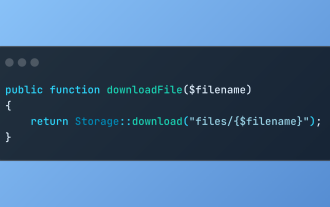 Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
The Storage::download method of the Laravel framework provides a concise API for safely handling file downloads while managing abstractions of file storage. Here is an example of using Storage::download() in the example controller:
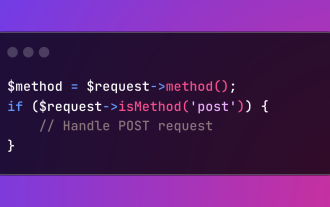 HTTP Method Verification in Laravel
Mar 05, 2025 pm 04:14 PM
HTTP Method Verification in Laravel
Mar 05, 2025 pm 04:14 PM
Laravel simplifies HTTP verb handling in incoming requests, streamlining diverse operation management within your applications. The method() and isMethod() methods efficiently identify and validate request types. This feature is crucial for building






