Analysis of safe file operation technology in PHP
PHP is a scripting language widely used in Web development. As we all know, there are various security risks in the network environment. During PHP file operations, ensuring security is particularly important. This article will provide a detailed analysis of the safe file operation technology in PHP to help developers strengthen the security protection of file operations.
1. File path injection (Path Traversal)
File path injection means that the attacker successfully bypasses the access control of the file system by entering malicious parameters and accesses files that are not within the expected access range. document. To prevent path injection vulnerabilities, we should always effectively validate and filter user-entered paths.
- Filtering user input
After receiving user input, it should be strictly filtered and verified. You can use PHP predefined functions such asrealpath()to standardize the path entered by the user to ensure the legality and correctness of the path. At the same time, you can also use regular expressions to filter user-entered paths to prevent them from containing special characters or path traversal symbols.
Tip:
- Try to use a whitelist to filter user input and only allow expected legal characters and paths.
- Don’t trust the user’s input, be sure to verify and filter the input.
- Use absolute paths
Use absolute paths for file operations whenever possible, rather than relative paths. Relative paths are vulnerable to path injection attacks. Using absolute paths ensures the accuracy and security of file operations. - Restrict file access permissions
Set the file access permissions reasonably and only allow authorized users or scripts to perform file operations. You can use file system permission settings to limit file access permissions to ensure that only authorized users can access and operate files.
2. File Upload Vulnerabilities
File upload vulnerabilities refer to attackers bypassing the security mechanism of the application by maliciously uploading files to execute arbitrary code or tamper with Attacks on website content. In order to prevent file upload vulnerabilities, we should take the following measures:
- Reasonably limit the type and size of uploaded files
During the file upload process, the type and size of uploaded files should be limited. Restrictions can be made by determining the file extension or MIME type to ensure that only safe file types are allowed to be uploaded. At the same time, you should also limit the size of uploaded files to avoid uploading overly large files that may cause server resource occupation and security issues. - Modify file name
During the file upload process, the uploaded file name should be modified to avoid using the original file name. Files can be named with random strings or timestamps to make file names more complex and unguessable. - Storage path security control
When uploading files, the storage path is an important consideration. Files should be stored in a secure directory away from the web root to prevent attackers from attacking the application by accessing the URL of the uploaded file.
3. File Inclusion Vulnerabilities
File inclusion vulnerabilities are a common security problem. Attackers inject malicious code into the URL or user input to achieve Attacks that execute arbitrary code. In order to prevent file inclusion vulnerabilities, we should take the following measures:
- Use absolute paths
When performing file inclusion operations, try to use absolute paths instead of relative paths. Using absolute paths protects you from path injection attacks. - Whitelist filtering user input
User input should be strictly filtered and validated before files are included. Only expected legitimate files are allowed to be included, and untrusted user input should be intercepted or filtered out. - Avoid dynamic construction of file paths
Try to avoid splicing user input into the file path during the file inclusion process. Doing so is vulnerable to path injection attacks and should be avoided if possible.
4. Preventing Error Information Leakage
Error information leakage is a common security vulnerability. Attackers can obtain sensitive information through error information and further attack applications. In order to prevent the leakage of error information, we should take the following measures:
- Close error reporting
In a formal environment, PHP's error reporting should be turned off to avoid the leakage of sensitive information. Error reporting can be turned off by modifying the error_reporting parameter in the php.ini file or using theerror_reporting()function. - Custom error handling
The custom error handling function can process error information to avoid directly exposing sensitive information to attackers. You can register the error handling function into PHP's error handler and automatically call the function when an error occurs.
Summary
During PHP file operations, ensuring security is a very important task. This article provides a detailed analysis of secure file operation technologies in PHP, including file path injection, file upload vulnerabilities, file inclusion vulnerabilities, and techniques to prevent error information leakage. By using these technologies appropriately, we can improve the security of file operations and thus better protect the security of applications and user data.
The above is the detailed content of Analysis of safe file operation technology in PHP. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to safely read and write files using Golang?
Jun 06, 2024 pm 05:14 PM
How to safely read and write files using Golang?
Jun 06, 2024 pm 05:14 PM
Reading and writing files safely in Go is crucial. Guidelines include: Checking file permissions Closing files using defer Validating file paths Using context timeouts Following these guidelines ensures the security of your data and the robustness of your application.
 How to insert content at a specified location in a file using C++?
Jun 04, 2024 pm 03:34 PM
How to insert content at a specified location in a file using C++?
Jun 04, 2024 pm 03:34 PM
In C++, use the ofstream class to insert content at a specified location in a file: open the file and locate the insertion point. use
 More than just 3D Gaussian! Latest overview of state-of-the-art 3D reconstruction techniques
Jun 02, 2024 pm 06:57 PM
More than just 3D Gaussian! Latest overview of state-of-the-art 3D reconstruction techniques
Jun 02, 2024 pm 06:57 PM
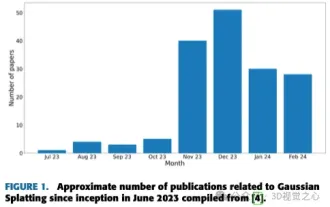
Written above & The author’s personal understanding is that image-based 3D reconstruction is a challenging task that involves inferring the 3D shape of an object or scene from a set of input images. Learning-based methods have attracted attention for their ability to directly estimate 3D shapes. This review paper focuses on state-of-the-art 3D reconstruction techniques, including generating novel, unseen views. An overview of recent developments in Gaussian splash methods is provided, including input types, model structures, output representations, and training strategies. Unresolved challenges and future directions are also discussed. Given the rapid progress in this field and the numerous opportunities to enhance 3D reconstruction methods, a thorough examination of the algorithm seems crucial. Therefore, this study provides a comprehensive overview of recent advances in Gaussian scattering. (Swipe your thumb up
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 Revolutionary GPT-4o: Reshaping the human-computer interaction experience
Jun 07, 2024 pm 09:02 PM
Revolutionary GPT-4o: Reshaping the human-computer interaction experience
Jun 07, 2024 pm 09:02 PM
The GPT-4o model released by OpenAI is undoubtedly a huge breakthrough, especially in its ability to process multiple input media (text, audio, images) and generate corresponding output. This ability makes human-computer interaction more natural and intuitive, greatly improving the practicality and usability of AI. Several key highlights of GPT-4o include: high scalability, multimedia input and output, further improvements in natural language understanding capabilities, etc. 1. Cross-media input/output: GPT-4o+ can accept any combination of text, audio, and images as input and directly generate output from these media. This breaks the limitation of traditional AI models that only process a single input type, making human-computer interaction more flexible and diverse. This innovation helps power smart assistants
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.




