 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 How to set up your CentOS system to prevent the download and execution of malicious code
How to set up your CentOS system to prevent the download and execution of malicious code
How to set up your CentOS system to prevent the download and execution of malicious code
How to set up a CentOS system to prevent the download and execution of malicious code?
The downloading and execution of malicious code is a very important issue in network security. To protect your CentOS system from such attacks, there are some measures you can take. This article will introduce you to some basic security settings and configurations, as well as some commonly used protection technologies and tools.
- Update the operating system and software packages in a timely manner:
Regularly updating the operating system and software packages is an important step to prevent malicious code attacks. CentOS systems occasionally release security patches and updates to fix known vulnerabilities. To achieve this, you can update your system using the following command:
yum update
- Install and configure the firewall:
Firewalls are a key component in protecting your system from cyberattacks. CentOS systems use firewalld as the default firewall manager. The following is a sample code on how to install and configure firewalld:
# 安装firewalld yum install firewalld # 启用firewalld systemctl start firewalld # 设置firewalld开机启动 systemctl enable firewalld # 开启常用的网络服务 firewall-cmd --permanent --add-service=http firewall-cmd --permanent --add-service=https # 重启防火墙 firewall-cmd --reload
The above code will enable firewalld and open HTTP and HTTPS services.
- Prohibit unnecessary services:
On CentOS systems, there are some unnecessary services that may become targets of malicious code attacks. You can reduce your system's attack surface by disabling or stopping these services. The following is a sample code for disabling and stopping services:
# 禁用和停止Telnet服务 systemctl disable telnet systemctl stop telnet # 禁用和停止FTP服务 systemctl disable vsftpd systemctl stop vsftpd # 禁用和停止无线服务 systemctl disable NetworkManager systemctl stop NetworkManager # 禁用和停止不必要的数据库服务(例如MySQL) systemctl disable mysqld systemctl stop mysqld
Other unnecessary services can be disabled and stopped according to actual needs.
- Use security access control:
Access control is a method of restricting system access. Access control can be modified using the following configuration file:
# 修改/etc/hosts.allow文件以允许特定的主机访问 echo "sshd: 192.168.1.0/255.255.255.0" >> /etc/hosts.allow # 修改/etc/hosts.deny文件以阻止特定的主机访问 echo "sshd: ALL" >> /etc/hosts.deny
The above code will allow only hosts with IP address 192.168.1.0/24 to access the sshd service and block access to all other hosts.
- Use secure source control:
Source control is a way to protect your system from malware and malicious code. You can install and configure yum-cron to automatically check and update packages using the following commands:
# 安装yum-cron yum install yum-cron # 启用yum-cron systemctl start yum-cron # 设置yum-cron开机启动 systemctl enable yum-cron
The above code will install yum-cron and configure it to check and update packages regularly.
Summary:
It is crucial to prevent the download and execution of malicious code in CentOS systems. System security can be greatly improved by promptly updating the operating system and software packages, installing and configuring firewalls, disabling unnecessary services, and using access control and secure source control. The above are some basic security settings and configuration examples, I hope they will be helpful to you. However, please note that network security is an ever-evolving field that requires continuous learning and staying up to date with the latest security technologies and tools to protect systems from malicious code.
The above is the detailed content of How to set up your CentOS system to prevent the download and execution of malicious code. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to use magnet links
Feb 18, 2024 am 10:02 AM
How to use magnet links
Feb 18, 2024 am 10:02 AM
Magnet link is a link method for downloading resources, which is more convenient and efficient than traditional download methods. Magnet links allow you to download resources in a peer-to-peer manner without relying on an intermediary server. This article will introduce how to use magnet links and what to pay attention to. 1. What is a magnet link? A magnet link is a download method based on the P2P (Peer-to-Peer) protocol. Through magnet links, users can directly connect to the publisher of the resource to complete resource sharing and downloading. Compared with traditional downloading methods, magnetic
 How to download episodes of Hongguo short drama
Mar 11, 2024 pm 09:16 PM
How to download episodes of Hongguo short drama
Mar 11, 2024 pm 09:16 PM
Hongguo Short Play is not only a platform for watching short plays, but also a treasure trove of rich content, including novels and other exciting content. This is undoubtedly a huge surprise for many users who love reading. However, many users still don’t know how to download and watch these novels in Hongguo Short Play. In the following, the editor of this website will provide you with detailed downloading steps. I hope it can help everyone in need. Partners. How to download and watch the Hongguo short play? The answer: [Hongguo short play] - [Audio book] - [Article] - [Download]. Specific steps: 1. First open the Hongguo Short Drama software, enter the homepage and click the [Listen to Books] button at the top of the page; 2. Then on the novel page we can see a lot of article content, here
 What should I do if I download other people's wallpapers after logging into another account on wallpaperengine?
Mar 19, 2024 pm 02:00 PM
What should I do if I download other people's wallpapers after logging into another account on wallpaperengine?
Mar 19, 2024 pm 02:00 PM
When you log in to someone else's steam account on your computer, and that other person's account happens to have wallpaper software, steam will automatically download the wallpapers subscribed to the other person's account after switching back to your own account. Users can solve this problem by turning off steam cloud synchronization. What to do if wallpaperengine downloads other people's wallpapers after logging into another account 1. Log in to your own steam account, find cloud synchronization in settings, and turn off steam cloud synchronization. 2. Log in to someone else's Steam account you logged in before, open the Wallpaper Creative Workshop, find the subscription content, and then cancel all subscriptions. (In case you cannot find the wallpaper in the future, you can collect it first and then cancel the subscription) 3. Switch back to your own steam
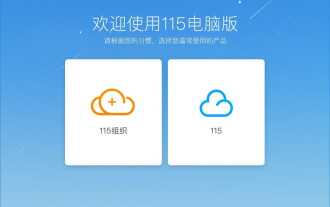 How to download links starting with 115://? Download method introduction
Mar 14, 2024 am 11:58 AM
How to download links starting with 115://? Download method introduction
Mar 14, 2024 am 11:58 AM
Recently, many users have been asking the editor, how to download links starting with 115://? If you want to download links starting with 115://, you need to use the 115 browser. After you download the 115 browser, let's take a look at the download tutorial compiled by the editor below. Introduction to how to download links starting with 115:// 1. Log in to 115.com, download and install the 115 browser. 2. Enter: chrome://extensions/ in the 115 browser address bar, enter the extension center, search for Tampermonkey, and install the corresponding plug-in. 3. Enter in the address bar of 115 browser: Grease Monkey Script: https://greasyfork.org/en/
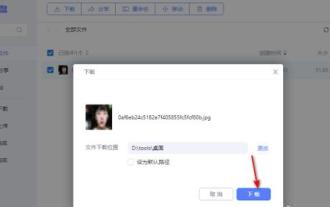 How to download files from 123 cloud disk
Feb 23, 2024 pm 08:58 PM
How to download files from 123 cloud disk
Feb 23, 2024 pm 08:58 PM
123 cloud disk can download many files, so how to download files specifically? Users can select the file they want to download and click to download, or right-click the file and select download. This introduction to the method of downloading files from 123 cloud disk can tell you how to download it specifically. Friends who don’t know much about it should hurry up and take a look! How to download files from 123 cloud disk 1. First open the software, click on the software that needs to be downloaded, and then there will be a download button on it. 2. Or right-click the software and you can see the download button in the list. 3. There will be a download window, select the location to download. 4. After selecting, click Download to download these files.
 Introduction to how to download and install the superpeople game
Mar 30, 2024 pm 04:01 PM
Introduction to how to download and install the superpeople game
Mar 30, 2024 pm 04:01 PM
The superpeople game can be downloaded through the steam client. The size of this game is about 28G. It usually takes one and a half hours to download and install. Here is a specific download and installation tutorial for you! New method to apply for global closed testing 1) Search for "SUPERPEOPLE" in the Steam store (steam client download) 2) Click "Request access to SUPERPEOPLE closed testing" at the bottom of the "SUPERPEOPLE" store page 3) After clicking the request access button, The "SUPERPEOPLECBT" game can be confirmed in the Steam library 4) Click the install button in "SUPERPEOPLECBT" and download
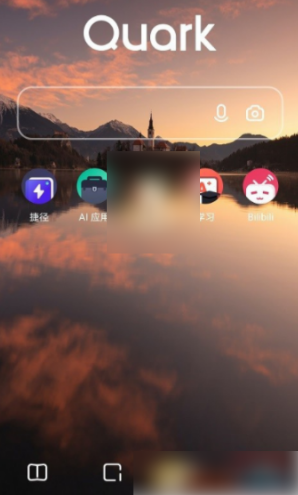 How to download Quark network disk to local? How to save files downloaded from Quark Network Disk back to the local computer
Mar 13, 2024 pm 08:31 PM
How to download Quark network disk to local? How to save files downloaded from Quark Network Disk back to the local computer
Mar 13, 2024 pm 08:31 PM
Many users need to download files when using Quark Network Disk, but we want to save them locally, so how to set this up? Let this site introduce to users in detail how to save files downloaded from Quark Network Disk back to the local computer. How to save files downloaded from Quark network disk back to your local computer 1. Open Quark, log in to your account, and click the list icon. 2. After clicking the icon, select the network disk. 3. After entering Quark Network Disk, click My Files. 4. After entering My Files, select the file you want to download and click the three-dot icon. 5. Check the file you want to download and click Download.
 How to download Baidu Netdisk files
Feb 23, 2024 pm 06:20 PM
How to download Baidu Netdisk files
Feb 23, 2024 pm 06:20 PM
How to download Baidu Netdisk files? You can download the required files in Baidu Netdisk, but most users don’t know how to download files in Baidu Netdisk. Next is the diagram of how to download Baidu Netdisk files brought by the editor to users. Text tutorial, interested users come and take a look! How to download Baidu Netdisk files 1. First open Baidu Netdisk and find the file that needs to be downloaded; 2. Then click the [Download] button in the toolbar as shown below; 3. Finally, a window will pop up, select [Download] to complete. File downloads can be opened at any time.



