Use it every day! Do you know what HASH is?
Have you ever used HashMap? So have you seriously understood what Hash is? This article will take you through an in-depth study of the Hash algorithm from a principle level.
1. The concept of hashing
The main idea of the hashing method is to determine the storage address of the node based on the key code value: based on the key code The value K is an independent variable. Through a certain functional relationship h(K) (called a hash function), the corresponding function value is calculated. This value is interpreted as the storage address of the node, and the node is stored in this storage. in the unit. When retrieving, use the same method to calculate the address, and then go to the corresponding unit to get the node you are looking for. Nodes can be quickly retrieved through hashing. Hash (also called "hash") is an important storage method and a common retrieval method.
The storage structure constructed according to the hash storage method is called a hash table (hash table). A position in the hash table is called a slot. The core of hashing technology is the hash function. For any given dynamic lookup table DL, if an "ideal" hash function h and the corresponding hash table HT are selected, then for each data element X in DL. The function value h (X.key) is the storage location of X in the hash table HT. Data element X will be placed at this position when inserting (or creating a table), and will also be searched at this position when retrieving X. The storage location determined by the hash function is called the hash address. Therefore, the core of hashing is: the hash function determines the corresponding relationship between the key code value (X.key) and the hash address h (X.key). Through this relationship, organizational storage and retrieval are realized.
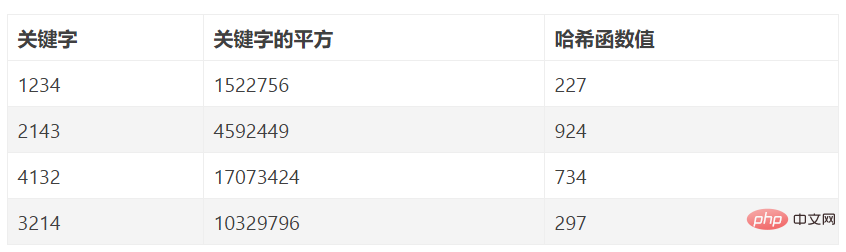
Generally, the storage space of the hash table is a one-dimensional array HT[M], and the hash address is the subscript of the array. The goal of designing a hashing method is to design a certain hash function h, 0<=h(K) In the following discussion, we assume that we are dealing with key codes with integer values. Otherwise, we can always create a key code with a normal value. One-to-one correspondence between integers, thereby converting the retrieval of the key into a retrieval of the corresponding positive integer; at the same time, it is further assumed that the value of the hash function falls between 0 and M-1. The principles for selecting a hash function are: the operation is as simple as possible; the value range of the function must be within the range of the hash table; the nodes should be distributed evenly as much as possible, that is, try to make different keys have different hash function values. Various factors need to be considered: key length, hash table size, key distribution, record retrieval frequency, etc. Below we introduce several commonly used hash functions. #As the name suggests, division by remainder method is to divide the key code x by M (often taking the length of the hash table), And take the remainder as the hash address. The remainder method is almost the simplest hashing method, and the hash function is: h(x) = x mod M. When using this method, first multiply the key code by a constant A (0< A < 1), extract the decimal part of the product. Then, multiply this value by the integer n, round down the result, and use it as the hash address. The hash function is: hash (key) = _LOW(n × (A × key % 1)). Among them, "A × key % 1" means taking the decimal part of A × key, that is: A × key % 1 = A × key - _LOW(A × key), and _LOW(X) means taking the integer part of X. For example: To construct a hash table with the number of data elements n=80 and the hash length m=100. Without loss of generality, we only give 8 keywords for analysis here. The 8 keywords are as follows: K1=61317602 K2=61326875 K3=62739628 K4=61343634 K5=62706815 K6=62774638 K7=61381262 K8=61394220 Analysis of the above 8 keywords shows that the values of the 1st, 2nd, 3rd, and 6th digits from left to right of the keywords are relatively concentrated and should not be used as Haha. Hash address, the remaining 4th, 5th, 7th, and 8th bits have even values, and two of them can be selected as the hash address. Suppose the last two digits are selected as the hash address, then the hash addresses of these eight keywords are: 2, 75, 28, 34, 15, 38, 62, 20. This method is suitable for: being able to estimate in advance the frequency of occurrence of various numbers on each digit of all keywords. Consider the key value as a number in another base system and then convert it into the original base number , and then select several of them as hash addresses. Example Hash(80127429)=(80127429)13=8137 0136 1135 2134 7133 4132 2*131 9=(502432641)10 If you take the middle three digits as the hash value, you get Hash(80127429)=432
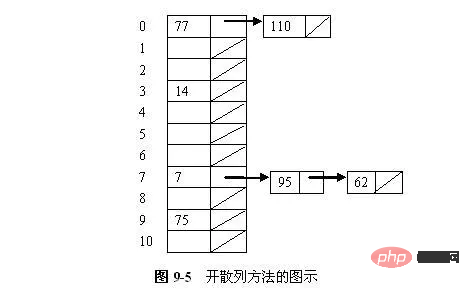
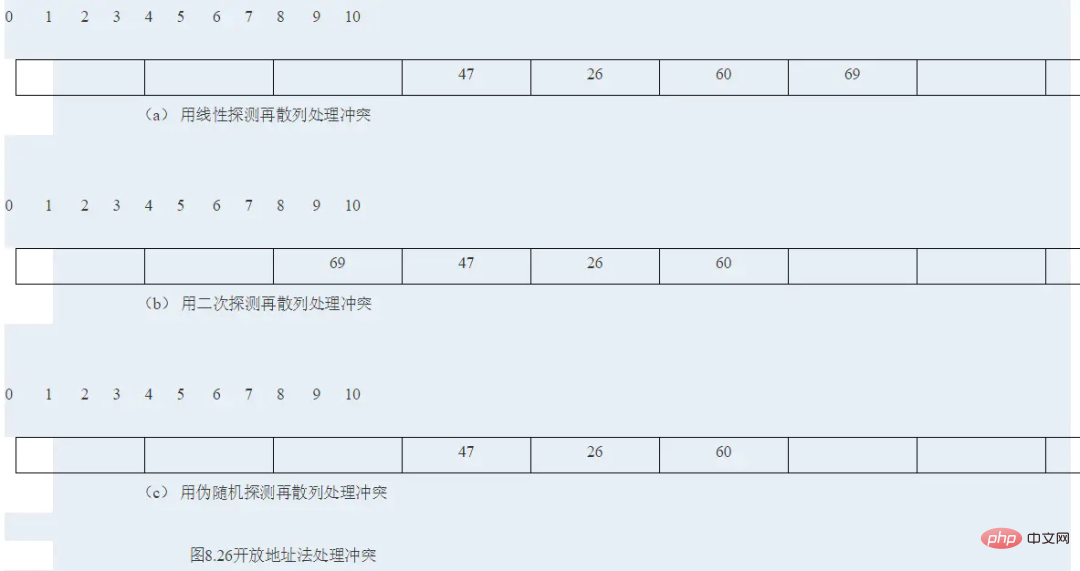
In order to obtain a good hash function, several methods can be used in combination, such as changing the base first, then folding or squaring, etc. As long as the hash is uniform, you can piece it together at will. #Sometimes the key code contains many digits, and it is too complicated to use the square-centering method, then you can The key code is divided into several parts with the same number of digits (the number of digits in the last part can be different), and then the superposition sum of these parts (carry out) is taken as the hash address. This method is called the folding method. is divided into: Although the goal of the hash function is to minimize conflicts, in fact conflicts are unavoidable. Therefore, we must look into conflict resolution strategies. Conflict resolution techniques can be divided into two categories: open hashing (also known as zipper method, separate chaining) and closed hashing method (closed hashing, also known as open address method, open addressing). The difference between these two methods is that the open hashing method stores the colliding key outside the main hash table, while the closed hashing method stores the colliding key in another slot in the table. (1)Zipper method A kind of hashing method The simple form is to define each slot in the hash table as the head of a linked list. All records that hash to a specific slot are put into the linked list for that slot. Figure 9-5 illustrates an open hash table in which each slot stores a record and a pointer to the rest of the linked list. These 7 numbers are stored in a hash table with 11 slots, and the hash function used is h(K) = K mod 11. The insertion order of numbers is 77, 7, 110, 95, 14, 75 and 62. There are 2 values hashed to slot 0, 1 value hashed to slot 3, 3 values hashed to slot 7, and 1 value hashed to slot 9. The closed hashing method combines all Records are stored directly in the hash table. Each record key key has a base position calculated by a hash function, that is, h(key). If a key is to be inserted and another record already occupies the base position of R (a collision occurs), then R is stored at another address in the table, and the conflict resolution policy determines which address it is. The basic idea of closed hash table conflict resolution is: when a conflict occurs, use a certain method to generate a hash address sequence d0, d1, d2,...di,...dm for the key K -1. Among them, d0=h (K) is called the base address home position of K; all di (0< i< m) are subsequent hash addresses. When K is inserted, if the node at the base address is already occupied by other data elements, it will be probed in sequence according to the above address sequence, and the first open free position di found will be used as the storage location of K; if all subsequent hashes No addresses are free, indicating that the closed hash table is full and an overflow is reported. Correspondingly, when retrieving K, the sequence of successor addresses with the same value will be searched in sequence, and the position di will be returned when the retrieval is successful; if an open free address is encountered when retrieving along the probing sequence, it means that there is no key to be searched in the table code. When deleting K, we also search sequentially according to the sequence of successor addresses with the same value. If we find that a certain position di has the K value, then delete the data element at the position di (the deletion operation actually just marks the node for deletion); If an open free address is encountered, it means that there is no key to be deleted in the table. Therefore, for closed hash tables, the method of constructing a sequence of subsequent hash addresses is the method of handling conflicts. Different methods of forming probes lead to different methods of resolving conflicts. Below are several common construction methods. (1) Linear detection method Treat the hash table as a ring table. If a conflict occurs at the base address d (i.e. h(K)=d) , then the following address units are explored in sequence: d 1, d 2,..., M-1, 0, 1,..., d-1 until a free address is found or the key code is found to the node of key. Of course, if you return to address d after searching along the probing sequence, it means failure whether you are doing an insertion operation or a retrieval operation. The probe function for simple linear probe is: p(K,i) = i Example 9.7 It is known that a set of key codes is (26, 36, 41, 38, 44, 15, 68, 12, 06, 51, 25), the length of the hash table M = 15, and the linear exploration method is used to resolve the conflict structure A hash table of this set of keys. Because n=11, use the remainder method to construct a hash function and select the largest prime number P=13 less than M. Then the hash function is: h(key) = key. Insert each node in order: 26: h(26) = 0, 36: h(36) = 10, 41: h(41) = 2, 38: h(38) = 12, 44: h(44) = 5. When 15 is inserted, its hash address is 2. Since 2 is already occupied by the element with key code 41, it needs to be probed. According to the sequential probing method, it is obvious that 3 is an open free address, so it can be placed in unit 3. Similarly, 68 and 12 can be placed in units 4 and 13 respectively. (2) Secondary exploration method The basic idea of the secondary exploration method is: The generated subsequent hash addresses are not consecutive, but skipped to leave room for subsequent data elements and thus reduce aggregation. The detection sequence of the secondary detection method is: 12, -12, 22, -22,... etc. That is to say, when a conflict occurs, the synonyms are hashed back and forth at both ends of the first address. The formula for finding the next open address is: ##(3) Random exploration method (4)Double hash detection method Both pseudo-random probing and secondary probing can eliminate the problem of basic aggregation - that is, key codes with different base addresses, and some segments of their probing sequences overlap. However, if two keys hash to the same base address, the same probe sequence will still be obtained using both methods, and aggregation will still occur. This is because the probing sequence generated by pseudo-random probing and secondary probing is only a function of the base address, not a function of the original key value. This problem is called secondary clustering. In order to avoid secondary aggregation, we need to make the exploration sequence a function of the original key value rather than a function of the base position. The double hash detection method uses the second hash function as a constant, skips the constant term each time, and performs linear detection.
2. Hash function
1. Division by remainder method
2. Multiply remainder method
Since integer division usually runs slower than multiplication, consciously avoid using the remainder Legal operations can improve the running time of hashing algorithms. The specific implementation of the square-middle method is to first find the square value of the key code to expand the difference between similar numbers, and then take the middle few digits (often binary bits) according to the length of the table as the hash function value. Because the middle digits of a product are related to each digit of the multiplier, the resulting hash address is more uniform.
Assume that each keyword in the keyword set is It consists of s digits (u1, u2, …, us), analyzes the entire keyword set, and extracts several evenly distributed bits or their combination as addresses. The digital analysis method is a method of taking some digital bits with relatively uniform values in the data element keywords as the hash address. That is, when the keyword has a lot of digits, you can analyze the bits of the keyword and discard the unevenly distributed bits as a hash value. It is only suitable when all keyword values are known. By analyzing the distribution, the keyword value range is converted into a smaller keyword value range.
5. Base conversion method
6. Folding method
3. Conflict resolution strategy
1. Separated linked list method
2. Closed hashing method (open address method)


The above is the detailed content of Use it every day! Do you know what HASH is?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Top 4 JavaScript Frameworks in 2025: React, Angular, Vue, Svelte
Mar 07, 2025 pm 06:09 PM
Top 4 JavaScript Frameworks in 2025: React, Angular, Vue, Svelte
Mar 07, 2025 pm 06:09 PM
This article analyzes the top four JavaScript frameworks (React, Angular, Vue, Svelte) in 2025, comparing their performance, scalability, and future prospects. While all remain dominant due to strong communities and ecosystems, their relative popul
 How does Java's classloading mechanism work, including different classloaders and their delegation models?
Mar 17, 2025 pm 05:35 PM
How does Java's classloading mechanism work, including different classloaders and their delegation models?
Mar 17, 2025 pm 05:35 PM
Java's classloading involves loading, linking, and initializing classes using a hierarchical system with Bootstrap, Extension, and Application classloaders. The parent delegation model ensures core classes are loaded first, affecting custom class loa
 How do I implement multi-level caching in Java applications using libraries like Caffeine or Guava Cache?
Mar 17, 2025 pm 05:44 PM
How do I implement multi-level caching in Java applications using libraries like Caffeine or Guava Cache?
Mar 17, 2025 pm 05:44 PM
The article discusses implementing multi-level caching in Java using Caffeine and Guava Cache to enhance application performance. It covers setup, integration, and performance benefits, along with configuration and eviction policy management best pra
 Spring Boot SnakeYAML 2.0 CVE-2022-1471 Issue Fixed
Mar 07, 2025 pm 05:52 PM
Spring Boot SnakeYAML 2.0 CVE-2022-1471 Issue Fixed
Mar 07, 2025 pm 05:52 PM
This article addresses the CVE-2022-1471 vulnerability in SnakeYAML, a critical flaw allowing remote code execution. It details how upgrading Spring Boot applications to SnakeYAML 1.33 or later mitigates this risk, emphasizing that dependency updat
 Node.js 20: Key Performance Boosts and New Features
Mar 07, 2025 pm 06:12 PM
Node.js 20: Key Performance Boosts and New Features
Mar 07, 2025 pm 06:12 PM
Node.js 20 significantly enhances performance via V8 engine improvements, notably faster garbage collection and I/O. New features include better WebAssembly support and refined debugging tools, boosting developer productivity and application speed.
 Iceberg: The Future of Data Lake Tables
Mar 07, 2025 pm 06:31 PM
Iceberg: The Future of Data Lake Tables
Mar 07, 2025 pm 06:31 PM
Iceberg, an open table format for large analytical datasets, improves data lake performance and scalability. It addresses limitations of Parquet/ORC through internal metadata management, enabling efficient schema evolution, time travel, concurrent w
 How can I implement functional programming techniques in Java?
Mar 11, 2025 pm 05:51 PM
How can I implement functional programming techniques in Java?
Mar 11, 2025 pm 05:51 PM
This article explores integrating functional programming into Java using lambda expressions, Streams API, method references, and Optional. It highlights benefits like improved code readability and maintainability through conciseness and immutability
 How to Share Data Between Steps in Cucumber
Mar 07, 2025 pm 05:55 PM
How to Share Data Between Steps in Cucumber
Mar 07, 2025 pm 05:55 PM
This article explores methods for sharing data between Cucumber steps, comparing scenario context, global variables, argument passing, and data structures. It emphasizes best practices for maintainability, including concise context use, descriptive






