 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 What are the log processing and monitoring methods for PHP packaged deployment?
What are the log processing and monitoring methods for PHP packaged deployment?
What are the log processing and monitoring methods for PHP packaged deployment?
PHP, as a commonly used server-side programming language, is widely used in the development of Web applications. In the development and deployment process of web applications, log processing and monitoring are very important. This article will introduce some commonly used log processing and monitoring methods in PHP packaging and deployment, and attach code examples.
1. Log processing method
- Using log libraries
In PHP, we can easily introduce some excellent log libraries Perform log processing. For example, the commonly used Monolog class library provides rich logging, formatting and storage functions, which can easily meet various logging needs. The following is a sample code that uses the Monolog class library to record logs:
use MonologLogger;
use MonologHandlerStreamHandler;
// 创建一个日志记录器
$log = new Logger('name');
// 创建一个StreamHandler实例,将日志写入文件
$log->pushHandler(new StreamHandler('/path/to/your.log', Logger::WARNING));
// 记录一条警告级别的日志
$log->warning('Foo');- Customized log processing function
In addition to using the logging class library, we can also customize logs Handle functions to log. The following is a sample code for a simple custom log processing function:
function writeLog($message) {
// 打开日志文件
$file = fopen('/path/to/your.log', 'a');
// 记录日志
fwrite($file, date('Y-m-d H:i:s') . ' ' . $message . "
");
// 关闭日志文件
fclose($file);
}
// 使用自定义日志处理函数记录日志
writeLog('This is a log message.');2. Monitoring method
- Use monitoring tools
Package and deploy in PHP , you can use some monitoring tools to monitor the running status and performance indicators of the application. For example, Prometheus is a popular open source monitoring solution that can collect application metric data through Exporter. The following is a sample code that uses Prometheus and Guzzle libraries to monitor web application performance:
use GuzzleHttpClient;
$client = new Client();
// 发送一个HTTP请求,并记录请求时间
$start = microtime(true);
$response = $client->get('http://example.com');
$end = microtime(true);
// 计算请求时间
$duration = $end - $start;
// 将请求时间写入Prometheus的Exporter
$client->post('http://localhost:9091/metrics/job/myapp', [
'body' => "myapp_request_duration_seconds $duration
"
]);- Custom monitoring function
In addition to using monitoring tools, we can also customize it Define monitoring functions to collect application running status and performance metrics. The following is a sample code of a simple custom monitoring function:
function monitor($metric, $value) {
// 将指标和值写入数据库或其他存储介质
$pdo = new PDO("mysql:host=localhost;dbname=myapp", "username", "password");
$pdo->exec("INSERT INTO metrics (metric, value, timestamp) VALUES ('$metric', '$value', NOW())");
}
// 使用自定义监控函数收集应用程序的指标数据
monitor('request_count', 1);To sum up, the commonly used log processing methods in PHP packaging and deployment include using log libraries and custom log processing functions. Common monitoring methods There are monitoring tools and custom monitoring functions. According to the actual needs and scale of the project, choosing a suitable method to process logs and monitor the running status and performance indicators of the application can help us better package, deploy and manage PHP programs.
The above is the detailed content of What are the log processing and monitoring methods for PHP packaged deployment?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Reasons why tables are locked in Oracle and how to deal with them
Mar 03, 2024 am 09:36 AM
Reasons why tables are locked in Oracle and how to deal with them
Mar 03, 2024 am 09:36 AM
Reasons for table locking in Oracle and how to deal with it In Oracle database, table locking is a common phenomenon, and there are many reasons for table locking. This article will explore some common reasons why tables are locked, and provide some processing methods and related code examples. 1. Types of locks In the Oracle database, locks are mainly divided into shared locks (SharedLock) and exclusive locks (ExclusiveLock). Shared locks are used for read operations, allowing multiple sessions to read the same resource at the same time.
 JSON processing methods and implementation in C++
Aug 21, 2023 pm 11:58 PM
JSON processing methods and implementation in C++
Aug 21, 2023 pm 11:58 PM
JSON is a lightweight data exchange format that is easy to read and write, as well as easy for machines to parse and generate. Using JSON format makes it easy to transfer data between various systems. In C++, there are many open source JSON libraries for JSON processing. This article will introduce some commonly used JSON processing methods and implementations in C++. JSON processing methods in C++ RapidJSON RapidJSON is a fast C++ JSON parser/generator that provides DOM, SAX and
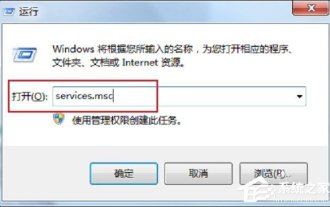 How to handle the unavailable rpc server in Win7 system
Jul 19, 2023 pm 04:57 PM
How to handle the unavailable rpc server in Win7 system
Jul 19, 2023 pm 04:57 PM
In the process of using computers, we often encounter some problems, some of which can make people overwhelmed. Some users encounter this problem. When they turn on the computer and use the printer, a message that the RPC server is unavailable pops up. What happened? what do I do? In response to this problem, let us share the solution to Win7rpc server being unavailable. 1. Press the Win+R keys to open Run, and enter services.msc in the Run input box. 2. After entering the service list, find the RemoteProcedureCall(RPC)Locator service. 3. Select the service and double-click. The default state is as shown below: 4. Change the startup type of the RPCLoader service to automatic
 How to deal with array out-of-bounds problems in C++ development
Aug 21, 2023 pm 10:04 PM
How to deal with array out-of-bounds problems in C++ development
Aug 21, 2023 pm 10:04 PM
How to deal with the array out-of-bounds problem in C++ development In C++ development, array out-of-bounds is a common error, which can lead to program crashes, data corruption and even security vulnerabilities. Therefore, correctly handling array out-of-bounds problems is an important part of ensuring program quality. This article will introduce some common processing methods and suggestions to help developers avoid array out-of-bounds problems. First, it is key to understand the cause of the array out-of-bounds problem. Array out-of-bounds refers to an index that exceeds its definition range when accessing an array. This usually happens in the following scenario: Negative numbers are used when accessing the array
 How to use PHP functions to process large amounts of data
Jun 16, 2023 am 10:45 AM
How to use PHP functions to process large amounts of data
Jun 16, 2023 am 10:45 AM
With the development of the Internet, we are exposed to large amounts of data every day, which needs to be stored, processed and analyzed. PHP is a server-side scripting language that is widely used today and is also used for large-scale data processing. When processing large-scale data, it is easy to face memory overflow and performance bottlenecks. This article will introduce how to use PHP functions to process large amounts of data. 1. Turn on memory limit By default, PHP’s memory limit size is 128M, which may become a problem when processing large amounts of data. To handle larger
 What to do if MySQL connection error 1017 occurs?
Jun 30, 2023 am 11:57 AM
What to do if MySQL connection error 1017 occurs?
Jun 30, 2023 am 11:57 AM
How to deal with MySQL connection error 1017? MySQL is an open source relational database management system that is widely used in website development and data storage. However, when using MySQL, you may encounter a variety of errors. One of the common errors is connection error 1017 (MySQL error code 1017). Connection error 1017 indicates a database connection failure, usually caused by an incorrect username or password. When MySQL fails to authenticate using the provided username and password
 Steps to solve the problem of high memory usage in win7
Dec 27, 2023 pm 10:27 PM
Steps to solve the problem of high memory usage in win7
Dec 27, 2023 pm 10:27 PM
The memory space of the computer depends on the smoothness of the computer's operation. Over time, the memory will become full and the usage will be too high, which will cause the computer to become delayed. So how to solve it? Let’s take a look at the solutions below. What to do if Windows 7 memory usage is too high: Method 1. Disable automatic updates 1. Click "Start" to open "Control Panel" 2. Click "Windows Update" 3. Click "Change Settings" on the left 4. Select the "Never Check for Updates" method 2. Software deletion: Uninstall all useless software. Method 3: Close processes and end all useless processes, otherwise there will be many advertisements in the background filling up the memory. Method 4: Disable services. Many useless services in the system are also closed, which not only ensures security but also saves space.
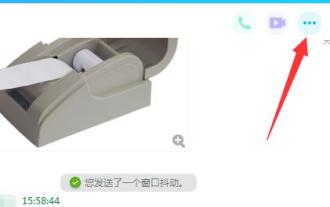 How to solve QQ remote desktop connection problems
Dec 26, 2023 am 11:55 AM
How to solve QQ remote desktop connection problems
Dec 26, 2023 am 11:55 AM
QQ is a chat software produced by Tencent. Almost everyone has a QQ account and can remotely connect and operate when chatting. However, some users encounter the problem of being unable to connect, so what should they do? Let’s take a look below. What to do if QQ Remote Desktop cannot connect: 1. Open the chat interface, click the "..." icon in the upper right corner 2. Select the red computer icon and click "Settings" 3. Click "Set Permissions—>Remote Desktop" 4. Check "Allow Remote Desktop to connect to this computer"



