 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How to use encryption and decryption techniques to protect sensitive data in PHP applications
How to use encryption and decryption techniques to protect sensitive data in PHP applications
How to use encryption and decryption techniques to protect sensitive data in PHP applications
How to use encryption and decryption technology to protect sensitive data in PHP applications
Introduction:
With the development of the Internet and the popularity of smart devices, more and more individuals and institutions use PHP to develop applications program. These applications usually contain a large amount of sensitive data, such as users' personal information, login credentials, etc. Protecting the security of this sensitive data is critical to the stable operation of applications and the protection of user privacy. This article will introduce how to use encryption and decryption technology to protect sensitive data in PHP applications.
1. Understanding Encryption and Decryption Technology
Encryption is the process of converting ordinary data into unreadable ciphertext, while decryption is the process of restoring ciphertext to readable plaintext. Encryption and decryption technology can protect the confidentiality of data, and even if the data is illegally obtained, the actual content cannot be obtained. In PHP applications, commonly used encryption technologies include symmetric encryption and asymmetric encryption.
Symmetric encryption uses the same key for encryption and decryption operations. It is fast and suitable for processing large amounts of data. The sample code is as follows:
function encrypt($data, $key) {
$iv = openssl_random_pseudo_bytes(openssl_cipher_iv_length('aes-256-cbc'));
$encrypted = openssl_encrypt($data, 'aes-256-cbc', $key, 0, $iv);
return base64_encode($iv . $encrypted);
}
function decrypt($data, $key) {
$data = base64_decode($data);
$iv = substr($data, 0, 16);
$encrypted = substr($data, 16);
return openssl_decrypt($encrypted, 'aes-256-cbc', $key, 0, $iv);
}
$key = "ThisIsASecretKey";
$data = "Sensitive Data";
$encryptedData = encrypt($data, $key);
$decryptedData = decrypt($encryptedData, $key);
echo "加密后的数据:" . $encryptedData . "<br/>";
echo "解密后的数据:" . $decryptedData;Asymmetric encryption uses a pair of keys, the public key is used to encrypt data, and the private key is used to decrypt data. Asymmetric encryption is more secure, but slower and suitable for processing small amounts of data or key exchange. The sample code is as follows:
function encrypt($data, $publicKey) {
openssl_public_encrypt($data, $encrypted, $publicKey);
return base64_encode($encrypted);
}
function decrypt($data, $privateKey) {
$data = base64_decode($data);
openssl_private_decrypt($data, $decrypted, $privateKey);
return $decrypted;
}
$publicKey = openssl_pkey_get_public(file_get_contents('public_key.pem'));
$privateKey = openssl_pkey_get_private(file_get_contents('private_key.pem'));
$data = "Sensitive Data";
$encryptedData = encrypt($data, $publicKey);
$decryptedData = decrypt($encryptedData, $privateKey);
echo "加密后的数据:" . $encryptedData . "<br/>";
echo "解密后的数据:" . $decryptedData;2. Best practices for protecting sensitive data
- Encrypt and store sensitive data:
When storing sensitive data in the database, first encrypt it and then store it. For example, the user's password can be encrypted and stored using a hash algorithm, and then compared with the hash algorithm during verification. - Use HTTPS protocol to transmit sensitive data:
When transmitting sensitive data between users and applications, try to use HTTPS protocol and encrypt data transmission through SSL/TLS to avoid data being eavesdropped or hijacked and ensure data confidentiality and integrity. - Regularly update keys:
Keys are an important part of ensuring data security. Regularly updating keys can increase the confidentiality of data. Regularly changing keys reduces the risk of key compromise and protects data from future attacks. - Control the access rights of the key:
Strictly control the access rights of the key and only allow trusted personnel to access the key to prevent the key from being obtained by criminals and causing data leakage.
Conclusion:
Protecting the security of sensitive data is an aspect that must be paid attention to during the development of PHP applications. By using encryption and decryption techniques, and following best practices to protect sensitive data, you can reduce the risk of data breaches and improve application security and stability. When using encryption and decryption technology, it is necessary to select appropriate encryption algorithms and random keys according to the actual situation, and reasonably manage the storage and use of keys. At the same time, measures such as regularly reviewing and updating encryption algorithms, keys, and access rights are also necessary. Only by continuously paying attention to and improving data security awareness can we better protect sensitive data.
The above is the detailed content of How to use encryption and decryption techniques to protect sensitive data in PHP applications. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Decrypting HTTP status code 460: Why does this error occur? Introduction: In daily network use, we often encounter various error prompts, including HTTP status codes. These status codes are a mechanism defined by the HTTP protocol to indicate the processing of a request. Among these status codes, there is a relatively rare error code, namely 460. This article will delve into this error code and explain why this error occurs. Definition of HTTP status code 460: First, we need to understand the basics of HTTP status code
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 How to set up word decryption
Mar 20, 2024 pm 04:36 PM
How to set up word decryption
Mar 20, 2024 pm 04:36 PM
In today's work environment, everyone's awareness of confidentiality is getting stronger and stronger, and encryption operations are often performed to protect files when using software. Especially for key documents, the awareness of confidentiality should be increased, and the security of documents should be given top priority at all times. So I don’t know how well everyone understands word decryption. How to operate it specifically? Today we will actually show you the process of word decryption through the explanation below. Friends who need to learn word decryption knowledge should not miss today's course. A decryption operation is first required to protect the file, which means that the file is processed as a protective document. After doing this to a file, a prompt pops up when you open the file again. The way to decrypt the file is to enter the password, so you can directly
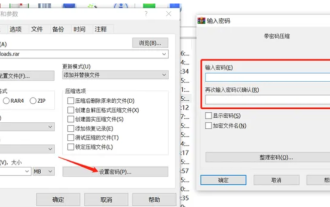 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 Decrypting the tricks added by the PyCharm interpreter
Feb 21, 2024 pm 03:33 PM
Decrypting the tricks added by the PyCharm interpreter
Feb 21, 2024 pm 03:33 PM
Decrypting the tricks added by the PyCharm interpreter PyCharm is the integrated development environment (IDE) preferred by many Python developers, and it provides many powerful features to improve development efficiency. Among them, the setting of the interpreter is an important part of PyCharm. Correctly setting the interpreter can help developers run the code smoothly and debug the program. This article will introduce some techniques for decrypting the PyCharm interpreter additions, and combine it with specific code examples to show how to correctly configure the interpreter. Adding and selecting interpreters in Py
 How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to de-encrypt videos on EZVIZ Cloud: There are many ways to de-encrypt videos on EZVIZ Cloud, one of which is by using the EZVIZ Cloud Mobile App. Users only need to enter the device list, select the camera to be decrypted and enter the device details page. On the device details page, find the "Settings" option, and then select "Video Encryption" to make relevant settings. In the video encryption settings interface, you can choose the option to turn off video encryption, and save the settings to complete the decryption operation. This simple step allows users to easily decrypt videos and improves the convenience of using the camera. If you use the computer client of EZVIZ Cloud, you can also cancel video encryption through similar steps. Just log in and select the corresponding camera, enter the device details interface, and then look for video addition in the settings.
 Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Original author: Meteor, ChainCatcher Original editor: Marco, ChainCatcher Recently, the full-chain interoperability protocol Analog has entered the public eye with the disclosure of US$16 million in financing. Investment institutions include TribeCapital, NGCVentures, Wintermute, GSR, NEAR, OrangeDAO, and Mike Novogratz’s Alternative asset management companies Samara Asset Group, Balaji Srinivasan, etc. At the end of 2023, Analog caused some excitement in the industry. They released information on the open testnet registration event on the X platform.



