 Operation and Maintenance
Operation and Maintenance
 Nginx
Nginx
 High-security configuration and firewall strategy for building Nginx servers
High-security configuration and firewall strategy for building Nginx servers
High-security configuration and firewall strategy for building Nginx servers
High-security configuration and firewall strategy for building Nginx servers
With the rapid development of the Internet, server security has received more and more attention. As an efficient and stable web server, Nginx's security configuration also needs our attention. In this article, we will explore how to configure your Nginx server for high security and introduce some firewall strategies.
- Use HTTPS protocol
HTTPS is an encrypted transmission protocol based on TLS/SSL protocol, which can ensure the security of data during transmission. To use the HTTPS protocol, you first need to obtain and install an SSL certificate. You can apply for a free SSL certificate from a certificate authority (such as Let's Encrypt) and then configure the certificate into the Nginx server. The following is an example configuration:
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /path/to/certificate.pem;
ssl_certificate_key /path/to/private_key.pem;
# 其他Nginx配置
...
}- Use strong passwords and keys
Setting strong passwords and keys on the Nginx server is an important measure to protect the server. You can use the htpasswd command to generate an encrypted password file and reference the file in the Nginx configuration file. The following is an example configuration:
server {
listen 80;
server_name example.com;
location / {
auth_basic "Restricted Access";
auth_basic_user_file /path/to/htpasswd;
# 其他Nginx配置
...
}
}- Setting Access Restrictions
Restricting access to server resources can reduce the risk of malicious attacks. In the Nginx configuration file, you can use the allow and deny directives to set access restrictions. The following is an example configuration:
server {
listen 80;
server_name example.com;
location / {
deny 192.168.1.0/24;
deny 10.0.0.0/8;
allow 192.168.1.100;
allow 127.0.0.1;
deny all;
# 其他Nginx配置
...
}
}The above configuration will deny access to the IP addresses 192.168.1.0/24 and 10.0.0.0/8 network segments, and allow access to the IP addresses 192.168.1.100 and 127.0.0.1 . Other unmatched IP addresses will be denied access.
- Using firewall policies
In addition to Nginx configuration, you can also use firewalls to increase server security. For example, you can use the iptables command or the firewalld service to configure firewall rules. The following is an example of setting a firewall policy using the iptables command:
# 允许SSH访问 sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT # 允许HTTP和HTTPS访问 sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPT # 其他规则 ... # 拒绝所有其他访问 sudo iptables -A INPUT -j DROP
The above configuration will allow SSH, HTTP, and HTTPS access, and deny all other access.
To sum up, by using the HTTPS protocol, setting strong passwords and keys, restricting access and using firewall policies, we can help us improve the security of the Nginx server. Of course, these are just some basic configurations and strategies, and there are actually more security measures that can be implemented. Therefore, we should maintain continuous attention to server security and promptly update and optimize related configurations and policies to ensure the security and reliability of the server.
The above is the detailed content of High-security configuration and firewall strategy for building Nginx servers. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
To allow the Tomcat server to access the external network, you need to: modify the Tomcat configuration file to allow external connections. Add a firewall rule to allow access to the Tomcat server port. Create a DNS record pointing the domain name to the Tomcat server public IP. Optional: Use a reverse proxy to improve security and performance. Optional: Set up HTTPS for increased security.
 Welcome to nginx!How to solve it?
Apr 17, 2024 am 05:12 AM
Welcome to nginx!How to solve it?
Apr 17, 2024 am 05:12 AM
To solve the "Welcome to nginx!" error, you need to check the virtual host configuration, enable the virtual host, reload Nginx, if the virtual host configuration file cannot be found, create a default page and reload Nginx, then the error message will disappear and the website will be normal show.
 How to generate URL from html file
Apr 21, 2024 pm 12:57 PM
How to generate URL from html file
Apr 21, 2024 pm 12:57 PM
Converting an HTML file to a URL requires a web server, which involves the following steps: Obtain a web server. Set up a web server. Upload HTML file. Create a domain name. Route the request.
 How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
Server deployment steps for a Node.js project: Prepare the deployment environment: obtain server access, install Node.js, set up a Git repository. Build the application: Use npm run build to generate deployable code and dependencies. Upload code to the server: via Git or File Transfer Protocol. Install dependencies: SSH into the server and use npm install to install application dependencies. Start the application: Use a command such as node index.js to start the application, or use a process manager such as pm2. Configure a reverse proxy (optional): Use a reverse proxy such as Nginx or Apache to route traffic to your application
 Can nodejs be accessed from the outside?
Apr 21, 2024 am 04:43 AM
Can nodejs be accessed from the outside?
Apr 21, 2024 am 04:43 AM
Yes, Node.js can be accessed from the outside. You can use the following methods: Use Cloud Functions to deploy the function and make it publicly accessible. Use the Express framework to create routes and define endpoints. Use Nginx to reverse proxy requests to Node.js applications. Use Docker containers to run Node.js applications and expose them through port mapping.
 How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
To successfully deploy and maintain a PHP website, you need to perform the following steps: Select a web server (such as Apache or Nginx) Install PHP Create a database and connect PHP Upload code to the server Set up domain name and DNS Monitoring website maintenance steps include updating PHP and web servers, and backing up the website , monitor error logs and update content.
 How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
An important task for Linux administrators is to protect the server from illegal attacks or access. By default, Linux systems come with well-configured firewalls, such as iptables, Uncomplicated Firewall (UFW), ConfigServerSecurityFirewall (CSF), etc., which can prevent a variety of attacks. Any machine connected to the Internet is a potential target for malicious attacks. There is a tool called Fail2Ban that can be used to mitigate illegal access on the server. What is Fail2Ban? Fail2Ban[1] is an intrusion prevention software that protects servers from brute force attacks. It is written in Python programming language
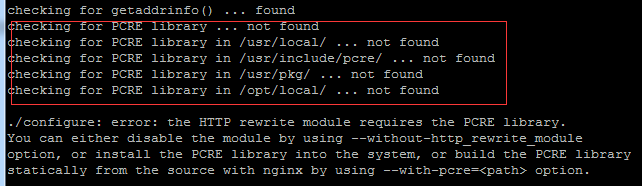 Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
Today, I will lead you to install Nginx in a Linux environment. The Linux system used here is CentOS7.2. Prepare the installation tools 1. Download Nginx from the Nginx official website. The version used here is: 1.13.6.2. Upload the downloaded Nginx to Linux. Here, the /opt/nginx directory is used as an example. Run "tar-zxvfnginx-1.13.6.tar.gz" to decompress. 3. Switch to the /opt/nginx/nginx-1.13.6 directory and run ./configure for initial configuration. If the following prompt appears, it means that PCRE is not installed on the machine, and Nginx needs to



