 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Preventing and repairing logic vulnerabilities in PHP websites
Preventing and repairing logic vulnerabilities in PHP websites
Preventing and repairing logic vulnerabilities in PHP websites
Prevention and Repair of Logic Vulnerabilities in PHP Websites
In today's Internet era, website security has become a matter of great concern to both users and website developers. However, while various types of vulnerabilities exist in websites, logic vulnerabilities are often the most overlooked. In this article, we will explore common logic vulnerabilities in PHP websites and provide some methods to prevent and fix them.
Logical vulnerabilities refer to security issues caused by incorrect logic or improper design in the program. In PHP websites, common logic vulnerabilities include unauthorized access, unauthorized operations, replay attacks, etc. Below we will introduce these vulnerabilities and their repair methods respectively, and give relevant code examples.
- Unauthorized Access
Unauthorized access refers to a situation where an unverified or authenticated user can access sensitive information or perform sensitive operations. In order to prevent this vulnerability, we need to implement strict permission checks in the website's access control mechanism.
For example, suppose we have a page that requires login to access:
<?php
session_start();
if (!isset($_SESSION['loggedin'])) {
header('Location: login.php');
exit();
}
// 其他需要登录才能访问的操作
?>In the above code, we first use the session_start() function to open the session, and then check whether you have logged in. If not logged in, redirect the user to the login page. This way we ensure that only authenticated users can access sensitive information or perform sensitive operations.
- Ultra-privilege operation
Ultra-privilege operation means that a user can perform operations that he does not have permission to perform. In order to prevent unauthorized access vulnerabilities, we need to implement strict permission checks in the program and restrict specific users' access to sensitive operations.
For example, suppose we have an admin page, and only users with admin rights can perform certain operations:
<?php
session_start();
if (!isset($_SESSION['loggedin']) || $_SESSION['role'] != 'admin') {
header('Location: index.php');
exit();
}
// 管理员操作
?>In the above code, we first check whether the user is logged in, and Whether its role is administrator. If the user is not logged in or is not an administrator, redirect the user to the homepage. This way we can restrict sensitive operations to only administrators.
- Replay attack
A replay attack refers to an attacker using authentication information from a previous valid session to pretend to be a legitimate user. In order to prevent replay attacks, we need to use some protective measures in the program, such as generating random session tokens and verifying each request.
For example, suppose we have a form processing page that needs to prevent replay attacks:
<?php
session_start();
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
if (isset($_POST['token']) && $_POST['token'] == $_SESSION['token']) {
// 执行表单处理操作
// ...
// 验证完成后,生成新的会话令牌
$_SESSION['token'] = bin2hex(random_bytes(32));
} else {
die('Invalid token');
}
}
?>In the above code, we first check whether the request method is POST, and then compare the request The token is the same as the token in the session. If they are the same, perform form processing operations. Once processing is complete, a new session token is generated and stored in the session. In this way we can prevent replay attacks.
To sum up, logic vulnerabilities are one of the common security issues in PHP websites. To prevent and fix these vulnerabilities, we need strict permission checking, access control and session management. By using relevant code examples appropriately, developers can improve the security of their websites and protect users' sensitive information from attacks.
The above is the detailed content of Preventing and repairing logic vulnerabilities in PHP websites. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1393
1393
 52
52
 1207
1207
 24
24
 This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
When logging into iTunesStore using AppleID, this error saying "This AppleID has not been used in iTunesStore" may be thrown on the screen. There are no error messages to worry about, you can fix them by following these solution sets. Fix 1 – Change Shipping Address The main reason why this prompt appears in iTunes Store is that you don’t have the correct address in your AppleID profile. Step 1 – First, open iPhone Settings on your iPhone. Step 2 – AppleID should be on top of all other settings. So, open it. Step 3 – Once there, open the “Payment & Shipping” option. Step 4 – Verify your access using Face ID. step
 How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
So, you took some great photos at your last party, but unfortunately, most of the photos you took were of red eyes. The photo itself is great, but the red eyes in it kind of ruin the image. Not to mention, some of those party photos might be from your friends’ phones. Today we'll look at how to remove red eye from photos. What causes the red eyes in the photo? Red-eye often occurs when taking photos with flash. This is because the light from the flash shines directly into the back of the eye, causing the blood vessels under the eye to reflect the light, giving the effect of red eyes in the photo. Fortunately, with the continuous advancement of technology, some cameras are now equipped with red-eye correction functions that can effectively solve this problem. By using this feature, the camera takes pictures
 How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
When a Win11 user uses credentials to log in, he or she receives an error message stating that your credentials cannot be verified. What is going on? After the editor investigated this problem, I found that there may be several different situations that directly or indirectly cause this problem. Let's take a look with the editor.
 Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
A Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis, and Fixes During PHP development, we often encounter errors with HTTP status code 500. This error is usually called "500InternalServerError", which means that some unknown errors occurred while processing the request on the server side. In this article, we will explore the common causes of PHP500 errors, how to diagnose them, and how to fix them, and provide specific code examples for reference. Common causes of 1.500 errors 1.
 An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
Many friends always encounter blue screens when using computer operating systems. Even the latest win11 system cannot escape the fate of blue screens. Therefore, today I have brought you a tutorial on how to repair win11 blue screens. No matter whether you have encountered a blue screen or not, you can learn it first in case you need it. How to fix win11 blue screen method 1. If we encounter a blue screen, first restart the system and check whether it can start normally. 2. If it can start normally, right-click "Computer" on the desktop and select "Manage" 3. Then expand "System Tools" on the left side of the pop-up window and select "Event Viewer" 4. In the event viewer, we will You can see what specific problem caused the blue screen. 5. Then just follow the blue screen situation and events
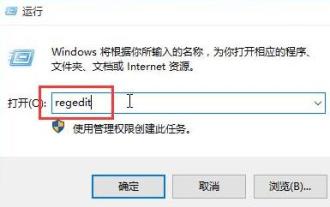 How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
1. Press win+r to open the run window, enter [regedit] and press Enter to open the registry editor. 2. In the opened registry editor, click to expand [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun]. In the blank space on the right, right-click and select [New - String Value], and rename it to [systray.exe]. 3. Double-click to open systray.exe, modify its numerical data to [C:WindowsSystem32systray.exe], and click [OK] to save the settings.
 How to solve the blue screen problem caused by csrss.exe
Dec 28, 2023 pm 06:24 PM
How to solve the blue screen problem caused by csrss.exe
Dec 28, 2023 pm 06:24 PM
If your computer often displays a blue screen after starting up, it may be caused by a serious error (stop code 0xF4) caused by the Windows system to the csrss.exe file. Now let’s see how to fix it! How to fix the csrss.exe blue screen. First, press the "Ctrl+Alt+Del" keys at the same time. At this time, the interface from the Microsoft Windows Task Manager will pop up. Click the "Task Manager" tab, and the screen will list all running programs and the resources they occupy and other information. Click again to enter the "Processes" tab, click "Image Name" again, and then find the "csrss.exe" file in the list. Click the "End Process" button
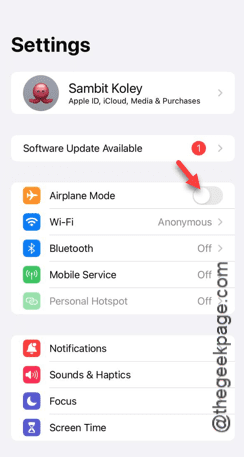 iPhone stuck in airplane mode: How to fix it
Jun 15, 2024 pm 02:16 PM
iPhone stuck in airplane mode: How to fix it
Jun 15, 2024 pm 02:16 PM
Airplane mode is very convenient in some situations. However, the same airplane mode may give you a headache if your iPhone suddenly gets stuck on it. In this article, we have designed this set of solutions to get your iPhone out of airplane mode. Quick fix – 1. Try disabling Airplane Mode directly from Control Center. 2. If you are unable to disable Airplane Mode from Control Center, you can disable Airplane Mode directly from the Settings tab – If these tips don’t work, follow the fixes below to resolve the issue. Fix 1 – Force Restart Your Device The process of force restarting your device is very simple. All you have to do is follow these step-by-step instructions. Step 1 – You can start the process by pressing and releasing the Volume Up button. step



