Learn how to find files using PowerToys in Microsoft
Windows will prevent you from making changes to a file if it is being used by other programs and processes. However, it doesn't always tell you which processes they are, which can be a frustrating thing, especially if you're blocked from continuing to work. While there are some ways to fix this problem, none are as simple and easy as the PowerToys utility. Here's everything you need to know to find files using PowerToys.
Find out which processes are using files with PowerToys File Locksmith
PowerToys is a free utility from Microsoft that includes many different tools. One of them is the File Locksmith tool, which lets you know if your files are used by other processes and programs. Whether it's a program, a folder, a DLL file or any other ordinary file, File Locksmith makes it easy for you to find what you're using it from the context menu. The specific operation method is as follows:
Install Power Toys
First, install PowerToys from the Microsoft website. To learn how to do this, see our guide on how to install PowerToys on a Windows PC. After installing PowerToys, launch it.
Enable File Locksmith
To get File Locksmith in the context menu, click FileLocksmith in the left pane in PowerToys.
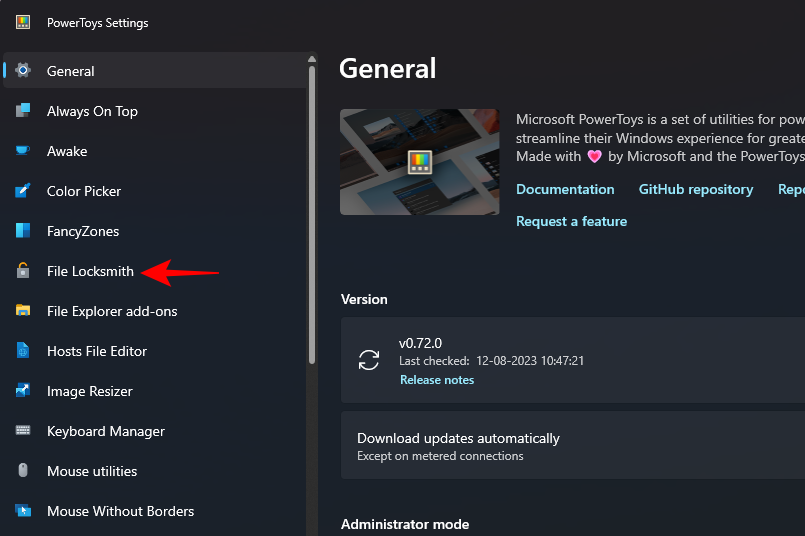
Then, on the right side, make sure the option "Enable File Locksmith" is turned on.
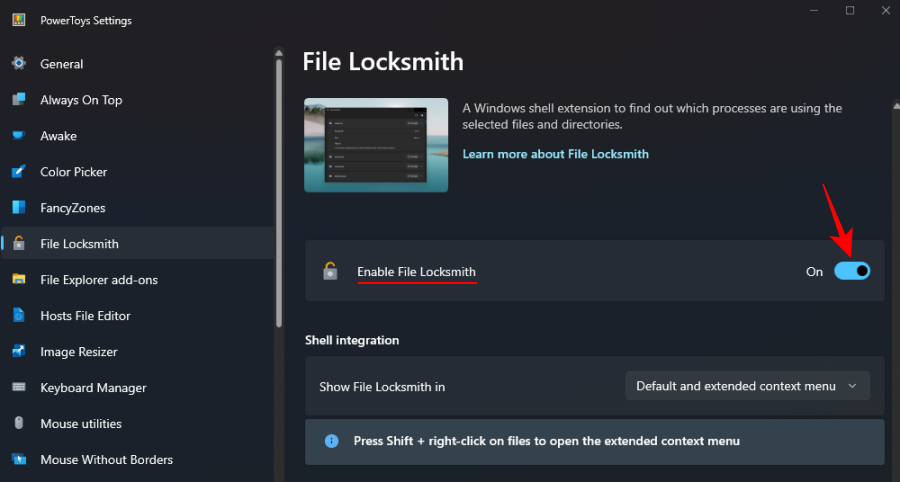
Find which processes are using the file
Next, right-click on the file or folder in question and select Show more options .
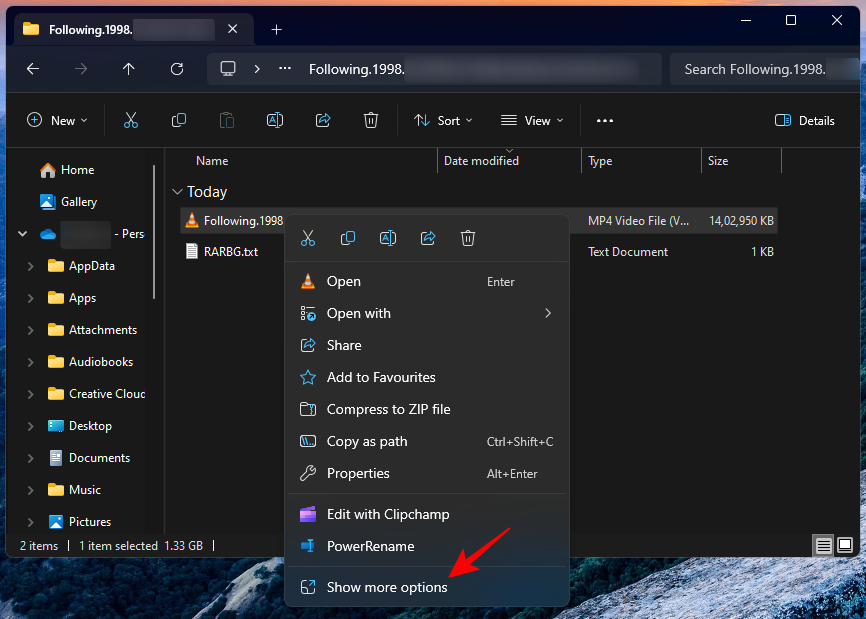
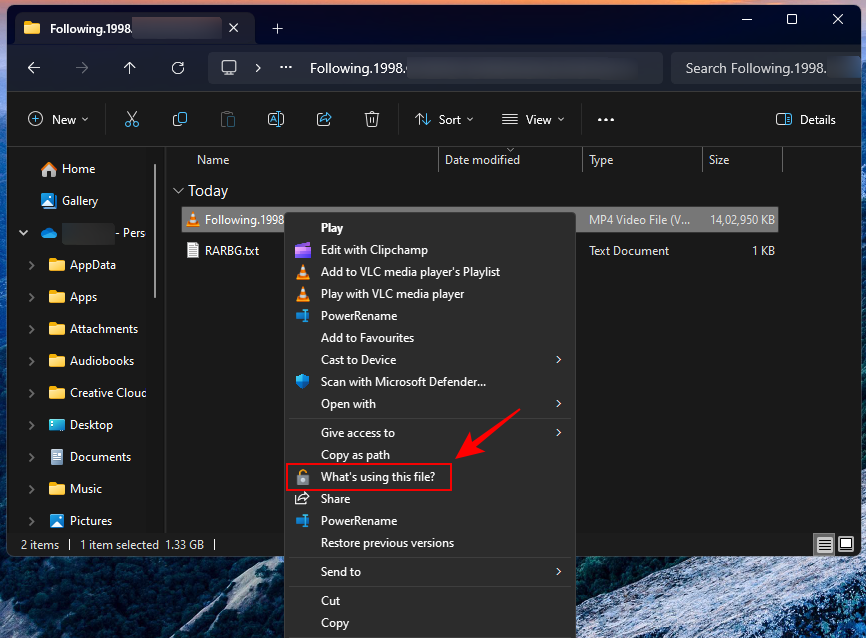
and select "What is being used by this file?"
"Restart as administrator" option in the upper right corner.
End Task" option its own process.

by right-clicking on the taskbar and selecting Task Manager (or pressing). Ctrl Shift Esc
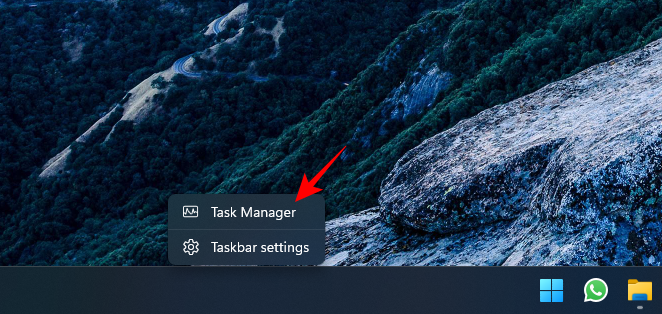 # Make sure the PID column is enabled (right-click within the columns area and select PID).
# Make sure the PID column is enabled (right-click within the columns area and select PID).
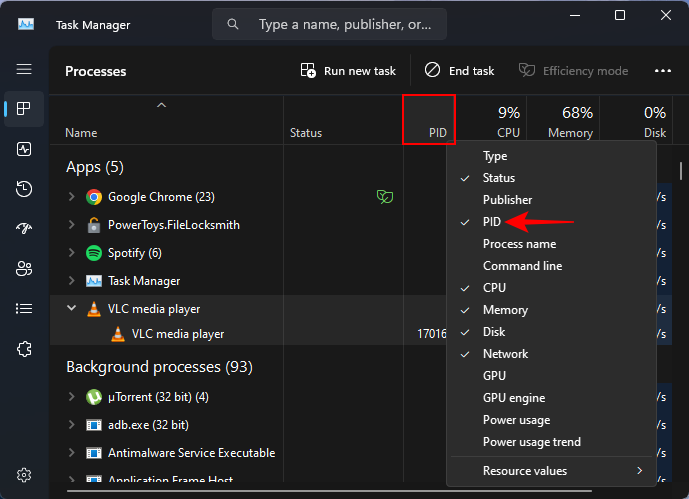 and confirm the process ID.
and confirm the process ID.
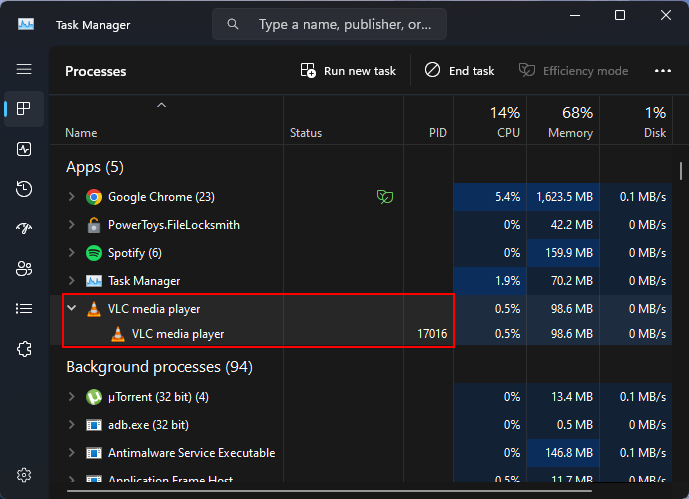 #If the two process IDs match, it is determined to be the same process using the file. You can now proceed to close the process or end the task from Task Manager or File Locksmith as shown before.
#If the two process IDs match, it is determined to be the same process using the file. You can now proceed to close the process or end the task from Task Manager or File Locksmith as shown before.
FAQ
Let’s consider some frequently asked questions about using PowerToy’s File Locksmith to find where files are being used.
How to find the open location of a file?
You can use some tools to find where files are used, such as Resource Monitor and Process Explorer. However, with PowerToys, all you need to do is right-click and select "Use the contents of this file" to find where the file opens.
Where is the File Locksmith for PowerToys in the context menu?
If you don't see File Locksmith's "Use the contents of this file" option in the context menu, click "Show more options."
How to prevent a process from using a file?
To prevent a process from using a file, first, find out which process is using the file with File Locksmith, then simply select "End Task".
The above is the detailed content of Learn how to find files using PowerToys in Microsoft. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
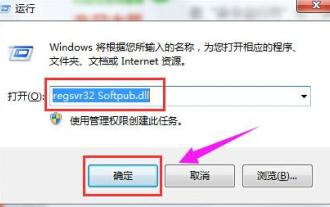 What to do if the 0x80004005 error code appears. The editor will teach you how to solve the 0x80004005 error code.
Mar 21, 2024 pm 09:17 PM
What to do if the 0x80004005 error code appears. The editor will teach you how to solve the 0x80004005 error code.
Mar 21, 2024 pm 09:17 PM
When deleting or decompressing a folder on your computer, sometimes a prompt dialog box "Error 0x80004005: Unspecified Error" will pop up. How should you solve this situation? There are actually many reasons why the error code 0x80004005 is prompted, but most of them are caused by viruses. We can re-register the dll to solve the problem. Below, the editor will explain to you the experience of handling the 0x80004005 error code. Some users are prompted with error code 0X80004005 when using their computers. The 0x80004005 error is mainly caused by the computer not correctly registering certain dynamic link library files, or by a firewall that does not allow HTTPS connections between the computer and the Internet. So how about
 How to transfer files from Quark Cloud Disk to Baidu Cloud Disk?
Mar 14, 2024 pm 02:07 PM
How to transfer files from Quark Cloud Disk to Baidu Cloud Disk?
Mar 14, 2024 pm 02:07 PM
Quark Netdisk and Baidu Netdisk are currently the most commonly used Netdisk software for storing files. If you want to save the files in Quark Netdisk to Baidu Netdisk, how do you do it? In this issue, the editor has compiled the tutorial steps for transferring files from Quark Network Disk computer to Baidu Network Disk. Let’s take a look at how to operate it. How to save Quark network disk files to Baidu network disk? To transfer files from Quark Network Disk to Baidu Network Disk, you first need to download the required files from Quark Network Disk, then select the target folder in the Baidu Network Disk client and open it. Then, drag and drop the files downloaded from Quark Cloud Disk into the folder opened by the Baidu Cloud Disk client, or use the upload function to add the files to Baidu Cloud Disk. Make sure to check whether the file was successfully transferred in Baidu Cloud Disk after the upload is completed. That's it
 Different uses of slashes and backslashes in file paths
Feb 26, 2024 pm 04:36 PM
Different uses of slashes and backslashes in file paths
Feb 26, 2024 pm 04:36 PM
A file path is a string used by the operating system to identify and locate a file or folder. In file paths, there are two common symbols separating paths, namely forward slash (/) and backslash (). These two symbols have different uses and meanings in different operating systems. The forward slash (/) is a commonly used path separator in Unix and Linux systems. On these systems, file paths start from the root directory (/) and are separated by forward slashes between each directory. For example, the path /home/user/Docume
 What is hiberfil.sys file? Can hiberfil.sys be deleted?
Mar 15, 2024 am 09:49 AM
What is hiberfil.sys file? Can hiberfil.sys be deleted?
Mar 15, 2024 am 09:49 AM
Recently, many netizens have asked the editor, what is the file hiberfil.sys? Can hiberfil.sys take up a lot of C drive space and be deleted? The editor can tell you that the hiberfil.sys file can be deleted. Let’s take a look at the details below. hiberfil.sys is a hidden file in the Windows system and also a system hibernation file. It is usually stored in the root directory of the C drive, and its size is equivalent to the size of the system's installed memory. This file is used when the computer is hibernated and contains the memory data of the current system so that it can be quickly restored to the previous state during recovery. Since its size is equal to the memory capacity, it may take up a larger amount of hard drive space. hiber
 Detailed explanation of Linux process priority adjustment method
Mar 15, 2024 am 08:39 AM
Detailed explanation of Linux process priority adjustment method
Mar 15, 2024 am 08:39 AM
Detailed explanation of the Linux process priority adjustment method. In the Linux system, the priority of a process determines its execution order and resource allocation in the system. Reasonably adjusting the priority of the process can improve the performance and efficiency of the system. This article will introduce in detail how to adjust the priority of the process in Linux and provide specific code examples. 1. Overview of process priority In the Linux system, each process has a priority associated with it. The priority range is generally -20 to 19, where -20 represents the highest priority and 19 represents
 Detailed explanation of the role of .ibd files in MySQL and related precautions
Mar 15, 2024 am 08:00 AM
Detailed explanation of the role of .ibd files in MySQL and related precautions
Mar 15, 2024 am 08:00 AM
Detailed explanation of the role of .ibd files in MySQL and related precautions MySQL is a popular relational database management system, and the data in the database is stored in different files. Among them, the .ibd file is a data file in the InnoDB storage engine, used to store data and indexes in tables. This article will provide a detailed analysis of the role of the .ibd file in MySQL and provide relevant code examples to help readers better understand. 1. The role of .ibd files: storing data: .ibd files are InnoDB storage
 Why do processes in Linux sleep?
Mar 20, 2024 pm 02:09 PM
Why do processes in Linux sleep?
Mar 20, 2024 pm 02:09 PM
Why do processes in Linux sleep? In the Linux operating system, a process can become dormant due to a number of different reasons and conditions. When a process is in a dormant state, it means that the process is temporarily suspended and cannot continue execution until certain conditions are met before it can be awakened to continue execution. Next, we will introduce in detail several common situations when a process enters hibernation in Linux, and illustrate them with specific code examples. Waiting for I/O to complete: When a process initiates an I/O operation (such as reading
 Detailed explanation of log viewing command in Linux system!
Mar 06, 2024 pm 03:55 PM
Detailed explanation of log viewing command in Linux system!
Mar 06, 2024 pm 03:55 PM
In Linux systems, you can use the following command to view the contents of the log file: tail command: The tail command is used to display the content at the end of the log file. It is a common command to view the latest log information. tail [option] [file name] Commonly used options include: -n: Specify the number of lines to be displayed, the default is 10 lines. -f: Monitor the file content in real time and automatically display the new content when the file is updated. Example: tail-n20logfile.txt#Display the last 20 lines of the logfile.txt file tail-flogfile.txt#Monitor the updated content of the logfile.txt file in real time head command: The head command is used to display the beginning of the log file



