 Technology peripherals
Technology peripherals
 It Industry
It Industry
 Reflection on Photographer's Infringement Case: Lawyer Reveals Visual China's Improper Rights Protection and Potential Fraud
Reflection on Photographer's Infringement Case: Lawyer Reveals Visual China's Improper Rights Protection and Potential Fraud
Reflection on Photographer's Infringement Case: Lawyer Reveals Visual China's Improper Rights Protection and Potential Fraud
The well-known photographer’s rights protection incident in China caused widespread discussion on the morning of August 16. The two parties started a dispute over the copyright issue of the picture.
In response, Senior Partner of Shanghai Dabang Law Firm, Intellectual Property Rights Lawyer You Yunting told Sina Technology: “Looking at Visual China’s statement, they only have the right to sell their works but not the copyright authorization and corresponding rights to protect their rights. In this case, they exercised their rights to protect their copyrights against the image users. , requiring the other party to pay hundreds of yuan per picture authorization fee based on past usage. The nature of this behavior, I think it is a non-rights protection. If it is done out of negligence, it is suspected of impersonation and infringement of the copyright of the pictures. People's rights. If it is intentional and is a large-scale and common behavior of the company, in addition to civil infringement, it will be suspected of fraud and may be subject to administrative penalties. If the circumstances are serious, such as concealing the facts of rights protection and not paying the copyright owner Sharing fees may even be suspected of fraud.”
Yesterday, the famous photographer @jeff disclosed his starry sky journey experience on Weibo, claiming that he had received a call from Visual China, accusing his official account of infringement. Used 173 of their photos and demanded compensation of more than 80,000 yuan! Jeff emphasized that he has never cooperated with Visual China, nor uploaded their pictures, and asked Visual China to give a reasonable explanation
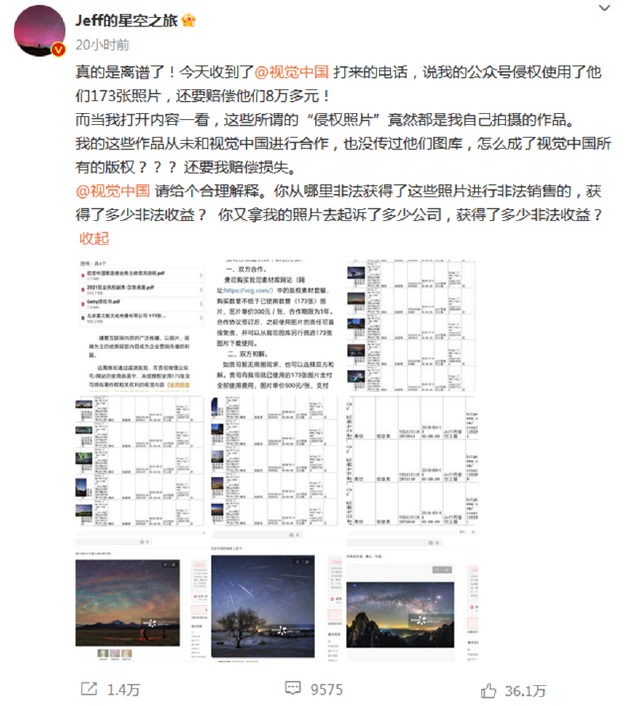
In this regard, Visual China responded that after preliminary verification, the pictures involved were sold by the photographer's authorized photo library Stocktrek Images, which in turn authorized the relevant pictures to Getty Images for sale. As the exclusive partner of Getty Images in mainland China, Visual China has complete sales rights, including the related pictures involved. The sales authorization chain of the pictures involved is clear and complete.
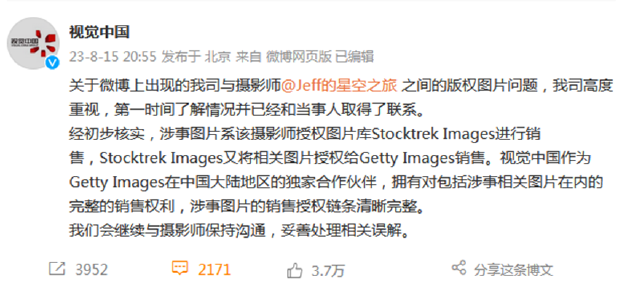
Today, jeff once again posted that he does not accept the view of Visual China. It also stated that has verified with Stocktrek, and Stocktrek has clearly informed Visual China that it has no right to sell its works, nor does it have any copyright to its works. Getty also has no right to sublicense its work. "There is no misunderstanding here. Up to now, you are still illegally selling my works online, lying to me and others that you own the copyright of the works and claiming compensation. Please stop your infringement immediately!!!"
#jeff As the photographer of the photo, will his and his company's use of his photo involve infringement? Lawyer You Yunting said that if the photographer of the photo authorizes the rights of the photo to a third party in the form of an exclusive license, he should also obtain the third party's authorization when using it himself. But if the authorization is just an ordinary license , or exclusive license and retain the right to use it, you can continue to use .
All articles on this site contain advertising statements, which include external jump links, aiming to convey more information and save selection time. The results are for reference only
The above is the detailed content of Reflection on Photographer's Infringement Case: Lawyer Reveals Visual China's Improper Rights Protection and Potential Fraud. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
When we no longer want to continue using the current Win10 Enterprise Edition 2016 Long-Term Service Edition, we can choose to switch to the Professional Edition. The method is also very simple. We only need to change some contents and install the system image. How to change win10 enterprise version 2016 long-term service version to professional version 1. Press win+R, and then enter "regedit" 2. Paste the following path directly in the address bar above: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion3 , then find the EditionID and replace the content with "professional" to confirm
 The photo of Trump's attack that flooded the screen, is the copyright owned by Visual China? Visual China Response
Jul 18, 2024 am 12:25 AM
The photo of Trump's attack that flooded the screen, is the copyright owned by Visual China? Visual China Response
Jul 18, 2024 am 12:25 AM
Author: Sanyan Reprinted from: Sanyan Finance (ID: sycaijing) A big news in the past two days-Trump was shot. For a time, related photos and videos went viral on the Internet. Among them, a set of photos of Trump holding his fist high and bleeding from his ears is quite artistic and has been widely circulated. It is understood that this set of photos was taken by AP photojournalist Evan Vucci, winner of the Pulitzer Prize for Journalism. For a time, Evan Vucci was noticed and discussed almost all over the world, and everyone knew that the classic photo was taken by him. Evan Vucci also posted photos he took of Trump’s attack on multiple social platforms. Today, Sanyan discovered something interesting. When several domestic media reported relevant content, the source annotation of the relevant photos was visually
 How to use Flask-Security to implement user authentication and authorization
Aug 04, 2023 pm 02:40 PM
How to use Flask-Security to implement user authentication and authorization
Aug 04, 2023 pm 02:40 PM
How to use Flask-Security to implement user authentication and authorization Introduction: In modern web applications, user authentication and authorization are essential functions. To simplify this process, Flask-Security is a very useful extension that provides a series of tools and functions to make user authentication and authorization simple and convenient. This article will introduce how to use Flask-Security to implement user authentication and authorization. 1. Install the Flask-Security extension: at the beginning
 How to get authorization for Douyin slices and goods? Is Douyin slicing easy to make?
Mar 07, 2024 pm 10:52 PM
How to get authorization for Douyin slices and goods? Is Douyin slicing easy to make?
Mar 07, 2024 pm 10:52 PM
Douyin, as a popular social media platform at the moment, not only provides people with a wealth of entertainment content, but has also become an important channel for many brands and merchants to promote products and achieve sales. Among them, Douyin’s slicing and selling products has become a novel and efficient marketing method. So, how do you get authorization for Douyin's sliced products? 1. How do you get authorization for Douyin's sliced products? Douyin's sliced products decompose long videos into short video clips and embed product promotion information in them to attract viewers to buy. . When slicing and selling goods on Douyin, the first step is to obtain authorization from the original video. When looking for a suitable licensor, you can consider using various channels such as Douyin platform, social media and industry forums. Find creators or copyright holders with popular video content and actively connect with them,
 UniApp implements detailed analysis of user login and authorization
Jul 05, 2023 pm 11:54 PM
UniApp implements detailed analysis of user login and authorization
Jul 05, 2023 pm 11:54 PM
UniApp implements detailed analysis of user login and authorization. In modern mobile application development, user login and authorization are essential functions. As a cross-platform development framework, UniApp provides a convenient way to implement user login and authorization. This article will explore the details of user login and authorization in UniApp, and attach corresponding code examples. 1. Implementation of user login function Create login page User login function usually requires a login page, which contains a form for users to enter their account number and password and a login button
 How to implement authentication and authorization in PHP applications using JWT
Aug 03, 2023 pm 10:17 PM
How to implement authentication and authorization in PHP applications using JWT
Aug 03, 2023 pm 10:17 PM
How to use JWT to implement authentication and authorization in PHP applications Introduction: With the rapid development of the Internet, authentication and authorization are becoming increasingly important in web applications. JSONWebToken (JWT) is a popular authentication and authorization mechanism that is widely used in PHP applications. This article will introduce how to use JWT to implement authentication and authorization in PHP applications, and provide code examples to help readers better understand the use of JWT. 1. Introduction to JWT JSONWebTo
 User authentication and authorization in Flask
Jun 17, 2023 pm 06:02 PM
User authentication and authorization in Flask
Jun 17, 2023 pm 06:02 PM
With the widespread use of web applications, security and data protection have become an important issue in web application development. To ensure the security of web applications, user authentication and authorization are required. As a popular web development framework, Flask provides many mechanisms for implementing user authentication and authorization. User Authentication User authentication refers to using a certain authentication method to determine whether the user's identity is legitimate when the user accesses the Web application. Flask offers a lot
 What to do if wps authorization has expired and text cannot be entered?
Mar 20, 2024 am 09:00 AM
What to do if wps authorization has expired and text cannot be entered?
Mar 20, 2024 am 09:00 AM
There are many genuine softwares in order to protect their own intellectual property rights. Before using the software, users must obtain some authorizations and obtain permission from the developer before they can use it. Some software has a trial period. After this period, you need to obtain re-authorization before you can use it normally. If wps prompts that the authorization has expired, we cannot perform any operations. How to solve this problem, let’s take a look at the explanation below. 1. I opened the WPS text program and clicked on the red box in the picture above, as shown in the picture below. 2. Click Configuration and Repair Tools. 3. Select "Advanced", as shown in the figure below. 4. Click the product management center and delete the "Expired" prompt content, as shown in the figure below. 5. After clicking "Add", enter the serial number, as shown in the figure below. 6. Then first



