Yii2 Programming: Security
If you're asking "What is Yii?" check out the Yii Framework Introduction, which reviews the benefits of Yii and includes an overview of Yii 2.0.
In this Programming with Yii2 series, I will guide readers in using the Yii2 PHP framework. If you plan to share your app with the public, it needs to be secure, and it's best to plan for this from the start. Luckily, starting with a framework like Yii makes this much easier than other frameworks. As stated in Yii Features:
Yii comes with many security measures to help protect your web applications from attacks such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and cookie tampering.
In this tutorial, I will walk you through basic security concepts within the Yii application framework. And, if you're interested, as the meeting planner app in our launch series nears alpha, future episodes will be dedicated to keeping the app secure.
Before we begin, please keep in mind that I do try to engage in the discussion below. If you have questions or topic suggestions, please leave a comment below or contact me on Twitter @reifman.
Note: If you notice there are gaps between episodes of the "Programming Yii" series, it's because I had to have brain surgery last year. Thank you for your patience and support - it's great to be writing regularly again and I look forward to continuing to cover Yii2.
Yii Security Basics
If you are new to web application security, there is a lot to know about Yii's products. I'll try to provide an overview based on the best Yii 2.0 documentation. The Yii team divides security into seven key areas:
- Authentication
- Authorization
- Use password
- Cryptography
- View security
- Authentication Client
- Best Practices
Let’s start digging into these one by one.
1. Authentication
Ilko Kacharov's Yii Framework Security Demo provides some useful slides summarizing the goals of authentication (and the following subtopic, authorization). Essentially, here are the questions these topics need to answer:
- Who is the user?
- Are the users who they say they are?
- Does the user have permission to access the resource?
- Does the user have permission to perform an operation?
- Does the user have the right to perform operations on the resource?
User Model and Identity Interface
Yii's yii/web/User class integrates with yii\web\IdentityInterface to manage the authentication state of users in your application.
Last November, I wrote a tutorial on Yii Advanced Application Templates. One of the advantages of the premium template is that it provides pre-built integration of the User model with ActiveRecord and databases. Therefore, your application immediately provides database-driven authentication.
The user model allows you to programmatically log in and out users:
- login() sets the specified identity and remembers the authentication state in sessions and cookies.
- logout() marks the user as a guest and clears related information from the session and cookies.
- setIdentity(): Changes the user's identity without touching the session or cookies, best suited for API functionality.
$isGuest property determines whether the current user is logged in. It is null when the user logs out, but otherwise returns an instance of IdentityInterface.
Essentially, you need a User class that extends ActiveRecord and implements methods that support IdentityInterface, like this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 |
|
Additionally, before creating a user, the application generates a random string as the authorization key. This can be used in "forgot password" emails or other email-based login links:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
|
Authorization
Yii provides two built-in authorization methods. Simpler access control lists (ACLs) determine which users or processes are allowed to perform operations on a resource, while more intensive role-based access controls (RBAC) help you manage access by defining roles. In RBAC, only users or system tasks with specific roles can perform specific operations.
Access Control List
ACLs are sometimes called access control filters (ACF). Yii provides ACL support in yii\filters\AccessControl. It is ideal for applications that require only simple access control. Here's what I've used so far in Meeting Planner.
The following is an example of a common SiteController that configures access behavior to filter access to available actions (usually pages). In this example, the ACLs apply to registration, login, and logout. '?' means that any user can access the login and registration pages, while '@' means that access is only allowed to logged in or authenticated users. In the following example, only logged in users can log out:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
|
随着控制器的增长,每个新操作都需要在访问控制规则中定义。而且,随着应用程序的增长,每个控制器及其所有操作都需要集成 ACL 过滤以确保安全。
基于角色的访问控制
基于角色的访问控制(RBAC)提供了更强大的身份验证系统,但也需要更多的前期设计和实现。
使用 RBAC,您可以通过可以继承(或不可继承)的角色来定义身份验证,并将角色应用于用户。您还可以定义角色规则。 RBAC 实现可能会变得相当复杂。
在下图中,管理员可以执行任何任务,作者可以创建帖子并更新自己的帖子。 Jane 是管理员,因此她可以执行管理员的任务,而 John 只是作者:
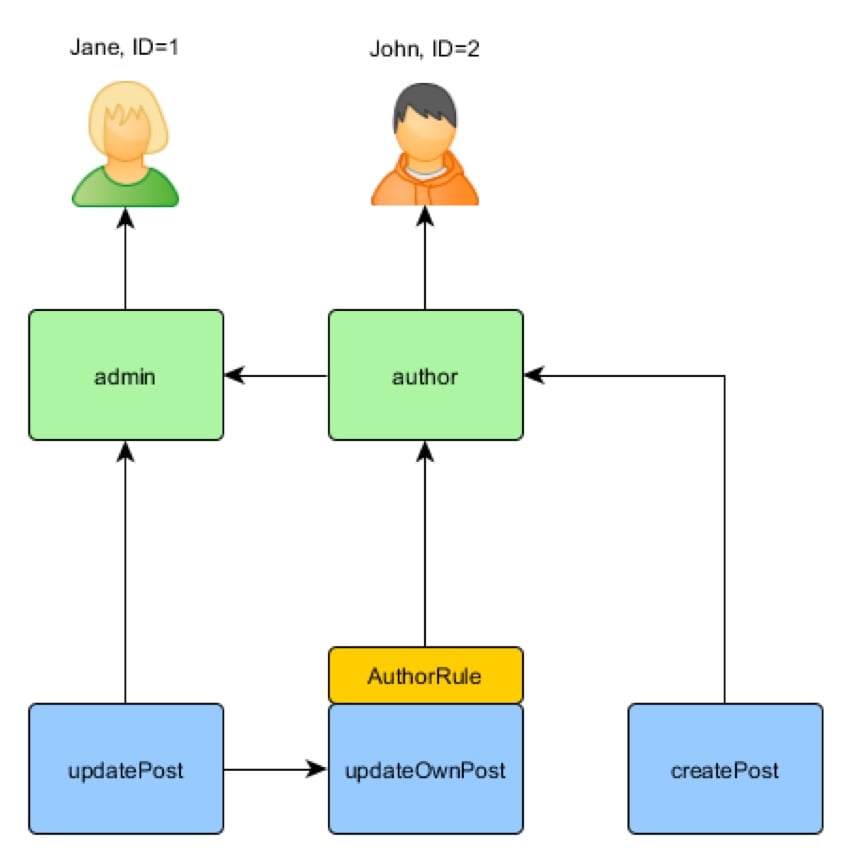
Yii 实现了所谓的“通用分层 RBAC,遵循 NIST RBAC 模型”。 RBAC 功能由其 authManager 应用程序组件提供。
我不会在这里深入探讨 RBAC,但我希望在以后的教程中能够深入探讨。再说一次,这取决于编辑女神——与她们交谈绝非易事:

基本上,要彻底实施 RBAC,您必须:
- 定义角色和权限
- 建立您的角色和权限之间的关系
- 定义任何现有的规则
- 将规则与您的角色和权限相关联
- 最后,为用户分配角色
您可以在下面看到启用 RBAC 系统所需的代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 |
|
要实现 RBAC,您必须准备好预先编写大量代码,或者随着应用程序的增长而编写大量代码。而且,如果您这样做,Yii 将根据您定义的身份验证框架来管理身份验证。换句话说,预先设计和编码可以提供可靠、详细的身份验证。
使用密码
正如马克·扎克伯格 (Mark Zuckerberg) 在 6 月份了解到的那样,一些网站以纯文本形式存储用户密码,但您的网站不应该这样做;公平地说,在密码管理器时代之前,我的 Facebook 帐户曾经因 PHPList 所做的事情而被黑客入侵过。不管怎样,Yii 使得加密和安全验证密码变得很容易。
Yii 的 crypt 函数使用 bcrypt 为您的密码生成哈希值。当人们注册时,会创建一个哈希值:
1 |
|
然后,当用户尝试登录时,它会被散列并与数据库中的散列进行比较:
1 2 3 4 5 |
|
但是您也可以使用 Yii 通过加密来保护数据。
密码学
Yii 框架提供了许多内置功能来支持数据保护:
- 密码和密钥生成函数,例如generateRandomKey、generateRandomString 和generateSalt。
- 密码验证:generatePasswordHash() 和 validatePassword()。
- 加密/解密:encryptByKey()、decryptByKey()、encryptByPassword() 和 decryptByPassword()。
- 使用标准算法派生密钥:pbkdf2() 和 hkdf()。
- 防止数据篡改:hashData() 和 validateData()。
查看安全性
来自用户的任何数据都可能受到 SQL 注入或跨浏览器脚本等攻击的感染。重要的是,您在视图中输出给用户的任何数据都应该被清理。 Yii 为此提供了几种方法。
首先,有 Html::encode,它基本上破坏了任何 SQL 或脚本:
1 2 3 4 5 6 7 |
|
并且与 HtmlPurifier 库集成以实现更大的文本块:
1 2 3 4 5 6 7 |
|
通过身份验证客户端登录
Yii 还提供了第三方身份验证的功能,这对于支持通过 Google、Facebook、Twitter 等进行社交登录尤其有用。
我为 Envato Tuts+ 编写了几篇关于在 Yii 框架内使用 AuthClient 进行社交登录的教程:
- 构建您的初创公司:使用 AuthClient 简化入口(待发布)
- 如何使用 Yii2 进行编程:Google 身份验证
-
如何使用 Yii2 进行编程:AuthClient 与 Twitter、Google 和其他网络集成
我发现社交登录对于会议策划者来说效果非常好。新用户无需密码即可开始安排会议。
最佳实践
Yii 还推荐了一些 Web 应用程序安全方面的最佳实践。它的文档为任何人提供了有关这些主题的良好入门知识。
- 过滤输入和输出
- 避免 SQL 注入
- 避免跨站脚本 (XSS)
- 避免跨站请求伪造 (CSRF)
- 避免文件泄露
- 在生产中避免调试信息和工具
- 使用通过 TLS 的安全连接
上面的前三个主题可以通过上面视图安全中讨论的编码得到很好的管理。
Yii also provides built-in CSRF protection for common activities and can be turned off when needed. In Meeting Planner, I have to turn off CSRF to accept messages published from Mailgun's API service.
For file exposure, the framework helps minimize this by centralizing all incoming requests into the web/index.php request file. This greatly limits the need to write application code that filters requests. It's well managed in one place.
Finally, using HTTPS can help secure your connection and protect users with Yii. Earlier this year, I wrote an article about Let's Encrypt — you can also use this tutorial to install HTTPS for your Yii applications.
Want to know more?
If you are interested in reading more detailed material on these topics, the Yii 1.x framework provides these posts. Sure, they're older and less specific to Yii 2, but they're still useful.
- Special Topic: Security
- How to write secure Yii applications
- Yii Security Extension Guide
Ending
I hope you enjoyed my overview of Yii2 security. If you integrate aspects of most or all of the above concepts into your application, you should have a basically secure web service. You might want to check out our Building Your Startup with PHP series to see some of these security practices in action.
Check out the upcoming tutorials in our "Programming with Yii2" series as we continue to dive into different aspects of the framework. I welcome feature and theme requests. You can post them in the comments below or send me an email on my Lookahead Consulting website.
If you would like to know when the next Yii2 tutorial is released, follow me on Twitter @reifman or check out my instructor page. My instructor page will immediately contain all articles from this series.
Let us work together to make the editorial goddesses happy.
Related Links
- Yii Best Security Practices
- Yii basic security class
- Yii2 Developer Exchange Meeting
The above is the detailed content of Yii2 Programming: Security. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Remove duplicate values from PHP array using regular expressions
Apr 26, 2024 pm 04:33 PM
Remove duplicate values from PHP array using regular expressions
Apr 26, 2024 pm 04:33 PM
How to remove duplicate values from PHP array using regular expressions: Use regular expression /(.*)(.+)/i to match and replace duplicates. Iterate through the array elements and check for matches using preg_match. If it matches, skip the value; otherwise, add it to a new array with no duplicate values.
 What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
Memory management in Java involves automatic memory management, using garbage collection and reference counting to allocate, use and reclaim memory. Effective memory management is crucial for security because it prevents buffer overflows, wild pointers, and memory leaks, thereby improving the safety of your program. For example, by properly releasing objects that are no longer needed, you can avoid memory leaks, thereby improving program performance and preventing crashes.
 What is programming for and what is the use of learning it?
Apr 28, 2024 pm 01:34 PM
What is programming for and what is the use of learning it?
Apr 28, 2024 pm 01:34 PM
1. Programming can be used to develop various software and applications, including websites, mobile applications, games, and data analysis tools. Its application fields are very wide, covering almost all industries, including scientific research, health care, finance, education, entertainment, etc. 2. Learning programming can help us improve our problem-solving skills and logical thinking skills. During programming, we need to analyze and understand problems, find solutions, and translate them into code. This way of thinking can cultivate our analytical and abstract abilities and improve our ability to solve practical problems.
 Problem-Solving with Python: Unlock Powerful Solutions as a Beginner Coder
Oct 11, 2024 pm 08:58 PM
Problem-Solving with Python: Unlock Powerful Solutions as a Beginner Coder
Oct 11, 2024 pm 08:58 PM
Pythonempowersbeginnersinproblem-solving.Itsuser-friendlysyntax,extensivelibrary,andfeaturessuchasvariables,conditionalstatements,andloopsenableefficientcodedevelopment.Frommanagingdatatocontrollingprogramflowandperformingrepetitivetasks,Pythonprovid
 Collection of C++ programming puzzles: stimulate thinking and improve programming skills
Jun 01, 2024 pm 10:26 PM
Collection of C++ programming puzzles: stimulate thinking and improve programming skills
Jun 01, 2024 pm 10:26 PM
C++ programming puzzles cover algorithm and data structure concepts such as Fibonacci sequence, factorial, Hamming distance, maximum and minimum values of arrays, etc. By solving these puzzles, you can consolidate C++ knowledge and improve algorithm understanding and programming skills.
 Unleash Your Inner Programmer: C for Absolute Beginners
Oct 11, 2024 pm 03:50 PM
Unleash Your Inner Programmer: C for Absolute Beginners
Oct 11, 2024 pm 03:50 PM
C is an ideal language for beginners to learn programming, and its advantages include efficiency, versatility, and portability. Learning C language requires: Installing a C compiler (such as MinGW or Cygwin) Understanding variables, data types, conditional statements and loop statements Writing the first program containing the main function and printf() function Practicing through practical cases (such as calculating averages) C language knowledge
 How does Java framework improve the security of enterprise-level applications?
Jun 04, 2024 pm 05:17 PM
How does Java framework improve the security of enterprise-level applications?
Jun 04, 2024 pm 05:17 PM
The Java framework provides five security enhancement methods for enterprise-level applications: input validation, data encryption, session management, access control, and exception handling. They protect applications from malicious threats through input validation tools, encryption mechanisms, session identification, access restrictions, and exception catching.
 The Key to Coding: Unlocking the Power of Python for Beginners
Oct 11, 2024 pm 12:17 PM
The Key to Coding: Unlocking the Power of Python for Beginners
Oct 11, 2024 pm 12:17 PM
Python is an ideal programming introduction language for beginners through its ease of learning and powerful features. Its basics include: Variables: used to store data (numbers, strings, lists, etc.). Data type: Defines the type of data in the variable (integer, floating point, etc.). Operators: used for mathematical operations and comparisons. Control flow: Control the flow of code execution (conditional statements, loops).






