 Database
Database
 Mysql Tutorial
Mysql Tutorial
 The importance of database backup and recovery! How do technical students use MySQL design protocols to protect data security?
The importance of database backup and recovery! How do technical students use MySQL design protocols to protect data security?
The importance of database backup and recovery! How do technical students use MySQL design protocols to protect data security?

The importance of database backup and recovery! How do technical students use MySQL design protocols to protect data security?
The database is an indispensable part of modern application development. It stores a large amount of data required by the application and carries important information of the enterprise. However, databases may also face various disasters, such as hard drive failure, accidental deletion, or data tampering. In order to ensure data security and integrity, database backup and recovery have become critical.
Database backup refers to copying the data and structure of the database so that it can be restored to the state at the time of backup in the event of data loss or irrecoverability. Backups can be done in a variety of ways, including physical and logical backups. Physical backup is to directly copy the binary file of the database, for example, use the mysqldump command of MySQL for backup. Logical backup is to export data to a text file for backup by executing SQL statements, for example, use the --opt option of the mysqldump command to export data. Backup files should be stored regularly in a secure location, preferably away from the database server, to prevent data loss caused by system failure or natural disasters.
Database recovery refers to restoring backed-up data and structures to their original state in the event of inevitable data loss or database damage. The recovery process can be complex, especially if the database has large amounts of data or complex relationships. Recovery can be done using backup files, and transaction logs can be used for incremental recovery. Choose a recovery strategy on a case-by-case basis, and be sure to test and verify your backup files before proceeding with recovery operations.
In addition to backup and recovery, there are other strategies and techniques that can be used to protect the security of your database. The following are some MySQL database design rules that can help technical students strengthen the protection of data security:
- Reasonably set permissions and access control: MySQL provides a flexible permission management mechanism that can be based on different users and roles. Set different permissions according to your needs. Properly setting permissions and access controls can prevent unauthorized users from accessing and modifying data.
- Use strong passwords and encryption: Use strong passwords that are difficult to guess, change passwords regularly, and use the encryption features provided by MySQL to protect sensitive data such as usernames and passwords.
- Regularly update and optimize the database: Timely updating and optimizing the database can repair security vulnerabilities and improve database performance. Keep databases and related software up to date to reduce the risk of exploitation.
- Set a reasonable backup strategy: Set different backup frequencies and retention times based on the importance of data and application requirements. Backup files should be saved on different storage media and encrypted to protect data security.
The following is an example showing how to use MySQL to back up database data:
# 备份数据库 mysqldump -u username -p database_name > backup.sql # 恢复数据库 mysql -u username -p database_name < backup.sql
In practical applications, database backup and recovery are important means to ensure data security and integrity. Technical students should formulate their own backup and recovery strategies based on specific business needs and actual conditions, and follow database design protocols to protect the company's data security.
The above is the detailed content of The importance of database backup and recovery! How do technical students use MySQL design protocols to protect data security?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
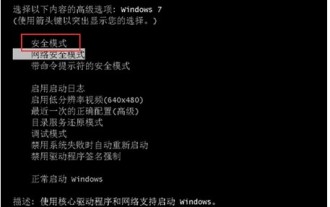 What to do if the Windows 7 system registry file is lost or damaged
Jul 08, 2023 pm 05:29 PM
What to do if the Windows 7 system registry file is lost or damaged
Jul 08, 2023 pm 05:29 PM
Windows 7 users encounter the phenomenon that the system registry file is missing or damaged when starting up. How to solve this situation? You first force restart the computer, then press the F8 key, select safe mode in the opened page, then find the command prompt in the menu bar to open, enter the SFC/SCANNOW command and press Enter, then the system will automatically start the computer Repair missing or corrupted installation files. What to do if the Windows 7 system registry file is lost or damaged 1. After the first power-on self-test, immediately hold down the F8 key, use the arrow keys to select safe mode, and hit Enter. 2. Then click the Start button, select Command Prompt, and run as an administrator. 3. Finally, enter SFC/ in the pop-up prompt.
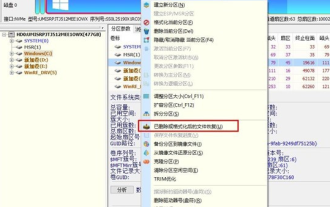 How to recover diskgenius data-diskgenius data recovery tutorial
Mar 06, 2024 am 09:34 AM
How to recover diskgenius data-diskgenius data recovery tutorial
Mar 06, 2024 am 09:34 AM
Many friends don’t know how to recover diskgenius data, so the editor will share the relevant tutorials on diskgenius data recovery. Let’s take a look. I believe it will be helpful to everyone. First, in the hard disk partition diagram above the main interface of DiskGenius, you can directly select the target partition and right-click. Then, in the shortcut menu that pops up, find and click the "Deleted or formatted file recovery" menu item, as shown in the figure. In the second step, the recovery options window pops up and make sure to check the three options of "Recover Deleted Files", "Complete Recovery" and "Extra Scan for Known File Types". Step 3: Click the "Select File Type" button on the right and specify the files you need to recover in the pop-up window
 Solution to PHP parameter missing problem
Mar 11, 2024 am 09:27 AM
Solution to PHP parameter missing problem
Mar 11, 2024 am 09:27 AM
Solution to the problem of PHP parameter loss In the process of developing PHP programs, we often encounter the problem of parameter loss. This may be caused by incomplete parameters passed by the front end or incorrect way of receiving parameters by the back end. In this article, we will provide some solutions to the problem of missing parameters in PHP, along with specific code examples. 1. Front-end parameter passing problem Use the GET method to pass parameters. When using the GET method to pass parameters, the parameters will be appended to the requested URL in the form of URL parameters. When receiving parameters in the backend
 ThinkPHP6 data backup and recovery: ensuring data security
Aug 13, 2023 am 08:28 AM
ThinkPHP6 data backup and recovery: ensuring data security
Aug 13, 2023 am 08:28 AM
ThinkPHP6 data backup and recovery: ensuring data security With the rapid development of the Internet, data has become an extremely important asset. Therefore, the security of data is of great concern. In web application development, data backup and recovery are an important part of ensuring data security. In this article, we will introduce how to use the ThinkPHP6 framework for data backup and recovery to ensure data security. 1. Data backup Data backup refers to copying or storing the data in the database in some way. This way even if the data
 PHP and PDO: How to perform database backup and restore operations
Jul 29, 2023 pm 06:54 PM
PHP and PDO: How to perform database backup and restore operations
Jul 29, 2023 pm 06:54 PM
PHP and PDO: How to perform database backup and restore operations When developing web applications, database backup and restore are very important tasks. As a popular server-side scripting language, PHP provides a wealth of libraries and extensions, among which PDO (PHP Data Objects) is a powerful database access abstraction layer. This article will introduce how to use PHP and PDO to perform database backup and restore operations. Step 1: Connect to the database Before actual operation, we need to establish a connection to the database. Use PDO pair
 Analysis of project experience on MySQL database backup and recovery performance optimization
Nov 02, 2023 am 08:53 AM
Analysis of project experience on MySQL database backup and recovery performance optimization
Nov 02, 2023 am 08:53 AM
In the current Internet era, the importance of data is self-evident. As one of the core components of Internet applications, database backup and recovery work is particularly important. However, as the amount of data continues to increase and business requirements become increasingly complex, traditional database backup and recovery solutions can no longer meet the high availability and high performance requirements of modern applications. Therefore, optimizing the backup and recovery performance of MySQL database has become an urgent problem that needs to be solved. In practice, we have adopted a series of project experiences to effectively improve MySQL data
 How to use middleware for data recovery in Laravel
Nov 02, 2023 pm 02:12 PM
How to use middleware for data recovery in Laravel
Nov 02, 2023 pm 02:12 PM
Laravel is a popular PHP web application framework that provides many fast and easy ways to build efficient, secure and scalable web applications. When developing Laravel applications, we often need to consider the issue of data recovery, that is, how to recover data and ensure the normal operation of the application in the event of data loss or damage. In this article, we will introduce how to use Laravel middleware to implement data recovery functions and provide specific code examples. 1. What is Lara?
 How to deal with hard drive sector corruption issues
Feb 19, 2024 am 11:03 AM
How to deal with hard drive sector corruption issues
Feb 19, 2024 am 11:03 AM
How to solve a broken hard disk sector? A broken hard disk sector is a common hardware failure, which may cause data loss and affect computer performance. It is very important to understand and solve the problem of bad hard drive sectors. This article will introduce the concept of hard disk sectors, discuss common causes of bad hard disk sectors and solutions. 1. What are hard disk sectors? Before introducing how to solve the problem of bad hard disk sectors, let’s first understand what hard disk sectors are. A hard disk sector is the smallest readable and writable unit on a hard drive. It is a small section of space on a hard drive. It is





