 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How to avoid common security vulnerabilities when parsing and processing HTML/XML in PHP
How to avoid common security vulnerabilities when parsing and processing HTML/XML in PHP
How to avoid common security vulnerabilities when parsing and processing HTML/XML in PHP

How to avoid common security vulnerabilities when parsing and processing HTML/XML in PHP
Introduction:
In modern web development, HTML and XML are common Data Format. As a commonly used back-end language, PHP has built-in functions for processing and parsing HTML/XML. However, when processing and parsing these data formats, there are often threats of security vulnerabilities. This article will cover some common security vulnerabilities and how to avoid them in PHP.
1. Cross-site scripting attack (XSS)
Cross-site scripting attack is a common web security vulnerability. The attacker obtains the user's sensitive information by injecting malicious script code. When processing and parsing HTML/XML, incorrectly outputting user-supplied data can lead to XSS vulnerabilities.
Solution:
The key to avoiding XSS vulnerabilities is to properly filter and escape user input to ensure that unprocessed user data is not output directly into HTML/XML. PHP provides some processing functions to filter and escape user input, such as htmlspecialchars() and htmlentities().
Sample code:
$name = $_POST['name']; $comment = $_POST['comment']; // 使用htmlspecialchars()对输出进行转义 echo "用户名:" . htmlspecialchars($name) . "<br>"; echo "评论内容:" . htmlspecialchars($comment) . "<br>";
2. XML external entity injection (XXE)
XML external entity injection is an attack method that targets applications to parse XML data provided by users. An attacker can inject malicious entities to read sensitive files or make remote requests.
Solution:
In PHP, XXE attacks can be prevented by disabling external entity resolution or limiting the access scope of entity resolution. This can be achieved using the libxml_disable_entity_loader() function or setting the libxml_use_internal_errors() function.
Sample code:
$xml = '<?xml version="1.0"?>
<!DOCTYPE data [
<!ELEMENT data ANY >
<!ENTITY file SYSTEM "file:///etc/passwd" >
]>
<data>&file;</data>';
// 禁用外部实体解析
libxml_disable_entity_loader(true);
$doc = new DOMDocument();
$doc->loadXML($xml);
// 输出:&file;
echo $doc->textContent;3. Encryption algorithm bypass
When using PHP to process HTML/XML data, sometimes it is necessary to encrypt the data to prevent data leakage. However, if an insecure encryption algorithm or implementation is used, an attacker may be able to obtain sensitive information by bypassing encryption.
Solution:
Selecting the appropriate encryption algorithm and correct implementation is the key. PHP provides many encryption-related functions and classes, such as hash() function and openssl extension. Password hashing functions can be used to store passwords and the HTTPS protocol is used to transmit sensitive data.
Sample code:
$password = "123456";
$hashedPassword = password_hash($password, PASSWORD_DEFAULT);
if (password_verify($password, $hashedPassword)) {
echo "密码验证通过";
} else {
echo "密码验证失败";
}Conclusion:
When processing and parsing HTML/XML in PHP, you must pay attention to security issues. This article describes some common security vulnerabilities and provides solutions and code examples. Through correct filtering, escaping and encryption, we can effectively prevent attacks from security vulnerabilities such as XSS, XXE and encryption algorithm bypass.
The above is the detailed content of How to avoid common security vulnerabilities when parsing and processing HTML/XML in PHP. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
Long URLs, often cluttered with keywords and tracking parameters, can deter visitors. A URL shortening script offers a solution, creating concise links ideal for social media and other platforms. These scripts are valuable for individual websites a
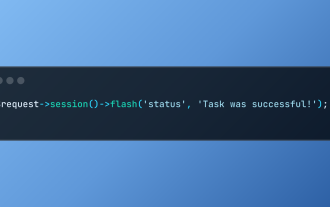 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
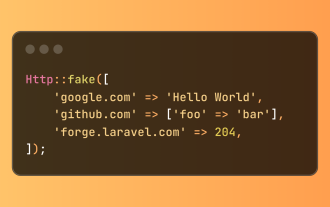 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
This is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
The 2025 PHP Landscape Survey investigates current PHP development trends. It explores framework usage, deployment methods, and challenges, aiming to provide insights for developers and businesses. The survey anticipates growth in modern PHP versio
 Notifications in Laravel
Mar 04, 2025 am 09:22 AM
Notifications in Laravel
Mar 04, 2025 am 09:22 AM
In this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov





