 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Study the underlying development principles of PHP: Detailed explanation of security sensitive data and authentication technology
Study the underlying development principles of PHP: Detailed explanation of security sensitive data and authentication technology
Study the underlying development principles of PHP: Detailed explanation of security sensitive data and authentication technology

Study on the underlying development principles of PHP: Detailed explanation of security sensitive data and authentication technology
In the development of Web applications, security has always been a very important issue. Especially for applications that handle sensitive data and user authentication, security is critical. In PHP development, understanding the underlying development principles and technologies is one of the keys to ensuring application security. This article will introduce in detail the security sensitive data and authentication technology in the underlying development principles of PHP.
- Data Encryption and Decryption
When dealing with sensitive data, the first thing to consider is encrypting this data. PHP provides a variety of data encryption and decryption methods, such as using the symmetric encryption algorithm AES, DES or using the asymmetric encryption algorithm RSA. Symmetric encryption algorithms require the same key for encryption and decryption, while asymmetric encryption algorithms use two keys, one for encryption and one for decryption. Before using any encryption algorithm, you need to ensure the security of the keys and consider key generation and management. - Store sensitive data securely
In addition to encrypting data, you also need to consider how to store sensitive data securely. A common approach is to store sensitive data in a database and use a hash function to encrypt and check passwords. A hash function can convert data into a fixed-length hash value, making it impossible to restore the original data through the hash value. In PHP, commonly used hash functions include MD5, SHA1, SHA256, etc. However, due to the one-way nature of the hash function, usually when verifying a password, a salting method should be used, that is, the salt value is hashed with the password and the result is compared with the hash value stored in the database. to ensure password security. - Cross-site scripting (XSS) protection
Cross-site scripting (XSS) is a very common web security vulnerability. Attackers steal users' sensitive data by injecting malicious scripts into web pages. or perform other malicious actions. In order to prevent XSS attacks, PHP provides some built-in functions and filters, such as htmlspecialchars() and strip_tags(), which are used to filter and escape input data to ensure that the content entered by the user will not be executed as a malicious script. - Cross-site request forgery (CSRF) protection
Cross-site request forgery (CSRF) is another common web security vulnerability. Attackers perform certain malicious operations by disguising themselves as requests from legitimate users. In order to prevent CSRF attacks, in PHP development, you can use some techniques, such as verifying the HTTP Referer header, using CSRF tokens or double submission cookie verification, etc. These techniques ensure that requests come from legitimate sources and prevent malicious requests from being executed. - User Authentication
User authentication is the core of application security. In PHP, there are multiple authentication methods to choose from, including basic authentication, digest authentication, token authentication, etc. Basic authentication is the simplest method and sends the username and password directly to the server for verification. Digest authentication uses a digest algorithm to encrypt and verify passwords and other information. Token authentication uses tokens to authenticate users, which can be persistent or short-lived and passed between different requests.
Summary:
This article introduces the security sensitive data and authentication technology in the underlying development principles of PHP. Encryption and decryption are essential steps when dealing with sensitive data. Securely storing sensitive data requires consideration of password hashing and salting. For common web security vulnerabilities, such as XSS and CSRF, PHP provides some built-in functions and technologies for protection. Finally, user authentication is key to ensuring application security, and authentication can be done through a variety of methods. By deeply understanding and mastering these underlying development principles and technologies, we can improve application security, protect users' sensitive data and ensure effective identity verification.
The above is the detailed content of Study the underlying development principles of PHP: Detailed explanation of security sensitive data and authentication technology. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 Slow Cellular Data Internet Speeds on iPhone: Fixes
May 03, 2024 pm 09:01 PM
Slow Cellular Data Internet Speeds on iPhone: Fixes
May 03, 2024 pm 09:01 PM
Facing lag, slow mobile data connection on iPhone? Typically, the strength of cellular internet on your phone depends on several factors such as region, cellular network type, roaming type, etc. There are some things you can do to get a faster, more reliable cellular Internet connection. Fix 1 – Force Restart iPhone Sometimes, force restarting your device just resets a lot of things, including the cellular connection. Step 1 – Just press the volume up key once and release. Next, press the Volume Down key and release it again. Step 2 – The next part of the process is to hold the button on the right side. Let the iPhone finish restarting. Enable cellular data and check network speed. Check again Fix 2 – Change data mode While 5G offers better network speeds, it works better when the signal is weaker
 The vitality of super intelligence awakens! But with the arrival of self-updating AI, mothers no longer have to worry about data bottlenecks
Apr 29, 2024 pm 06:55 PM
The vitality of super intelligence awakens! But with the arrival of self-updating AI, mothers no longer have to worry about data bottlenecks
Apr 29, 2024 pm 06:55 PM
I cry to death. The world is madly building big models. The data on the Internet is not enough. It is not enough at all. The training model looks like "The Hunger Games", and AI researchers around the world are worrying about how to feed these data voracious eaters. This problem is particularly prominent in multi-modal tasks. At a time when nothing could be done, a start-up team from the Department of Renmin University of China used its own new model to become the first in China to make "model-generated data feed itself" a reality. Moreover, it is a two-pronged approach on the understanding side and the generation side. Both sides can generate high-quality, multi-modal new data and provide data feedback to the model itself. What is a model? Awaker 1.0, a large multi-modal model that just appeared on the Zhongguancun Forum. Who is the team? Sophon engine. Founded by Gao Yizhao, a doctoral student at Renmin University’s Hillhouse School of Artificial Intelligence.
 The U.S. Air Force showcases its first AI fighter jet with high profile! The minister personally conducted the test drive without interfering during the whole process, and 100,000 lines of code were tested for 21 times.
May 07, 2024 pm 05:00 PM
The U.S. Air Force showcases its first AI fighter jet with high profile! The minister personally conducted the test drive without interfering during the whole process, and 100,000 lines of code were tested for 21 times.
May 07, 2024 pm 05:00 PM
Recently, the military circle has been overwhelmed by the news: US military fighter jets can now complete fully automatic air combat using AI. Yes, just recently, the US military’s AI fighter jet was made public for the first time and the mystery was unveiled. The full name of this fighter is the Variable Stability Simulator Test Aircraft (VISTA). It was personally flown by the Secretary of the US Air Force to simulate a one-on-one air battle. On May 2, U.S. Air Force Secretary Frank Kendall took off in an X-62AVISTA at Edwards Air Force Base. Note that during the one-hour flight, all flight actions were completed autonomously by AI! Kendall said - "For the past few decades, we have been thinking about the unlimited potential of autonomous air-to-air combat, but it has always seemed out of reach." However now,
 Tesla robots work in factories, Musk: The degree of freedom of hands will reach 22 this year!
May 06, 2024 pm 04:13 PM
Tesla robots work in factories, Musk: The degree of freedom of hands will reach 22 this year!
May 06, 2024 pm 04:13 PM
The latest video of Tesla's robot Optimus is released, and it can already work in the factory. At normal speed, it sorts batteries (Tesla's 4680 batteries) like this: The official also released what it looks like at 20x speed - on a small "workstation", picking and picking and picking: This time it is released One of the highlights of the video is that Optimus completes this work in the factory, completely autonomously, without human intervention throughout the process. And from the perspective of Optimus, it can also pick up and place the crooked battery, focusing on automatic error correction: Regarding Optimus's hand, NVIDIA scientist Jim Fan gave a high evaluation: Optimus's hand is the world's five-fingered robot. One of the most dexterous. Its hands are not only tactile
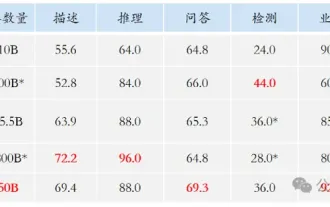
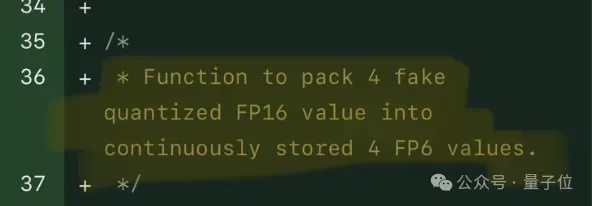 Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
FP8 and lower floating point quantification precision are no longer the "patent" of H100! Lao Huang wanted everyone to use INT8/INT4, and the Microsoft DeepSpeed team started running FP6 on A100 without official support from NVIDIA. Test results show that the new method TC-FPx's FP6 quantization on A100 is close to or occasionally faster than INT4, and has higher accuracy than the latter. On top of this, there is also end-to-end large model support, which has been open sourced and integrated into deep learning inference frameworks such as DeepSpeed. This result also has an immediate effect on accelerating large models - under this framework, using a single card to run Llama, the throughput is 2.65 times higher than that of dual cards. one
 Open-Sora comprehensive open source upgrade: supports 16s video generation and 720p resolution
Apr 25, 2024 pm 02:55 PM
Open-Sora comprehensive open source upgrade: supports 16s video generation and 720p resolution
Apr 25, 2024 pm 02:55 PM
Open-Sora has been quietly updated in the open source community. It now supports video generation up to 16 seconds, with resolutions up to 720p, and can handle text-to-image, text-to-video, image-to-video, and video-to-video of any aspect ratio. and the generation needs of infinitely long videos. Let's try it out. Generate a horizontal screen Christmas snow scene, post to B site and then generate a vertical screen, and use Douyin to generate a 16-second long video. Now everyone can have a screenwriting addiction. How to play? Guidance GitHub: https://github.com/hpcaitech/Open-Sora What’s even cooler is that Open-Sora is still all open source, including the latest model architecture, the latest model weights, multi-time/resolution/long-term
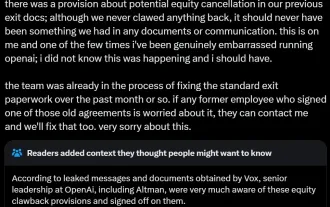 AI startups collectively switched jobs to OpenAI, and the security team regrouped after Ilya left!
Jun 08, 2024 pm 01:00 PM
AI startups collectively switched jobs to OpenAI, and the security team regrouped after Ilya left!
Jun 08, 2024 pm 01:00 PM
Last week, amid the internal wave of resignations and external criticism, OpenAI was plagued by internal and external troubles: - The infringement of the widow sister sparked global heated discussions - Employees signing "overlord clauses" were exposed one after another - Netizens listed Ultraman's "seven deadly sins" Rumors refuting: According to leaked information and documents obtained by Vox, OpenAI’s senior leadership, including Altman, was well aware of these equity recovery provisions and signed off on them. In addition, there is a serious and urgent issue facing OpenAI - AI safety. The recent departures of five security-related employees, including two of its most prominent employees, and the dissolution of the "Super Alignment" team have once again put OpenAI's security issues in the spotlight. Fortune magazine reported that OpenA
 70B model generates 1,000 tokens in seconds, code rewriting surpasses GPT-4o, from the Cursor team, a code artifact invested by OpenAI
Jun 13, 2024 pm 03:47 PM
70B model generates 1,000 tokens in seconds, code rewriting surpasses GPT-4o, from the Cursor team, a code artifact invested by OpenAI
Jun 13, 2024 pm 03:47 PM
70B model, 1000 tokens can be generated in seconds, which translates into nearly 4000 characters! The researchers fine-tuned Llama3 and introduced an acceleration algorithm. Compared with the native version, the speed is 13 times faster! Not only is it fast, its performance on code rewriting tasks even surpasses GPT-4o. This achievement comes from anysphere, the team behind the popular AI programming artifact Cursor, and OpenAI also participated in the investment. You must know that on Groq, a well-known fast inference acceleration framework, the inference speed of 70BLlama3 is only more than 300 tokens per second. With the speed of Cursor, it can be said that it achieves near-instant complete code file editing. Some people call it a good guy, if you put Curs



