 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Protect your Linux server: Become proficient with these commands
Protect your Linux server: Become proficient with these commands
Protect your Linux server: Become proficient with these commands

Protect your Linux server: Use these commands proficiently
With the development of cloud computing and network technology, Linux servers are becoming more and more popular among enterprises and individual users . As a stable and reliable operating system, Linux provides many powerful security features to protect servers from threats of intrusion and data leakage. However, in order to better protect your Linux server, it is necessary to understand and apply some important commands. In this article, we will introduce some proficient commands to strengthen the security of your Linux server.
- iptables: iptables is a powerful firewall tool that controls network traffic by configuring rules. Proficient use of iptables allows you to limit unnecessary access and protect your server from network attacks. Commonly used commands are:
- iptables -L: View the current firewall rules.
- iptables -A INPUT -p tcp --dport 22 -j DROP: Use this command to block all access to the SSH port.
- fail2ban: fail2ban is a tool used to prevent brute force attacks. It monitors the server's log files and blocks access from malicious IP addresses based on set rules. Proficient use of fail2ban can greatly reduce the impact of brute force attacks on the server. Commonly used commands are:
- fail2ban-client status: Check the status of fail2ban.
- fail2ban-client set ssh banip 10.0.0.1: Use this command to add the IP address 10.0.0.1 to the SSH ban list.
- chown and chmod: chown and chmod are commands used to set file permissions and owners. Properly setting file owners and permissions can prevent unauthorized users from accessing sensitive files. Commonly used commands are:
- chown root:root /path/to/file: Set the owner of the file to the root user.
- chmod 700 /path/to/file: Set the file permissions so that only the owner can read, write, and execute.
- ssh-keygen: ssh-keygen is a command used to generate and manage SSH key pairs. Using an SSH key pair provides more secure remote access and prevents unauthorized users from logging in with passwords. Commonly used commands are:
- ssh-keygen -t rsa: Generate an RSA key pair for authentication.
- ssh-copy-id user@server: Copy the public key to the remote server to achieve password-free login.
- Sudo: Sudo is a tool used to authorize ordinary users to execute privileged commands. Using Sudo can limit the use of privileged commands and reduce the risk of attacks by malicious code on your system. Commonly used commands are:
- sudo apt-get update: Use Sudo to execute privileged commands.
- SELinux and AppArmor: SELinux and AppArmor are two mandatory access control tools used to harden Linux security. They reduce potential security vulnerabilities by enforcing which processes can access system resources. Commonly used commands are:
- getenforce: Check the status of SELinux.
- aa-status: View the status of AppArmor.
It is very important to be proficient in using these commands when protecting your Linux server. They can help you build stronger firewalls, block brute force attacks, restrict file access, use secure remote access methods, and harden operating system security. However, be careful when using these commands to avoid accidentally affecting the normal operation of the server.
The above is the detailed content of Protect your Linux server: Become proficient with these commands. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
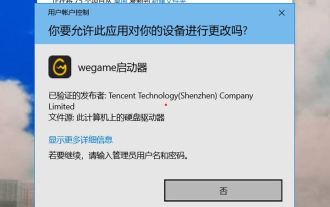 How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
When using Win11 system, sometimes you will encounter a prompt that requires you to enter the administrator username and password. This article will discuss how to deal with this situation. Method 1: 1. Click [Windows Logo], then press [Shift+Restart] to enter safe mode; or enter safe mode this way: click the Start menu and select Settings. Select "Update and Security"; select "Restart Now" in "Recovery"; after restarting and entering the options, select - Troubleshoot - Advanced Options - Startup Settings -&mdash
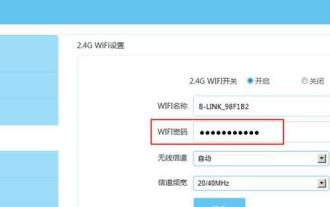 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
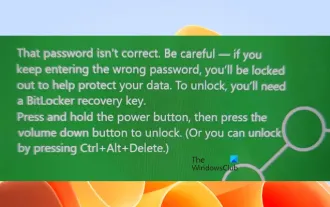 Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
This article will explore how to solve the problem of wrong password, especially the need to be careful when dealing with BitLocker warnings. This warning is triggered when an incorrect password is entered multiple times in BitLocker to unlock the drive. Usually, this warning occurs because the system has a policy that limits incorrect login attempts (usually three login attempts are allowed). In this case, the user will receive an appropriate warning message. The complete warning message is as follows: The password entered is incorrect. Please note that continuously entering incorrect passwords will cause the account to be locked. This is to protect the security of your data. If you need to unlock your account, you will need to use a BitLocker recovery key. The password is incorrect, beware the BitLocker warning you receive when you log in to your computer
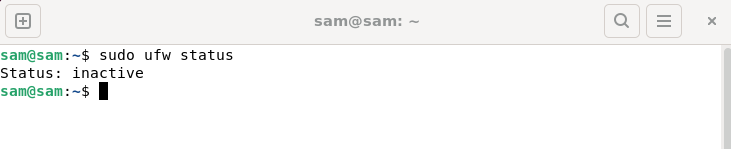 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux
 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
 What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
In the Windows 10 system, the password policy is a set of security rules to ensure that the passwords set by users meet certain strength and complexity requirements. If the system prompts that your password does not meet the password policy requirements, it usually means that your password does not meet the requirements set by Microsoft. standards for complexity, length, or character types, so how can this be avoided? Users can directly find the password policy under the local computer policy to perform operations. Let’s take a look below. Solutions that do not comply with password policy specifications: Change the password length: According to the password policy requirements, we can try to increase the length of the password, such as changing the original 6-digit password to 8-digit or longer. Add special characters: Password policies often require special characters such as @, #, $, etc. I
 Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation? With the wide application of Golang in the field of programming, more and more developers choose to use Golang to develop various types of applications. However, like other programming languages, there are security challenges in Golang development. In particular, Golang's power and flexibility also make it a potential virus creation tool. This article will delve into security issues in Golang development and provide some methods to avoid G
 How to set a password for excel
Mar 21, 2024 am 09:00 AM
How to set a password for excel
Mar 21, 2024 am 09:00 AM
A few days ago, my cousin came to me to complain that he had worked hard to create a lot of data using Excel, but it was later modified by his colleagues. He didn't know the situation at the time. After sending it to his boss, he was scolded. This is really frustrating. Some people just don’t like you and want to deliberately punish you. After you leave school and enter society, you will find that more and more people are stabbing you in the back. In addition to a few words of comfort to my cousin, I also gave my cousin an advice. If you are afraid of encountering such a thing again in the future, then set a password for the excel form so that no one can open it except you. Netizens, if you are afraid that your Excel spreadsheet will be secretly modified by others, you should also set a password. How to set password for excel password form? Come with me to find out! 1.



