 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 One-stop solution: development and deployment of PHP login authentication system
One-stop solution: development and deployment of PHP login authentication system
One-stop solution: development and deployment of PHP login authentication system

In today's digital era, with the rapid development of the Internet, security and privacy issues have become one of the important issues in Internet applications. In various Internet applications, the development and deployment of user login authentication systems is particularly important. This article will introduce the development and deployment of a PHP-based login authentication system to achieve a one-stop solution.
1. Requirements Analysis
Before developing the login authentication system, we must first analyze the requirements. A complete login authentication system should include the following main functions:
- User registration: Provide user registration function and allow users to create new accounts.
- User login: Allow users to log in using registered accounts.
- Password encryption: Encrypt and store the user's password to ensure the security of the user's account.
- Verification code: Provides verification code function to identify and verify users to prevent malicious attacks.
- Remember login status: Allow users to choose the function of remembering login status to facilitate quick login the next time.
- Logout function: Provides users with the function to log out to ensure user privacy and security.
- Security measures: Strict verification and filtering of user input to prevent XSS, CSRF and other attacks.
2. Technology Selection
Based on the above demand analysis, we chose to use PHP as the development language to develop the login authentication system. PHP is a scripting language widely used in web development and has high security and flexibility.
In order to provide a better user experience, we also choose to combine front-end development technology and use HTML, CSS, and JavaScript for page design and interaction.
3. System Development
During the system development process, we need to gradually develop each functional module in the order of demand analysis.
- User Registration
The user registration function is one of the core functions of the system. During the development process, we need to design a registration page that allows users to enter user name, password and other information, and verifies, filters, and encrypts the user's input. In order to prevent malicious registration, we can combine the verification code function for verification. - User login
The user login function is another core function of the system. On the login page, users need to enter the correct username and password to log in. In order to protect the security of users' accounts, we use password encryption algorithms to encrypt and store user passwords and verify them during the login process. - Password encryption
In order to improve the security of the account, we can use the password encryption algorithm to encrypt and store the user's password. Common password encryption algorithms include MD5, SHA-256, bcrypt, etc. During system development, we can choose a suitable encryption algorithm and combine it with salt value to further increase the security of the password. - Verification code
The verification code function can effectively prevent malicious attacks, such as brute force cracking, malicious registration, etc. During the development process, we can use GD Library or a third-party library to generate verification code images and verify the verification code entered by the user. - Remember login status
In order to improve user experience, we can provide the function of remembering login status. By setting Token or Cookie, users can log in quickly the next time they visit. - Logout function
The user logout function is an important guarantee for system security. During the development process, we need to design a logout page that will automatically exit when the user actively exits or does not operate within a certain period of time. - Security Measures
In order to ensure the security of the system, we need to verify and filter user input. By using filters, regular expressions and other methods, user input is strictly verified to prevent XSS, CSRF and other attacks.
4. System Deployment
After the development of the login authentication system is completed, we still need to deploy the system.
- Environment preparation
Ensure that the PHP interpreter and related extensions have been installed on the server, and the corresponding environment variables have been configured. - Website deployment
Deploy the developed login authentication system files to the Web server to ensure that they are accessible on the Internet. - Database configuration
The login authentication system generally needs to use a database to store the user's account information and login status. We need to configure the database connection information in the system to ensure that the login authentication system can access and operate the database normally. - HTTPS configuration
In order to protect user privacy and security, we can configure the HTTPS protocol for the login authentication system and use SSL certificates to encrypt data for transmission.
5. System maintenance
After completing the system deployment, we still need to maintain and update the system. Security checks on the system can be carried out regularly, loopholes can be repaired and the system updated in a timely manner to ensure the stability and security of the system.
Summary
Through the above steps, we can develop a PHP-based login authentication system and successfully deploy it to the server. This system can meet the needs of users to register, log in, remember login status, etc., and improve the security of user accounts through password encryption, verification codes, security measures and other measures. Through the development and deployment of the above one-stop solution, we can ensure the security of users' accounts and privacy, and provide a better user experience.
The above is the detailed content of One-stop solution: development and deployment of PHP login authentication system. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to use Memcache in PHP development?
Nov 07, 2023 pm 12:49 PM
How to use Memcache in PHP development?
Nov 07, 2023 pm 12:49 PM
In web development, we often need to use caching technology to improve website performance and response speed. Memcache is a popular caching technology that can cache any data type and supports high concurrency and high availability. This article will introduce how to use Memcache in PHP development and provide specific code examples. 1. Install Memcache To use Memcache, we first need to install the Memcache extension on the server. In CentOS operating system, you can use the following command
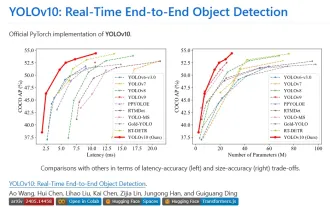 Yolov10: Detailed explanation, deployment and application all in one place!
Jun 07, 2024 pm 12:05 PM
Yolov10: Detailed explanation, deployment and application all in one place!
Jun 07, 2024 pm 12:05 PM
1. Introduction Over the past few years, YOLOs have become the dominant paradigm in the field of real-time object detection due to its effective balance between computational cost and detection performance. Researchers have explored YOLO's architectural design, optimization goals, data expansion strategies, etc., and have made significant progress. At the same time, relying on non-maximum suppression (NMS) for post-processing hinders end-to-end deployment of YOLO and adversely affects inference latency. In YOLOs, the design of various components lacks comprehensive and thorough inspection, resulting in significant computational redundancy and limiting the capabilities of the model. It offers suboptimal efficiency, and relatively large potential for performance improvement. In this work, the goal is to further improve the performance efficiency boundary of YOLO from both post-processing and model architecture. to this end
 How to solve the problem of inaccessibility after Tomcat deploys war package
Jan 13, 2024 pm 12:07 PM
How to solve the problem of inaccessibility after Tomcat deploys war package
Jan 13, 2024 pm 12:07 PM
How to solve the problem that Tomcat cannot successfully access the war package after deploying it requires specific code examples. As a widely used Java Web server, Tomcat allows developers to package their own developed Web applications into war files for deployment. However, sometimes we may encounter the problem of being unable to successfully access the war package after deploying it. This may be caused by incorrect configuration or other reasons. In this article, we'll provide some concrete code examples that address this dilemma. 1. Check Tomcat service
 Best practices and common problem solutions for deploying web projects on Tomcat
Dec 29, 2023 am 08:21 AM
Best practices and common problem solutions for deploying web projects on Tomcat
Dec 29, 2023 am 08:21 AM
Best practices for deploying Web projects with Tomcat and solutions to common problems Introduction: Tomcat, as a lightweight Java application server, has been widely used in Web application development. This article will introduce the best practices and common problem solving methods for Tomcat deployment of web projects, and provide specific code examples to help readers better understand and apply. 1. Project directory structure planning Before deploying a Web project, we need to plan the directory structure of the project. Generally speaking, we can organize it in the following way
 Gunicorn Deployment Guide for Flask Applications
Jan 17, 2024 am 08:13 AM
Gunicorn Deployment Guide for Flask Applications
Jan 17, 2024 am 08:13 AM
How to deploy Flask application using Gunicorn? Flask is a lightweight Python Web framework that is widely used to develop various types of Web applications. Gunicorn (GreenUnicorn) is a Python-based HTTP server used to run WSGI (WebServerGatewayInterface) applications. This article will introduce how to use Gunicorn to deploy Flask applications, with
 How to solve the problem of inaccessibility after Tomcat deploys war package
Jan 13, 2024 am 11:43 AM
How to solve the problem of inaccessibility after Tomcat deploys war package
Jan 13, 2024 am 11:43 AM
The solution to the problem that Tomcat cannot be accessed after deploying the war package requires specific code examples. Introduction: In Web development, Tomcat is one of the most widely used Java Web servers. However, sometimes after we deploy the war package to Tomcat, there is an inaccessible problem. This article will introduce several situations that may lead to inaccessibility, and give corresponding solutions and code examples. 1. Ensure that the war package has been deployed correctly. The first step is to ensure that the war package has been correctly deployed to Tomcat’s webapp.
 Deploy the unbeatable combination of Gunicorn and Flask
Jan 17, 2024 am 10:24 AM
Deploy the unbeatable combination of Gunicorn and Flask
Jan 17, 2024 am 10:24 AM
Gunicorn and Flask: The perfect deployment combination, specific code examples required Overview: It is very important for developers to choose the appropriate deployment method, especially for Python web applications. Among Python web frameworks, Flask is a very popular choice, and Gunicorn is a server for deploying Python applications. This article will introduce the combination of Gunicorn and Flask and provide some specific code examples to help readers
 How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
To successfully deploy and maintain a PHP website, you need to perform the following steps: Select a web server (such as Apache or Nginx) Install PHP Create a database and connect PHP Upload code to the server Set up domain name and DNS Monitoring website maintenance steps include updating PHP and web servers, and backing up the website , monitor error logs and update content.



