 Technology peripherals
Technology peripherals
 It Industry
It Industry
 Anomaly Detection: Minimize False Positives with Rules Engine
Anomaly Detection: Minimize False Positives with Rules Engine
Anomaly Detection: Minimize False Positives with Rules Engine
Anomalies are deviations from expected patterns and can occur in a variety of environments—whether in banking transactions, industrial operations, the marketing industry, or healthcare monitoring. Traditional detection methods often produce high false alarm rates. A false positive occurs when a system incorrectly identifies a routine event as an anomaly, resulting in unnecessary investigation efforts and operational delays. This inefficiency is a pressing problem because it drains resources and diverts attention from the real problems that need to be solved. This article takes an in-depth look at a specialized approach to anomaly detection that makes extensive use of rule-based engines. This approach improves the accuracy of identifying violations by cross-referencing multiple key performance indicators (KPIs). Not only can this approach more effectively verify or disprove the presence of an anomaly, but it can sometimes also isolate and identify the root cause of the problem.
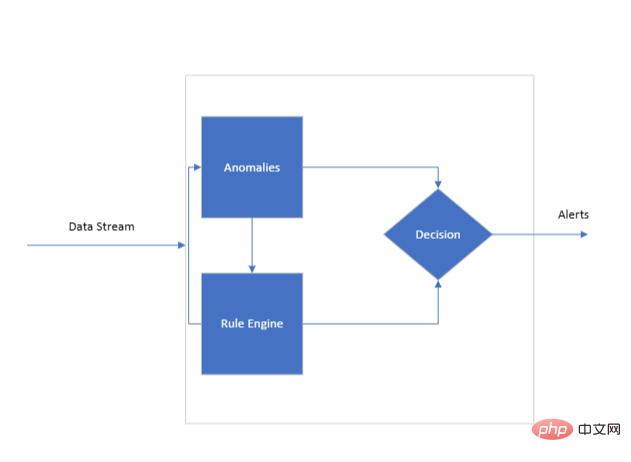
System Architecture Overview
Data Flow
This is the continuous data flow reviewed by the engine. Each point in the flow may be associated with one or more KPIs that are used by the rules engine to evaluate against its training ruleset. A continuous flow of data is essential for real-time monitoring, providing the engine with the necessary information to work.
Rules Engine Architecture
The heart of the system is the rules engine, which needs to be trained to understand the nuances of the KPIs it will monitor. This is where a set of KPI rules comes into play. These rules serve as the algorithmic basis of the engine and are designed to correlate two or more KPIs together.
Type of KPI rules:
- Data quality: rules that focus on the consistency, accuracy and reliability of data flow.
- KPI Relevance: Rules that focus on the relevance of certain KPIs
Rule application process
After receiving the data, the engine immediately looks for deviations or anomalies in the incoming KPIs. An anomaly here refers to any metric that falls outside a predetermined acceptable range. The engine flags these anomalies for further investigation, which can be divided into three main operations: accept, reject, and narrow down. This may involve correlating one KPI with another to validate or negate a detected anomaly.
Method
Rule Formation
The basic steps involve creating a series of KPIs that relate multiple KPIs to each other associated rules. For example, a rule might relate product quality metrics to production speed in a factory setting. For example:
- Direct relationship between KPIs: A "direct relationship" between two KPIs means that when one KPI increases, the other KPI also increases, or when one KPI decreases, the other will also decrease. For example, in a retail business, an increase in advertising spend (KPI1) may be directly related to an increase in sales revenue (KPI2). In this case, an increase in one of the aspects has a positive impact on the other. This knowledge is invaluable to businesses as it aids in strategic planning and resource allocation.
- Inverse relationship between KPIs: On the other hand, an “inverse relationship” means that when one KPI increases, the other KPI decreases and vice versa. For example, in a manufacturing environment, the time it takes to produce a product (KPI1) may have an inverse relationship with productivity (KPI2). As production time is reduced, productivity may increase. Understanding the inverse relationship is also critical for business optimization, as it may require balancing measures to optimize both KPIs.
- Combine KPIs to create new rules: Sometimes it can be beneficial to combine two or more KPIs to create a new metric that can provide valuable insights into business performance. For example, combining Customer Lifetime Value (KPI1) and Customer Acquisition Cost (KPI2) results in a third KPI: Customer Value to Cost Ratio. This new KPI provides a more comprehensive understanding of whether the cost of acquiring a new customer is commensurate with the value it delivers over time.
Training rule engine
The rule engine has been comprehensively trained and can effectively Apply these rules.
Real-time review
The rules engine proactively monitors incoming data, applying its trained rules to identify anomalies or potential anomalies.
Decision
In identifying potential anomalies, the engine:
- Accepting exceptions: Confirmation phase: After an exception is flagged, the engine will compare it with other associated KPIs using its pre-trained KPI rules. The point here is to determine whether the anomaly is actually a problem or just an outlier. This confirmation is done based on the correlation between primary and secondary KPIs.
- Reject exceptions: False positive phase: Not all exceptions indicate a problem; some may be statistical outliers or data errors. In this case, the engine uses its training to reject the anomaly, essentially identifying it as a false positive. This is critical to eliminating unnecessary alert fatigue and focusing resources on the real problem.
- Narrowing down the scope of the exception: Refinement phase: Sometimes, an exception can be part of a larger problem that affects multiple components. Here, the engine further pinpoints the exact nature of the problem by narrowing it down to specific KPI components. This advanced filtering helps quickly identify issues and resolve root causes.
Advantages
- Reduce false positives: By using a rules engine that cross-references multiple KPIs, the system greatly reduces Incidence of false positives.
- Time and Cost Efficiency: Detection and resolution of anomalies is increased, reducing operational time and associated costs.
- Improve Accuracy: The ability to compare and contrast multiple KPIs allows for a more granular and accurate representation of abnormal events.
Conclusion
This article outlines an approach to anomaly detection using a rules engine trained on various KPI rule sets. In contrast to traditional anomaly detection systems, which often rely solely on statistical algorithms or machine learning models, this approach uses a specialized rules engine as its cornerstone. By delving deeper into the relationships and interactions between different KPIs, businesses can gain more granular insights that simple, stand-alone metrics cannot provide. This enables more robust strategic planning, better risk management, and an overall more effective approach to achieving business goals. Once an anomaly is flagged, the engine compares it to other associated KPIs using its pre-trained KPI rules. The point here is to determine whether the anomaly is actually a problem or just an outlier.
The above is the detailed content of Anomaly Detection: Minimize False Positives with Rules Engine. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to use PHP to implement anomaly detection and fraud analysis
Jul 30, 2023 am 09:42 AM
How to use PHP to implement anomaly detection and fraud analysis
Jul 30, 2023 am 09:42 AM
How to use PHP to implement anomaly detection and fraud analysis Abstract: With the development of e-commerce, fraud has become a problem that cannot be ignored. This article introduces how to use PHP to implement anomaly detection and fraud analysis. By collecting user transaction data and behavioral data, combined with machine learning algorithms, user behavior is monitored and analyzed in real time in the system, potential fraud is identified, and corresponding measures are taken to deal with it. Keywords: PHP, anomaly detection, fraud analysis, machine learning 1. Introduction With the rapid development of e-commerce, the number of transactions people conduct on the Internet
 Nginx security performance monitoring and anomaly detection
Jun 10, 2023 pm 04:15 PM
Nginx security performance monitoring and anomaly detection
Jun 10, 2023 pm 04:15 PM
Nginx is a free, open source, high-performance, lightweight HTTP server software that is widely used on the Internet. However, because Nginx often faces the public network and is responsible for important Web services, it needs to perform regular security performance monitoring and anomaly detection, and take timely and effective security measures to ensure the normal operation of the website and the security of data. 1. Nginx security performance monitoring Nginx security performance monitoring mainly includes the following aspects: (1) Nginx access log monitoring Nginx
 MySql log monitoring: How to quickly detect and analyze MySQL errors and exceptions
Jun 15, 2023 pm 09:42 PM
MySql log monitoring: How to quickly detect and analyze MySQL errors and exceptions
Jun 15, 2023 pm 09:42 PM
With the advent of the Internet and big data era, MySQL database, as a commonly used open source database management system, is adopted by more and more companies and organizations. However, in the actual application process, various errors and exceptions may occur in the MySQL database, such as system crashes, query timeouts, deadlocks, etc. These anomalies will have a serious impact on system stability and data integrity. Therefore, quickly detecting and analyzing MySQL errors and anomalies is a very important task. Log monitoring is an important function of MySQL
 Anomaly detection examples in Python
Jun 09, 2023 pm 09:33 PM
Anomaly detection examples in Python
Jun 09, 2023 pm 09:33 PM
Python is a high-level programming language that is easy to learn and powerful. Due to its high readability, small amount of code, and easy maintenance, it is widely used in scientific computing, data analysis, artificial intelligence and other fields. However, any programming language will encounter errors and exceptions, so Python also provides an exception mechanism so that developers can better handle these situations. This article will introduce how to use the anomaly detection mechanism in Python and give some examples. 1. Exception types in Python in Py
 Best practices and algorithm selection for data reliability validation and model evaluation in Python
Oct 27, 2023 pm 12:01 PM
Best practices and algorithm selection for data reliability validation and model evaluation in Python
Oct 27, 2023 pm 12:01 PM
How to perform best practices and algorithm selection for data reliability verification and model evaluation in Python Introduction: In the field of machine learning and data analysis, verifying the reliability of data and evaluating the performance of the model are very important tasks. By verifying the reliability of the data, the quality and accuracy of the data can be guaranteed, thereby improving the predictive power of the model. Model evaluation can help us select the best models and determine their performance. This article will introduce best practices and algorithm choices for data reliability verification and model evaluation in Python
 Anomaly detection problem based on time series
Oct 09, 2023 pm 04:33 PM
Anomaly detection problem based on time series
Oct 09, 2023 pm 04:33 PM
The problem of anomaly detection based on time series requires specific code examples. Time series data is data recorded in a certain order over time, such as stock prices, temperature changes, traffic flow, etc. In practical applications, anomaly detection of time series data is of great significance. An outlier can be an extreme value that is inconsistent with normal data, noise, erroneous data, or an unexpected event in a specific situation. Anomaly detection can help us discover these anomalies and take appropriate measures. For time series anomaly detection problems, commonly used
 Python for time series analysis: forecasting and anomaly detection
Aug 31, 2023 pm 08:09 PM
Python for time series analysis: forecasting and anomaly detection
Aug 31, 2023 pm 08:09 PM
Python has become the language of choice for data scientists and analysts, offering comprehensive data analysis libraries and tools. In particular, Python excels in time series analysis and excels in forecasting and anomaly detection. With its simplicity, versatility, and strong support for statistical and machine learning techniques, Python provides an ideal platform for extracting valuable insights from time-dependent data. This article explores Python's remarkable capabilities for time series analysis, focusing on forecasting and anomaly detection. By delving into the practical aspects of these tasks, we highlight how Python's libraries and tools enable accurate forecasting and identification of anomalies in time series data. Through real-world examples and demonstrative input
 How to implement anomaly detection algorithm in C#
Sep 19, 2023 am 08:09 AM
How to implement anomaly detection algorithm in C#
Sep 19, 2023 am 08:09 AM
How to implement the anomaly detection algorithm in C# requires specific code examples. Introduction: In C# programming, exception handling is a very important part. When errors or unexpected situations occur in the program, the exception handling mechanism can help us handle these errors gracefully to ensure the stability and reliability of the program. This article will introduce in detail how to implement anomaly detection algorithms in C# and give specific code examples. 1. Basic knowledge of exception handling Definition and classification of exceptions Exceptions are errors or unexpected situations encountered when a program is running, which disrupt the normal execution flow of the program.



