Java Development: How to Obfuscate and Encrypt Code

Java development: How to perform code obfuscation and encryption, specific code examples are required
Introduction:
In today's Internet era, protecting the security of software code has become Particularly important. To prevent malicious attackers from reverse engineering, cracking, or tampering with the code, developers need to take steps to enhance the security of the code. Code obfuscation and encryption is a common method. This article will explore how to use Java for code obfuscation and encryption and provide some specific code examples.
Code obfuscation:
Code obfuscation refers to making the code logic obscure and difficult to understand by renaming variables and methods, deleting useless code, and adding meaningless code, thereby increasing reverse engineering. difficulty. The following are some commonly used code obfuscation techniques.
- Variable and method renaming:
You can make your code more difficult to understand by replacing the names of variables and methods with meaningless random strings. For example, replace the variable name "username" with "a", the method name "getUserInfo" with "b", etc.
Sample code:
public class Example {
private String a;
public void b() {
String c = "Hello, World!";
System.out.println(c);
}
public static void main(String[] args) {
Example example = new Example();
example.b();
}
}- Delete useless code:
By deleting unused variables, methods or classes, you can reduce the amount of code and make reverse engineering more efficient difficulty. You can use tools such as ProGuard and JShrink to automatically remove useless code.
Sample code:
public class Example {
public static void main(String[] args) {
int a = 5;
int b = 10;
System.out.println(a + b);
}
}- Add meaningless code:
By adding some meaningless code, such as empty loops, useless conditional judgments, etc., you can make The code logic is more complex, making reverse engineering more difficult.
Sample code:
public class Example {
public static void main(String[] args) {
for (int i = 0; i < 10000; i++) {
// 空循环
}
if (true) {
// 无用的条件判断
}
}
}Code encryption:
Code encryption refers to encrypting the code so that the original executable code can only be obtained after decryption. The following are some commonly used code encryption techniques.
- Symmetric encryption:
Use symmetric encryption algorithms, such as AES, DES, etc., to encrypt and decrypt the code. The encrypted code will only be decrypted and executed when running, which increases the security of the code.
Sample code:
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
public class Example {
public static void main(String[] args) throws Exception {
String plainText = "Hello, World!";
String secretKey = "D0ECAA41770A386C";
// 创建SecretKeySpec对象
SecretKeySpec secretKeySpec = new SecretKeySpec(secretKey.getBytes(), "AES");
// 创建Cipher对象
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, secretKeySpec);
// 加密
byte[] encrypted = cipher.doFinal(plainText.getBytes());
// 解密
cipher.init(Cipher.DECRYPT_MODE, secretKeySpec);
byte[] decrypted = cipher.doFinal(encrypted);
System.out.println(new String(decrypted));
}
}- Hybrid encryption:
Use an asymmetric encryption algorithm, such as RSA, to generate a public and private key pair. Asymmetrically encrypt the secret key used in the symmetric encryption algorithm, and store the encrypted secret key and the encrypted code together. At runtime, the private key is used to decrypt the symmetric encryption key, and then the code is decrypted and executed.
Sample code:
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import javax.crypto.Cipher;
public class Example {
public static void main(String[] args) throws Exception {
String plainText = "Hello, World!";
// 生成公私钥对
KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA");
keyPairGenerator.initialize(1024);
KeyPair keyPair = keyPairGenerator.generateKeyPair();
// 创建Cipher对象
Cipher cipher = Cipher.getInstance("RSA/ECB/PKCS1Padding");
cipher.init(Cipher.ENCRYPT_MODE, keyPair.getPublic());
// 对称加密
String secretKey = "D0ECAA41770A386C";
byte[] encryptedSecretKey = cipher.doFinal(secretKey.getBytes());
// 解密获得秘钥
cipher.init(Cipher.DECRYPT_MODE, keyPair.getPrivate());
byte[] decryptedSecretKey = cipher.doFinal(encryptedSecretKey);
// 使用秘钥解密代码
SecretKeySpec secretKeySpec = new SecretKeySpec(decryptedSecretKey, "AES");
cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, secretKeySpec);
byte[] decrypted = cipher.doFinal(encrypted);
System.out.println(new String(decrypted));
}
}Summary:
Code obfuscation and encryption are important means to enhance code security. By obfuscating and encrypting the code, you can increase the difficulty of reverse engineering the code and effectively prevent malicious attacks. This article introduces commonly used code obfuscation and encryption techniques and provides specific code examples. Developers can choose appropriate code protection methods according to their needs to improve software security.
The above is the detailed content of Java Development: How to Obfuscate and Encrypt Code. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 What are the five options for choosing the Java career path that best suits you?
Jan 30, 2024 am 10:35 AM
What are the five options for choosing the Java career path that best suits you?
Jan 30, 2024 am 10:35 AM
There are five employment directions in the Java industry, which one is suitable for you? Java, as a programming language widely used in the field of software development, has always been popular. Due to its strong cross-platform nature and rich development framework, Java developers have a wide range of employment opportunities in various industries. In the Java industry, there are five main employment directions, including JavaWeb development, mobile application development, big data development, embedded development and cloud computing development. Each direction has its characteristics and advantages. The five directions will be discussed below.
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 Essential for Java development: Recommend the most efficient decompilation tool
Jan 09, 2024 pm 07:34 PM
Essential for Java development: Recommend the most efficient decompilation tool
Jan 09, 2024 pm 07:34 PM
Essential for Java developers: Recommend the best decompilation tool, specific code examples are required Introduction: During the Java development process, we often encounter situations where we need to decompile existing Java classes. Decompilation can help us understand and learn other people's code, or make repairs and optimizations. This article will recommend several of the best Java decompilation tools and provide some specific code examples to help readers better learn and use these tools. 1. JD-GUIJD-GUI is a very popular open source
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
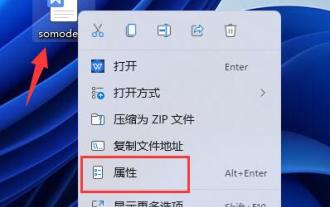 Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Some friends want to protect their files, but don’t know how to encrypt win11 documents. In fact, we can directly use folder encryption or use third-party software to encrypt files. Detailed tutorial on win11 document encryption: 1. First find the file you want to encrypt, right-click to select it, and open "Properties" 2. Then click "Advanced" in the properties column 3. Select "Encrypt content to protect data" in Advanced and click " OK" 4. Then click "OK" to save. 5. Finally, select the desired encryption mode and "OK" to save the document to encrypt the document.
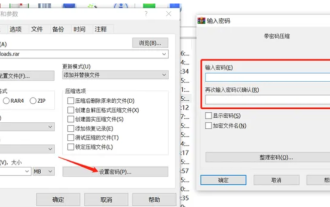 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 Detailed introduction to the encryption and decryption methods of Vim text in CentOS
Dec 31, 2023 pm 02:49 PM
Detailed introduction to the encryption and decryption methods of Vim text in CentOS
Dec 31, 2023 pm 02:49 PM
CentOS uses vim/vi to encrypt and decrypt files 1. Use vim/vi to encrypt: Advantages: After encryption, if you don’t know the password, you cannot see the plain text, including root users; Disadvantages: It is obvious that others know the encryption , it is easy for others to destroy encrypted files, including content destruction and deletion; I believe everyone is familiar with the vi editor. There is a command in vi to encrypt files. For example: 1) First, in the root master Create an experimental file text.txt under the directory /root/: [root@www~]#vim/vitext.txt2) Enter the editing mode, press ESC after entering the content, and then enter: X (note the capital X), Enter; 3)




