 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How to solve external resource calls and access in PHP development
How to solve external resource calls and access in PHP development
How to solve external resource calls and access in PHP development

How to solve the problem of calling and accessing external resources in PHP development requires specific code examples
In PHP development, we often encounter the need to call and access external resources situations, such as API interfaces, databases, file systems, etc. of other websites. Correctly handling and managing calls and access to these external resources is the key to ensuring development efficiency and system stability. This article will share several common solutions and provide specific code examples.
- Use CURL library for API interface calls
CURL is a powerful tool library for data communication with the server. In PHP, we can call the API interface of other websites through the CURL library. The following is a simple example that demonstrates how to use the CURL library to initiate a GET request and obtain the returned results.
<?php
function callApi($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
$response = curl_exec($ch);
curl_close($ch);
return $response;
}
$apiUrl = "http://api.example.com/data";
$response = callApi($apiUrl);
echo $response;
?>- Use PDO library for database operations
PDO (PHP Data Objects) is a database operation abstraction layer of PHP. It provides a unified API interface that can support Many different types of databases, such as MySQL, SQLite, Oracle, etc. The following is a simple example that demonstrates how to use the PDO library to connect to a database and perform query operations.
<?php
$dsn = "mysql:host=localhost;dbname=test";
$username = "root";
$password = "password";
try {
$conn = new PDO($dsn, $username, $password);
$sql = "SELECT * FROM users";
$stmt = $conn->prepare($sql);
$stmt->execute();
$result = $stmt->fetchAll(PDO::FETCH_ASSOC);
print_r($result);
} catch (PDOException $e) {
echo "Error: " . $e->getMessage();
}
?>- Use file processing functions for file system operations
In PHP, there are many file processing functions that can be used to operate the file system, such as reading file contents , write files, delete files, etc. The following is a simple example that demonstrates how to use file processing functions to read the contents of a file and output it.
<?php
$filePath = "/path/to/file.txt";
if(file_exists($filePath)){
$fileContent = file_get_contents($filePath);
echo $fileContent;
} else {
echo "File not found.";
}
?>Summary
In PHP development, it is very important to correctly handle and manage calls and access to external resources. This article introduces solutions for using the CURL library for API interface calls, using the PDO library for database operations, and using file processing functions for file system operations, and provides specific code examples. By rationally using these methods, we can handle external resources more efficiently in PHP development.
The above is the detailed content of How to solve external resource calls and access in PHP development. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to implement single sign-on in PHP
Jun 11, 2023 pm 07:01 PM
How to implement single sign-on in PHP
Jun 11, 2023 pm 07:01 PM
Single sign-on (SSO) is an authentication mechanism that allows users to authenticate across multiple applications and sites using a single set of credentials, such as a username and password. This mechanism can improve user experience and efficiency while also enhancing security. In PHP, implementing single sign-on requires some specific methods. Below we will introduce how to implement single sign-on in PHP. We will divide it into the following steps: Create a user authentication center (AuthenticationCenter) using OAuth2
 How to disable private browsing authentication in Safari: How-to guide for iOS 17
Sep 11, 2023 pm 06:37 PM
How to disable private browsing authentication in Safari: How-to guide for iOS 17
Sep 11, 2023 pm 06:37 PM
In iOS 17, Apple introduced several new privacy and security features to its mobile operating system, one of which is the ability to require two-step authentication for private browsing tabs in Safari. Here's how it works and how to turn it off. On an iPhone or iPad running iOS 17 or iPadOS 17, if you have any Private Browsing tab open in Safari and then exit the session or app, Apple's browser now requires Face ID/TouchID authentication or a passcode to access again they. In other words, if someone gets their hands on your iPhone or iPad while it's unlocked, they still won't be able to view it without knowing your passcode
 How to implement authentication and authorization in PHP applications using JWT
Aug 03, 2023 pm 10:17 PM
How to implement authentication and authorization in PHP applications using JWT
Aug 03, 2023 pm 10:17 PM
How to use JWT to implement authentication and authorization in PHP applications Introduction: With the rapid development of the Internet, authentication and authorization are becoming increasingly important in web applications. JSONWebToken (JWT) is a popular authentication and authorization mechanism that is widely used in PHP applications. This article will introduce how to use JWT to implement authentication and authorization in PHP applications, and provide code examples to help readers better understand the use of JWT. 1. Introduction to JWT JSONWebTo
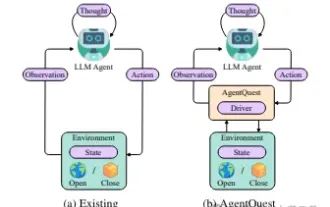 Exploring the boundaries of agents: AgentQuest, a modular benchmark framework for comprehensively measuring and improving the performance of large language model agents
Apr 11, 2024 pm 08:52 PM
Exploring the boundaries of agents: AgentQuest, a modular benchmark framework for comprehensively measuring and improving the performance of large language model agents
Apr 11, 2024 pm 08:52 PM
Based on the continuous optimization of large models, LLM agents - these powerful algorithmic entities have shown the potential to solve complex multi-step reasoning tasks. From natural language processing to deep learning, LLM agents are gradually becoming the focus of research and industry. They can not only understand and generate human language, but also formulate strategies, perform tasks in diverse environments, and even use API calls and coding to Build solutions. In this context, the introduction of the AgentQuest framework is a milestone. It not only provides a modular benchmarking platform for the evaluation and advancement of LLM agents, but also provides researchers with a Powerful tools to track and improve the performance of these agents at a more granular level
 Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Authentication is one of the most important parts of any web application. This tutorial discusses token-based authentication systems and how they differ from traditional login systems. By the end of this tutorial, you will see a fully working demo written in Angular and Node.js. Traditional Authentication Systems Before moving on to token-based authentication systems, let’s take a look at traditional authentication systems. The user provides their username and password in the login form and clicks Login. After making the request, authenticate the user on the backend by querying the database. If the request is valid, a session is created using the user information obtained from the database, and the session information is returned in the response header so that the session ID is stored in the browser. Provides access to applications subject to
 How to use PHP to call web services and APIs?
Jun 30, 2023 pm 03:03 PM
How to use PHP to call web services and APIs?
Jun 30, 2023 pm 03:03 PM
How to use PHP's Web services and API calls With the continuous development of Internet technology, Web services and API calls have become an indispensable part of developers. By using web services and API calls, we can easily interact with other applications to obtain data or implement specific functions. As a popular server-side scripting language, PHP also provides a wealth of functions and tools to support the development of Web services and API calls. In this article, I will briefly introduce how to use PHP to
 Implementing user authentication using middleware in the Slim framework
Jul 29, 2023 am 10:22 AM
Implementing user authentication using middleware in the Slim framework
Jul 29, 2023 am 10:22 AM
Implementing user authentication using middleware in the Slim framework With the development of web applications, user authentication has become a crucial feature. In order to protect users' personal information and sensitive data, we need a reliable method to verify the user's identity. In this article, we will introduce how to implement user authentication using the Slim framework’s middleware. The Slim framework is a lightweight PHP framework that provides a simple and fast way to build web applications. One of the powerful features is the middle
 User authentication and authorization in Flask
Jun 17, 2023 pm 06:02 PM
User authentication and authorization in Flask
Jun 17, 2023 pm 06:02 PM
With the widespread use of web applications, security and data protection have become an important issue in web application development. To ensure the security of web applications, user authentication and authorization are required. As a popular web development framework, Flask provides many mechanisms for implementing user authentication and authorization. User Authentication User authentication refers to using a certain authentication method to determine whether the user's identity is legitimate when the user accesses the Web application. Flask offers a lot





