 Backend Development
Backend Development
 C#.Net Tutorial
C#.Net Tutorial
 Common file encryption and decryption algorithm issues in C#
Common file encryption and decryption algorithm issues in C#
Common file encryption and decryption algorithm issues in C#

Common file encryption and decryption algorithm problems in C# require specific code examples
In modern computer applications, data protection and security are particularly important. File encryption and decryption algorithms are a commonly used data security protection measure to ensure that files are not accessed and modified by unauthorized personnel during transmission and storage. This article will explore common file encryption and decryption algorithm issues in C# and provide corresponding specific code examples.
- Symmetric encryption algorithm
The symmetric encryption algorithm is an algorithm that uses the same key for encryption and decryption. Common symmetric encryption algorithms in C# include DES, AES and RC4. Here we take the DES algorithm as an example to show the specific implementation of file encryption and decryption.
First, we need to define a function to generate a random key:
public static byte[] GenerateRandomKey()
{
byte[] key = new byte[8];
using (var rng = new RNGCryptoServiceProvider())
{
rng.GetBytes(key);
}
return key;
}Next, we can use the generated key to encrypt and decrypt files. The following is an example of using the DES algorithm for file encryption:
public static void EncryptFile(string inputFile, string outputFile, byte[] key)
{
using (var des = new DESCryptoServiceProvider())
{
des.Key = key;
des.Mode = CipherMode.ECB;
using (var fsInput = new FileStream(inputFile, FileMode.Open, FileAccess.Read))
{
using (var fsOutput = new FileStream(outputFile, FileMode.Create, FileAccess.Write))
{
using (var cryptoStream = new CryptoStream(fsOutput, des.CreateEncryptor(), CryptoStreamMode.Write))
{
byte[] buffer = new byte[1024];
int bytesRead;
while ((bytesRead = fsInput.Read(buffer, 0, buffer.Length)) > 0)
{
cryptoStream.Write(buffer, 0, bytesRead);
}
}
}
}
}
}In the above example code, we use the DESCryptoServiceProvider class to create an instance of the DES encryption algorithm. Then, we use the CreateEncryptor method to generate the encryptor and write the encrypted data to the output file.
The process of decrypting files is similar to encryption, just change creating an encryptor to creating a decryptor. The following is an example of file decryption using the DES algorithm:
public static void DecryptFile(string inputFile, string outputFile, byte[] key)
{
using (var des = new DESCryptoServiceProvider())
{
des.Key = key;
des.Mode = CipherMode.ECB;
using (var fsInput = new FileStream(inputFile, FileMode.Open, FileAccess.Read))
{
using (var fsOutput = new FileStream(outputFile, FileMode.Create, FileAccess.Write))
{
using (var cryptoStream = new CryptoStream(fsOutput, des.CreateDecryptor(), CryptoStreamMode.Write))
{
byte[] buffer = new byte[1024];
int bytesRead;
while ((bytesRead = fsInput.Read(buffer, 0, buffer.Length)) > 0)
{
cryptoStream.Write(buffer, 0, bytesRead);
}
}
}
}
}
}- Asymmetric Encryption Algorithm
Asymmetric encryption algorithm is a method that uses a pair of keys for encryption and decryption algorithm, including public and private keys. Common asymmetric encryption algorithms in C# include RSA and DSA.
When using an asymmetric encryption algorithm to encrypt and decrypt files, you first need to generate a pair of keys. The following is an example of using the RSA algorithm to generate a key:
public static void GenerateKeyPair(out string publicKey, out string privateKey)
{
using (var rsa = new RSACryptoServiceProvider())
{
publicKey = rsa.ToXmlString(false);
privateKey = rsa.ToXmlString(true);
}
}After generating the key, we can use the public key to encrypt the file and the private key to decrypt the file. The following is an example of using the RSA algorithm for file encryption:
public static void EncryptFile(string inputFile, string outputFile, string publicKey)
{
using (var rsa = new RSACryptoServiceProvider())
{
rsa.FromXmlString(publicKey);
using (var fsInput = new FileStream(inputFile, FileMode.Open, FileAccess.Read))
{
using (var fsOutput = new FileStream(outputFile, FileMode.Create, FileAccess.Write))
{
using (var cryptoStream = new CryptoStream(fsOutput, rsa.Encryptor, CryptoStreamMode.Write))
{
byte[] buffer = new byte[1024];
int bytesRead;
while ((bytesRead = fsInput.Read(buffer, 0, buffer.Length)) > 0)
{
cryptoStream.Write(buffer, 0, bytesRead);
}
}
}
}
}
}In the above example code, we create an RSACryptoServiceProvider instance based on the public key, and use the Encryptor attribute to obtain the encryptor and write the encrypted data to the output in the file.
The process of decrypting files is similar to encryption, just change creating an encryptor to creating a decryptor. The following is an example of using the RSA algorithm for file decryption:
public static void DecryptFile(string inputFile, string outputFile, string privateKey)
{
using (var rsa = new RSACryptoServiceProvider())
{
rsa.FromXmlString(privateKey);
using (var fsInput = new FileStream(inputFile, FileMode.Open, FileAccess.Read))
{
using (var fsOutput = new FileStream(outputFile, FileMode.Create, FileAccess.Write))
{
using (var cryptoStream = new CryptoStream(fsOutput, rsa.Decryptor, CryptoStreamMode.Write))
{
byte[] buffer = new byte[1024];
int bytesRead;
while ((bytesRead = fsInput.Read(buffer, 0, buffer.Length)) > 0)
{
cryptoStream.Write(buffer, 0, bytesRead);
}
}
}
}
}
}Summary:
File encryption and decryption algorithms are important means of protecting data security. This article introduces common symmetric and asymmetric encryption algorithms in C# and provides corresponding code examples. By understanding and applying these encryption algorithms, we can protect the confidentiality and integrity of files and ensure the security of data during transmission and storage.
The above is the detailed content of Common file encryption and decryption algorithm issues in C#. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1375
1375
 52
52
 Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Revealing the causes of HTTP status code 460
Feb 19, 2024 pm 08:30 PM
Decrypting HTTP status code 460: Why does this error occur? Introduction: In daily network use, we often encounter various error prompts, including HTTP status codes. These status codes are a mechanism defined by the HTTP protocol to indicate the processing of a request. Among these status codes, there is a relatively rare error code, namely 460. This article will delve into this error code and explain why this error occurs. Definition of HTTP status code 460: First, we need to understand the basics of HTTP status code
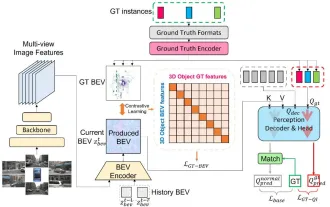 CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
Written above & the author’s personal understanding: At present, in the entire autonomous driving system, the perception module plays a vital role. The autonomous vehicle driving on the road can only obtain accurate perception results through the perception module. The downstream regulation and control module in the autonomous driving system makes timely and correct judgments and behavioral decisions. Currently, cars with autonomous driving functions are usually equipped with a variety of data information sensors including surround-view camera sensors, lidar sensors, and millimeter-wave radar sensors to collect information in different modalities to achieve accurate perception tasks. The BEV perception algorithm based on pure vision is favored by the industry because of its low hardware cost and easy deployment, and its output results can be easily applied to various downstream tasks.
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.
 Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
The convergence of artificial intelligence (AI) and law enforcement opens up new possibilities for crime prevention and detection. The predictive capabilities of artificial intelligence are widely used in systems such as CrimeGPT (Crime Prediction Technology) to predict criminal activities. This article explores the potential of artificial intelligence in crime prediction, its current applications, the challenges it faces, and the possible ethical implications of the technology. Artificial Intelligence and Crime Prediction: The Basics CrimeGPT uses machine learning algorithms to analyze large data sets, identifying patterns that can predict where and when crimes are likely to occur. These data sets include historical crime statistics, demographic information, economic indicators, weather patterns, and more. By identifying trends that human analysts might miss, artificial intelligence can empower law enforcement agencies
 Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
01 Outlook Summary Currently, it is difficult to achieve an appropriate balance between detection efficiency and detection results. We have developed an enhanced YOLOv5 algorithm for target detection in high-resolution optical remote sensing images, using multi-layer feature pyramids, multi-detection head strategies and hybrid attention modules to improve the effect of the target detection network in optical remote sensing images. According to the SIMD data set, the mAP of the new algorithm is 2.2% better than YOLOv5 and 8.48% better than YOLOX, achieving a better balance between detection results and speed. 02 Background & Motivation With the rapid development of remote sensing technology, high-resolution optical remote sensing images have been used to describe many objects on the earth’s surface, including aircraft, cars, buildings, etc. Object detection in the interpretation of remote sensing images
 How to set up word decryption
Mar 20, 2024 pm 04:36 PM
How to set up word decryption
Mar 20, 2024 pm 04:36 PM
In today's work environment, everyone's awareness of confidentiality is getting stronger and stronger, and encryption operations are often performed to protect files when using software. Especially for key documents, the awareness of confidentiality should be increased, and the security of documents should be given top priority at all times. So I don’t know how well everyone understands word decryption. How to operate it specifically? Today we will actually show you the process of word decryption through the explanation below. Friends who need to learn word decryption knowledge should not miss today's course. A decryption operation is first required to protect the file, which means that the file is processed as a protective document. After doing this to a file, a prompt pops up when you open the file again. The way to decrypt the file is to enter the password, so you can directly
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction



