Common security vulnerabilities and security strategies in Java development

Common security vulnerabilities and security strategies in Java development require specific code examples
With the rapid development of the Internet, Java, as a widely used programming language, More and more applications are developed based on Java. However, due to some common security vulnerabilities in the Java development process, such as cross-site scripting attacks (XSS), SQL injection attacks, cross-site request forgery (CSRF), etc., these vulnerabilities have brought serious security risks to applications. This article will introduce these common security vulnerabilities and provide relevant security strategies and specific code examples to help developers strengthen the security of their applications.
1. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a common Internet attack method. The attacker inserts malicious code into the web page. Script, when the user browses the webpage, the malicious script will be executed, resulting in dangers such as user privacy leakage and account theft.
To prevent cross-site scripting attacks, Java developers can use the ESAPI (Enterprise Security API) recommended by OWASP to filter input.
For example, if there is a <script></script> tag in the form submitted by the user, the input can be filtered through the following code example:
import org.owasp.esapi.ESAPI;
import org.owasp.esapi.filters.SecurityWrapperRequest;
// ...
SecurityWrapperRequest request = new SecurityWrapperRequest(request);
String input = request.getParameter("input");
String safeInput = ESAPI.encoder().canonicalize(input);
safeInput = ESAPI.encoder().encodeForHTML(safeInput);
// 使用安全的输入进行处理By using ESAPI's## In the #encoder().canonicalize() and encoder().encodeForHTML() methods, we filter and escape the user input to ensure that the input does not contain malicious scripts.
String username = request.getParameter("username");
String password = request.getParameter("password");
String sql = "SELECT * FROM users WHERE username = ? AND password = ?";
PreparedStatement statement = connection.prepareStatement(sql);
statement.setString(1, username);
statement.setString(2, password);
ResultSet resultSet = statement.executeQuery();
// 处理查询结果?) to Query statements can prevent maliciously constructed SQL injection attacks.
// 在用户登录成功后,将Token保存在session中
String token = generateToken();
request.getSession().setAttribute("token", token);
// 在表单中添加Token隐藏字段,确保提交的请求是合法的
<input type="hidden" name="token" value="${token}">
// 在服务器端验证Token的合法性
String submittedToken = request.getParameter("token");
String sessionToken = (String) request.getSession().getAttribute("token");
if (submittedToken.equals(sessionToken)) {
// Token验证通过
// 处理请求
} else {
// Token验证失败,可能是CSRF攻击
// 拒绝请求并记录日志
}The above is the detailed content of Common security vulnerabilities and security strategies in Java development. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
In the field of technological innovation, artificial intelligence (AI) is one of the most transformative and promising developments of our time. Artificial intelligence has revolutionized many industries, from healthcare and finance to transportation and entertainment, with its ability to analyze large amounts of data, learn from patterns, and make intelligent decisions. However, despite its remarkable progress, AI also faces significant limitations and challenges that prevent it from reaching its full potential. In this article, we will delve into the top ten limitations of artificial intelligence, revealing the limitations faced by developers, researchers, and practitioners in this field. By understanding these challenges, it is possible to navigate the complexities of AI development, reduce risks, and pave the way for responsible and ethical advancement of AI technology. Limited data availability: The development of artificial intelligence depends on data
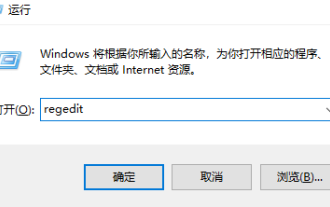 How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
When we no longer want to continue using the current Win10 Enterprise Edition 2016 Long-Term Service Edition, we can choose to switch to the Professional Edition. The method is also very simple. We only need to change some contents and install the system image. How to change win10 enterprise version 2016 long-term service version to professional version 1. Press win+R, and then enter "regedit" 2. Paste the following path directly in the address bar above: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion3 , then find the EditionID and replace the content with "professional" to confirm
 Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Microsoft previously provided dns encryption services for win11, but many users do not know how to use win11 encrypted dns. In fact, we only need to open the dns settings under network settings. Detailed tutorial on win11 encrypted dns: 1. First enter the disk and find the folder you want to encrypt. 2. Then open "Ethernet" on the right 3. Then find the DNS server allocation below and click "Edit" 4. After changing "Auto (DHCP)" to "Manual", open "IPv4" below 5. After turning it on, enter "8.8.8.8" in the preferred DNS 6. Then change the preferred DNS encryption to "Encryption only (DNS over HTTPS)" 7. After the changes are completed, click "Save" and you will find
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
 Methods to solve localstorage security vulnerabilities
Jan 13, 2024 pm 01:43 PM
Methods to solve localstorage security vulnerabilities
Jan 13, 2024 pm 01:43 PM
Security vulnerabilities in localstorage and how to solve them With the development of the Internet, more and more applications and websites are beginning to use WebStorage API, of which localstorage is the most commonly used one. Localstorage provides a mechanism to store data on the client side, persisting data across page sessions regardless of session end or page refresh. However, just because of the convenience and wide application of localstorage, it also has some security vulnerabilities.
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
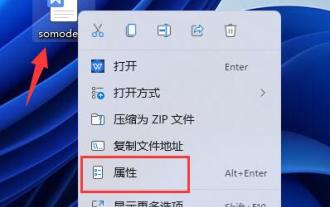 Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Some friends want to protect their files, but don’t know how to encrypt win11 documents. In fact, we can directly use folder encryption or use third-party software to encrypt files. Detailed tutorial on win11 document encryption: 1. First find the file you want to encrypt, right-click to select it, and open "Properties" 2. Then click "Advanced" in the properties column 3. Select "Encrypt content to protect data" in Advanced and click " OK" 4. Then click "OK" to save. 5. Finally, select the desired encryption mode and "OK" to save the document to encrypt the document.




