PHP实现文件安全下载_PHP
你可能会笑我"下载文件"如此简单都值得说?当然并不是想象那么简单。例如你希望客户要填完一份表格,才可以下载某一文件,你第一个想法一定是用 "Redirect"的方法,先检查表格是否已经填写完毕和完整,然后就将网址指到该文件,这样客户才能下载,但如果你想做一个关于"网上购物"的电子商务网站,考虑安全问题,你不想用户直接复制网址下载该文件,笔者建议你使用PHP直接读取该实际文件然后下载的方法去做。程序如下:
$file_name = "tianhys.exee";
$file_dir = "/public/www/download/";
if (!file_exists($file_dir . $file_name)) { //检查文件是否存在
echo "文件找不到";
exit;
} else {
$file = fopen($file_dir . $file_name,"r"); // 打开文件
// 输入文件标签
Header("Content-type: application/octet-stream");
Header("Accept-Ranges: bytes");
Header("Accept-Length: ".filesize($file_dir . $file_name));
Header("Content-Disposition: attachment; filename=" .$file_name);
// 输出文件内容
echo fread($file,filesize($file_dir . $file_name));
fclose($file);
exit;}
而如果文件路径是"http" 或者 "ftp" 网址的话,则源代码会有少许改变,程序如下:
$file_name = "tianhys.exe";
$file_dir = "http://www.tianhys.org/";
$file = @ fopen($file_dir . $file_name,"r");
if (!$file) {
echo "文件找不到";
} else {
Header("Content-type: application/octet-stream");
Header("Content-Disposition: attachment; filename=" .$file_name);
while (!feof ($file)) {
echo fread($file,50000);
}
fclose ($file);
}
这样就可以用PHP直接输出文件

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Introduction to how to download and install the superpeople game
Mar 30, 2024 pm 04:01 PM
Introduction to how to download and install the superpeople game
Mar 30, 2024 pm 04:01 PM
The superpeople game can be downloaded through the steam client. The size of this game is about 28G. It usually takes one and a half hours to download and install. Here is a specific download and installation tutorial for you! New method to apply for global closed testing 1) Search for "SUPERPEOPLE" in the Steam store (steam client download) 2) Click "Request access to SUPERPEOPLE closed testing" at the bottom of the "SUPERPEOPLE" store page 3) After clicking the request access button, The "SUPERPEOPLECBT" game can be confirmed in the Steam library 4) Click the install button in "SUPERPEOPLECBT" and download
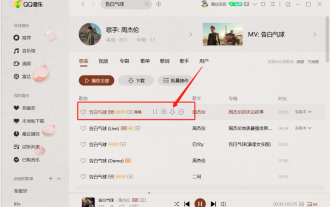 How to download qq music to USB flash drive? -How to download qq music to USB disk
Apr 01, 2024 am 10:11 AM
How to download qq music to USB flash drive? -How to download qq music to USB disk
Apr 01, 2024 am 10:11 AM
1. Open QQ Music software, enter the name of your favorite song in the search bar, and click the download button. 2. Open the folder where the downloaded songs are stored. 3. Copy the downloaded songs to the USB flash drive, and that’s it! Of course, you need to open the U disk first, then open the U disk in "My Computer" and paste it.
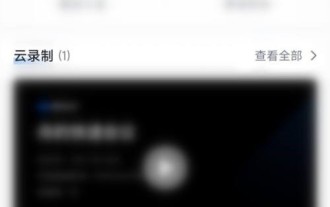 How to download meeting minutes from Tencent Conference_How to download meeting minutes from Tencent Conference
Apr 02, 2024 pm 03:30 PM
How to download meeting minutes from Tencent Conference_How to download meeting minutes from Tencent Conference
Apr 02, 2024 pm 03:30 PM
1. First open Tencent Meeting and click [History Meeting] on the homepage. 2. After entering the meeting, click [Cloud Recording] to download. 3. Finally, to download the cloud recording video, the meeting host needs to enable the download permission and have the permission to view the recording file.
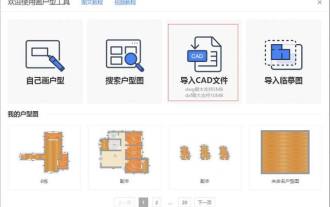 How to download cad floor plans from Kujiale_How to download cad floor plans from Kujiale
Apr 02, 2024 pm 01:25 PM
How to download cad floor plans from Kujiale_How to download cad floor plans from Kujiale
Apr 02, 2024 pm 01:25 PM
1. Import from the pop-up window of the home-building tool when you first enter it. Click [Start Design] in Cloud Design, enter the tool page and select CAD import. Note: Currently only DWG/DXF format is supported, DWG does not exceed 5MB, and DXF does not exceed 10MB. 2. Import from the House Plan Tool. Click [Import]-[Import CAD] on the House Plan Tool page. Step 2: Adjust the imported CAD house plan. After importing into CAD, as shown in the figure below, there are some walls that have not been generated. Click the wall drawing tool in the upper left corner of the house plan interface to fill it (the red box position in the figure). After drawing the wall, on the left Select the door and window model and drag it to the wall for decoration. Note: 3D decoration design cannot be carried out for units that are not closed. After adjusting the positions of doors and windows and the door opening direction, remember to assign commands to each room.
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 AI's new world challenges: What happened to security and privacy?
Mar 31, 2024 pm 06:46 PM
AI's new world challenges: What happened to security and privacy?
Mar 31, 2024 pm 06:46 PM
The rapid development of generative AI has created unprecedented challenges in privacy and security, triggering urgent calls for regulatory intervention. Last week, I had the opportunity to discuss the security-related impacts of AI with some members of Congress and their staff in Washington, D.C. Today's generative AI reminds me of the Internet in the late 1980s, with basic research, latent potential, and academic uses, but it's not yet ready for the public. This time, unchecked vendor ambition, fueled by minor league venture capital and inspired by Twitter echo chambers, is rapidly advancing AI’s “brave new world.” The "public" base model is flawed and unsuitable for consumer and commercial use; privacy abstractions, if present, leak like a sieve; security structures are important because of the attack surface
 Full analysis of Go language file renaming operation
Apr 08, 2024 pm 03:30 PM
Full analysis of Go language file renaming operation
Apr 08, 2024 pm 03:30 PM
The os.Rename function is used in Go language to rename files. The syntax is: funcRename(oldpath,newpathstring)error. This function renames the file specified by oldpath to the file specified by newpath. Examples include simple renaming, moving files to different directories, and ignoring error handling. The Rename function performs an atomic operation and may only update directory entries when the two files are in the same directory. Renames may fail across volumes or while a file is in use.
 How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to Implement PHP Security Best Practices PHP is one of the most popular backend web programming languages used for creating dynamic and interactive websites. However, PHP code can be vulnerable to various security vulnerabilities. Implementing security best practices is critical to protecting your web applications from these threats. Input validation Input validation is a critical first step in validating user input and preventing malicious input such as SQL injection. PHP provides a variety of input validation functions, such as filter_var() and preg_match(). Example: $username=filter_var($_POST['username'],FILTER_SANIT






