 Technology peripherals
Technology peripherals
 AI
AI
 Why is user operation difficult to do? How does AI help companies improve user LTV?
Why is user operation difficult to do? How does AI help companies improve user LTV?
Why is user operation difficult to do? How does AI help companies improve user LTV?
With the popularization of the Internet and market saturation, the cost of customer acquisition is gradually increasing, and user operations are becoming more and more difficult. Is there any way to overcome the current difficulties and improve user LTV? This article summarizes how to use artificial intelligence to improve user LTV. I hope it can inspire you
With the popularity of the Internet and the increase in market saturation, the cost of attracting new users has gradually increased, and the traffic growth of various industries has encountered a bottleneck. In this case, enterprises will pay more attention to the management of existing users and improve user retention rate, activity, payment rate and user life cycle value
Existing users have established trust, usage habits and consumption records, so they are expected to become long-term and stable loyal users through refined operations. User operation has gradually become an indispensable part of each brand. For enterprises, user operation is the key to improving user satisfaction, maintaining user loyalty, and increasing product/service sales.
What are the main aspects of user operation difficulties?
However, user operation is not easy and faces many challenges: including market competition, complexity of user behavior, technological development, increasing user expectations, difficulty in obtaining and analyzing data, etc.
- Changing user behavior and needs: User behavior and needs are changing at any time and are affected by various factors such as the external environment, social trends, new technologies, etc., and it is difficult to satisfy users unchanged.
- Market competition is fierce: Competition in the industry is fierce, with companies vying for users’ time and attention. In the competition, user operations need to constantly innovate and strive for excellence in order to stand out.
- Technology and data challenges: User operations require analysis, decision-making and implementation based on technology and data. The rapid development of technology and the processing of massive data have become difficult, requiring enterprises to invest a lot of resources to solve technical and data problems. Moreover, user data is huge and diverse. How to obtain valuable information from this data and apply it in practice is a challenge faced by many companies.
- User trust and privacy issues: Users are very concerned about the protection of personal information, so companies need to operate user data legally and compliantly, protect user privacy, and build user trust at the same time.
- Operation strategies are unreasonable or not personalized enough: Some companies lack deep insight into users, and the operational strategies they formulate are not personalized enough and do not meet actual needs. Maintaining long-term user relationships is more challenging than attracting new users, requiring more resources and strategies to maintain user activity and loyalty.
- Organizational structure and talent shortcomings: Some companies may have deficiencies in organizational structure, team configuration or talent reserves, and lack professional user operation talents and corresponding teams.
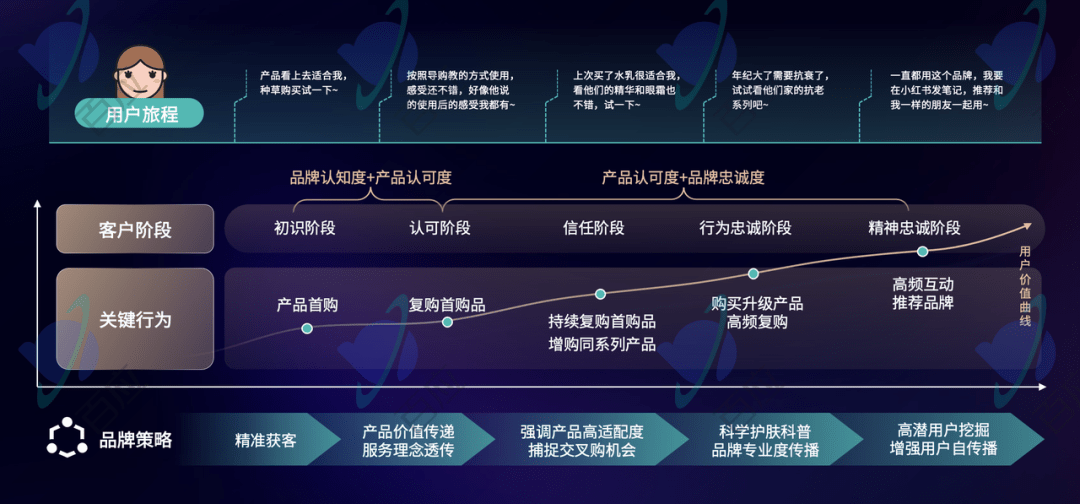
How to improve the effectiveness of user operations to break through difficulties? Is it achieved through a single breakthrough, or by improving the entire operational link? This is very important for every operator
How to establish full-link refined user operations?
From user acquisition, user experience, user retention to user conversion, the full link of user operations covers the entire user process. Enterprises should conduct precise and personalized operations in each link to improve user experience and retention. users, increase user loyalty and satisfaction, and achieve sustained business growth.
- User research and analysis: Understand the characteristics, needs, behavior patterns and preferences of the target user group, and obtain user insights through user research, data analysis and other methods; Build personalized user portraits: Based on user data, establish user portraits and analyze users Behavior, interests and needs lay the foundation for personalized recommendations and customized services.
- Design user life cycle: Divide user operations into different stages, including guiding new users, cultivating active users, retaining lost users, activating silent users, etc., and formulating corresponding operation strategies for each stage.
- Develop user operation strategies: Develop user operation strategies based on user research results, including strategies for different stages such as user acquisition, user activation, user retention, user payment, and user recommendation. Based on user portraits and behavioral data, implement personalized recommendations and marketing, push products or services that match users' interests, and increase users' willingness to purchase.
- Formulate user operation KPI: Set quantifiable key performance indicators (KPI), such as daily active users (DAU), monthly active users (MAU), user retention rate, conversion rate, etc., in order to evaluate the performance of user operations Effect.
- Develop communication and promotion strategies: Determine communication channels and methods suitable for target users, including social media, AI outbound calls, SMS push, App notifications, etc., and formulate corresponding promotion plans.
- Continuous optimization of operation strategies: Regularly analyze user data and operation effects, and timely adjust and optimize user operation strategies to adapt to market changes and changes in user needs.
3. How AI outbound calls can help enterprises operate efficiently and improve user LTV
The current situation of enterprise user operations shows diversified and all-round characteristics. As competition intensifies, the channels and methods for companies to operate users are becoming increasingly diversified. They are committed to establishing lasting user relationships and achieving user acquisition, retention, conversion and promotion through multi-channel and multi-level operations.
AI outbound call technology plays an increasingly important role in user operations. Through AI outbound calls, large-scale and personalized user communication can be achieved, including user information confirmation, product recommendations, service satisfaction surveys, etc. AI outbound calling can save human resources and improve efficiency. At the same time, through intelligent algorithms, communication methods are customized for each user and improve user satisfaction
- Personalized user interaction: AI outbound calls can conduct personalized calls and content push based on the user's historical behavior and data, customize information according to the user's preferences, and improve user participation.
- Intelligent customer service and question answering: AI outbound calls can take on part of the customer service work, answer users' common questions through an intelligent dialogue system, and improve the efficiency of customer service.
- Regular event reminders and invitations: Using AI outbound calls, you can regularly send event reminders and invitations to users to enhance users' attention to specific activities and encourage users to participate.
- User feedback and survey: AI outbound calls can be used for regular user satisfaction surveys or product feedback collection to provide data support for product optimization and improvement.
- Return visits and user care: Through AI outbound calls, regular return visits to users can be realized to understand the user's usage and experience, as well as provide care and assistance.
- Purchase Reminders and Recommendations: AI outbound calls can send purchase reminders, recommendations for specific products, etc. to users based on their purchase history and behavior patterns to increase transaction frequency.
The goal of AI outbound calls is to achieve automated and intelligent user communication and interaction, and to provide existing users with personalized and customized services and information. However, when implementing AI outbound calls, you need to pay attention to ensure that the content and frequency will not cause trouble to users, maintain an appropriate communication rhythm, and respect the privacy and wishes of users
Generally speaking, user operation is the key for enterprises to maintain competitiveness in the digital era. By in-depth understanding of users, providing personalized services, improving rights experience, and utilizing the most advanced AI technology, companies can stand out in the fierce market competition and achieve sustainable development.
This article was originally published by @baiyinguser-operated observation room on Everyone is a Product Manager. Reprinting without permission is prohibited
Title picture comes from Unsplash, based on CC0 protocol
The above is the detailed content of Why is user operation difficult to do? How does AI help companies improve user LTV?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to configure Debian Apache log format
Apr 12, 2025 pm 11:30 PM
How to configure Debian Apache log format
Apr 12, 2025 pm 11:30 PM
This article describes how to customize Apache's log format on Debian systems. The following steps will guide you through the configuration process: Step 1: Access the Apache configuration file The main Apache configuration file of the Debian system is usually located in /etc/apache2/apache2.conf or /etc/apache2/httpd.conf. Open the configuration file with root permissions using the following command: sudonano/etc/apache2/apache2.conf or sudonano/etc/apache2/httpd.conf Step 2: Define custom log formats to find or
 How Tomcat logs help troubleshoot memory leaks
Apr 12, 2025 pm 11:42 PM
How Tomcat logs help troubleshoot memory leaks
Apr 12, 2025 pm 11:42 PM
Tomcat logs are the key to diagnosing memory leak problems. By analyzing Tomcat logs, you can gain insight into memory usage and garbage collection (GC) behavior, effectively locate and resolve memory leaks. Here is how to troubleshoot memory leaks using Tomcat logs: 1. GC log analysis First, enable detailed GC logging. Add the following JVM options to the Tomcat startup parameters: -XX: PrintGCDetails-XX: PrintGCDateStamps-Xloggc:gc.log These parameters will generate a detailed GC log (gc.log), including information such as GC type, recycling object size and time. Analysis gc.log
 How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
In Debian systems, the readdir function is used to read directory contents, but the order in which it returns is not predefined. To sort files in a directory, you need to read all files first, and then sort them using the qsort function. The following code demonstrates how to sort directory files using readdir and qsort in Debian system: #include#include#include#include#include//Custom comparison function, used for qsortintcompare(constvoid*a,constvoid*b){returnstrcmp(*(
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information
 How to configure firewall rules for Debian syslog
Apr 13, 2025 am 06:51 AM
How to configure firewall rules for Debian syslog
Apr 13, 2025 am 06:51 AM
This article describes how to configure firewall rules using iptables or ufw in Debian systems and use Syslog to record firewall activities. Method 1: Use iptablesiptables is a powerful command line firewall tool in Debian system. View existing rules: Use the following command to view the current iptables rules: sudoiptables-L-n-v allows specific IP access: For example, allow IP address 192.168.1.100 to access port 80: sudoiptables-AINPUT-ptcp--dport80-s192.16
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
This guide will guide you to learn how to use Syslog in Debian systems. Syslog is a key service in Linux systems for logging system and application log messages. It helps administrators monitor and analyze system activity to quickly identify and resolve problems. 1. Basic knowledge of Syslog The core functions of Syslog include: centrally collecting and managing log messages; supporting multiple log output formats and target locations (such as files or networks); providing real-time log viewing and filtering functions. 2. Install and configure Syslog (using Rsyslog) The Debian system uses Rsyslog by default. You can install it with the following command: sudoaptupdatesud
 Where is the Debian Nginx log path
Apr 12, 2025 pm 11:33 PM
Where is the Debian Nginx log path
Apr 12, 2025 pm 11:33 PM
In the Debian system, the default storage locations of Nginx's access log and error log are as follows: Access log (accesslog):/var/log/nginx/access.log Error log (errorlog):/var/log/nginx/error.log The above path is the default configuration of standard DebianNginx installation. If you have modified the log file storage location during the installation process, please check your Nginx configuration file (usually located in /etc/nginx/nginx.conf or /etc/nginx/sites-available/ directory). In the configuration file



