What to do if your IP address is attacked
Solutions to IP address attacks include analyzing attack types, setting up firewalls, blocking IP addresses, isolating communication links, notifying relevant agencies, strengthening security protection, collecting evidence, and strengthening security awareness training. Detailed introduction: 1. To analyze the attack type, you first need to analyze the type and method of the attack to understand the attacker's behavior and purpose; 2. Firewall settings, by configuring firewall rules, you can restrict access to the attacked IP; 3. IP blocking , if the attack traffic is very violent and seriously affects the normal operation of the server, you can consider temporarily blocking the attacked server, etc.

When an IP address is attacked, the following measures can be taken to respond and handle it:
1. Analyze the attack type: First, you need to analyze the attack types and methods to understand the attacker’s behavior and purpose. Attack-related information can be collected and analyzed through network security equipment, log analysis, and traffic monitoring. This helps identify response strategies and take appropriate measures.
2. Firewall settings: By configuring firewall rules, you can restrict access to the attacked IP. Based on the source, destination, protocol, port and other information of the attack traffic, corresponding firewall policies can be set to block malicious traffic and reduce the impact of the attack.
3. IP blocking: If the attack traffic is very violent and seriously affects the normal operation of the server, you can consider temporarily blocking the IP address under attack. The attacker's IP address can be added to the blacklist through firewalls, security devices, or server configuration to prohibit them from accessing the attacked server.
4. Communication link isolation: If the attack traffic comes from a specific network or IP segment, you can consider isolating it from that network or IP segment. You can contact the network operator for traffic cleaning and isolation, and divert the attack traffic to specialized cleaning equipment to protect the server under attack.
5. Notify relevant agencies: If the attack has caused serious impact, it can be reported promptly to relevant agencies, such as network operators, security teams or law enforcement agencies. Provide detailed attack information and logs to assist them in investigation and processing.
6. Strengthen security protection: After returning to normal operation, it is necessary to strengthen the security protection measures of the server. The server's operating system and applications can be updated to patch known vulnerabilities; authentication and access control can be strengthened to prevent unauthorized access; important data can be backed up regularly to prevent data loss or damage.
7. Collect evidence: In the process of responding to an attack, evidence of the attack needs to be collected and retained in a timely manner. This includes information such as the time of the attack, characteristics of the attack traffic, and the attacker’s IP address and behavior. This evidence will be important for subsequent investigations and holding the attackers accountable.
8. Security awareness training: Strengthen employee network security awareness training and improve their ability to identify and prevent network attacks. Through education and training, employees can understand common network attack methods and preventive measures to improve the network security level of the entire organization.
In short, when an IP address is attacked, timely measures need to be taken to respond and deal with it. By analyzing attack types, setting up firewalls, blocking IP addresses, isolating communication links, notifying relevant agencies, strengthening security protection, collecting evidence, and strengthening security awareness training, we can effectively mitigate the impact of attacks and protect the security and stable operation of servers. . At the same time, it is recommended to cooperate with network security experts or relevant institutions to strengthen network security protection capabilities.
The above is the detailed content of What to do if your IP address is attacked. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1369
1369
 52
52
 How to set Xiaohongshu not to display IP address? How does it change the id to locate the city?
Mar 27, 2024 pm 03:00 PM
How to set Xiaohongshu not to display IP address? How does it change the id to locate the city?
Mar 27, 2024 pm 03:00 PM
Xiaohongshu is a popular social e-commerce platform where users can share their daily life and discover their favorite products. Some users are more sensitive to personal privacy and hope that their IP address will not be displayed on Xiaohongshu to protect their online privacy. So, how to set Xiaohongshu not to display the IP address? This article will answer this question in detail. 1. How to set Xiaohongshu not to display the IP address? 1. Modify Xiaohongshu settings: Open Xiaohongshu APP, click "Me" in the lower right corner to enter the personal center. Then click on the avatar to enter account settings. In the account settings, find "Privacy Settings" and click to enter. Here, you can find the setting options for IP address, just turn it off. 2. Clear cache: Sometimes, Xiaohongshu may display an error
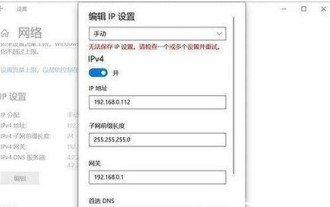 How to solve the problem that Windows 10 IP address cannot be saved after setting it
Jul 08, 2023 pm 12:33 PM
How to solve the problem that Windows 10 IP address cannot be saved after setting it
Jul 08, 2023 pm 12:33 PM
Sometimes everyone encounters the need to manually modify the IP address, but some Windows 10 customers report that the IP address cannot be saved after setting it. How to solve this situation? The IP address is stored basically because there is an error in filling in your IP address. You can check whether the subnet prefix has been written with the subnet mask. If so, change it back. After the change, you can save it normally. IP address. How to solve the problem that the Windows 10 IP address cannot be saved after it is set: The error picture is as follows: The prompt "Unable to save the IP setting, please check one or more settings and try" caused by filling in the error. This is the subnet prefix length, not the subnet mask. as the picture shows. As shown in the picture above, many users actually write out the subnet prefix as the subnet mask.
 Where is the IP address of Xiaomi mobile phone?
Feb 29, 2024 pm 06:10 PM
Where is the IP address of Xiaomi mobile phone?
Feb 29, 2024 pm 06:10 PM
Where is the IP address of Xiaomi mobile phone? You can check the IP address on Xiaomi mobile phone, but most users don’t know where to check the IP address. Next is the graphic tutorial on how to check the IP address of Xiaomi mobile phone brought by the editor. Interested users come and take a look! Where is the IP address of Xiaomi mobile phone? 1. First open the settings function in Xiaomi mobile phone, select [My Device] and click to enter; 2. Then on the My Device function page, click [All Parameters] service; 3. Then on the All Parameters page , slide to the bottom and select [Status Information]; 4. Finally, you can see the IP address in the status information interface.
 Where to change the IP address of Xianyu_Share how to change the IP address of Xianyu
Mar 20, 2024 pm 05:06 PM
Where to change the IP address of Xianyu_Share how to change the IP address of Xianyu
Mar 20, 2024 pm 05:06 PM
Xianyu is a very practical second-hand trading platform. Here we can buy many different products and sell our own idle items. What if we want to modify our address? Let’s take a look with the editor below! Share how to modify the Xianyu IP address. First, open the Xianyu software. After entering the homepage, you can see seafood market, recommendations, address and other options in the upper left corner. Click "Address". 2. Then on the address page, we click the [Down Arrow] next to the address; 3. After the final click, we click on the city on the city selection page;
 How to change the location of Douyin IP address? Why does the IP address change location?
Mar 21, 2024 pm 06:30 PM
How to change the location of Douyin IP address? Why does the IP address change location?
Mar 21, 2024 pm 06:30 PM
Users share their lives, show off their talents, and interact with netizens across the country and even the world through Douyin. Some users wish to change their IP addresses on Douyin due to reasons such as privacy protection or geographical restrictions. So, how does the Douyin IP address change its location? 1. How to change the location of Douyin IP address? A proxy server is an intermediary service used to forward user requests to the Internet and return responses. By configuring a proxy server, users can hide their real IP addresses and change their IP addresses. This approach helps protect user privacy and improves network security. Proxy servers can also be used to access restricted content or bypass geolocation restrictions. Overall, using a proxy server is a practical network tool that can help users browse the Internet more safely and freely.
 PHP implements IP address query function
Jun 22, 2023 pm 11:22 PM
PHP implements IP address query function
Jun 22, 2023 pm 11:22 PM
With the rapid development of the Internet, IP addresses have become an indispensable part of network communications. IP address information is very important in network security monitoring, traffic management, and targeted e-commerce advertising. Therefore, in order to facilitate users to query IP address/domain name information, many websites provide IP address query functions. This article will introduce how to use PHP to implement the IP address query function for readers' reference. 1. What is an IP address? IP address (InternetProtocolAddress) is the network protocol
 Vue Development Notes: Avoid Common Security Vulnerabilities and Attacks
Nov 22, 2023 am 09:44 AM
Vue Development Notes: Avoid Common Security Vulnerabilities and Attacks
Nov 22, 2023 am 09:44 AM
Vue is a popular JavaScript framework that is widely used in web development. As the use of Vue continues to increase, developers need to pay attention to security issues to avoid common security vulnerabilities and attacks. This article will discuss the security matters that need to be paid attention to in Vue development to help developers better protect their applications from attacks. Validating user input In Vue development, validating user input is crucial. User input is one of the most common sources of security vulnerabilities. When handling user input, developers should always
 Bitcoin transaction IP address (Is the Bitcoin transaction IP address public?)
Feb 06, 2024 am 10:03 AM
Bitcoin transaction IP address (Is the Bitcoin transaction IP address public?)
Feb 06, 2024 am 10:03 AM
Bitcoin transaction IP address Bitcoin transaction IP address is an indispensable and important component of the Bitcoin transaction system. It is the core of the Bitcoin trading platform through which Bitcoin traders can conduct Bitcoin transactions. The Bitcoin transaction IP address is the basis of the Bitcoin transaction system and the basis on which Bitcoin traders can conduct Bitcoin transactions. The Bitcoin trading IP address is a global network address used to locate the Bitcoin trading system’s servers and traders’ devices. By querying the Bitcoin transaction IP address, you can obtain transaction status and related information. In addition, Bitcoin trading IP addresses can also be used to connect clients to the Bitcoin trading system and traders’ devices. Are Bitcoin transaction IP addresses public? Bitcoin transaction IP addresses will not be made public



