How to scan and repair security vulnerabilities in Java development projects

How to scan and repair security vulnerabilities in Java development projects
With the rapid development of the Internet, Java development has become the first choice for many companies and individuals. And the security issues that come with it are gradually becoming important. The potential risks that security vulnerabilities bring to projects cannot be ignored. Therefore, it is crucial to scan and repair security vulnerabilities in Java development projects. This article will introduce some methods and tools to help developers effectively scan and repair security vulnerabilities.
- Understand common security vulnerabilities
Before scanning and repairing security vulnerabilities, developers first need to understand some common security vulnerabilities so that they can better locate and repair them. question. Common security vulnerabilities include but are not limited to SQL injection, cross-site scripting attacks (XSS), cross-site request forgery (CSRF), etc. Understanding how these vulnerabilities work can help developers better identify and fix potential security issues.
- Use static code analysis tools
Static code analysis tools can help developers check for security vulnerabilities in the code. These tools can scan code for potential security issues and provide fix recommendations. Common Java static code analysis tools include FindBugs, PMD, SpotBugs, etc. Using these tools can greatly simplify the process of security vulnerability scanning and improve the accuracy and efficiency of scanning.
- Use dynamic code analysis tools
Unlike static code analysis tools, dynamic code analysis tools can simulate attacks in real environments and help developers discover runtime security loopholes. Common Java dynamic code analysis tools include OWASP ZAP and Burp Suite. These tools can simulate various attack scenarios and automatically discover potential security issues. Use dynamic code analysis tools to better simulate real attacks and ensure the security of your project at runtime.
- Timely update dependent libraries and frameworks
Dependent libraries and frameworks are commonly used tools in Java development. However, there are also potential risks in these dependent libraries and frameworks. Security Question. Therefore, developers should update these dependent libraries and frameworks in a timely manner to ensure that they are using the latest and safe versions. In addition, when integrating these dependent libraries and frameworks, their security and configuration must also be carefully checked to avoid security vulnerabilities caused by improper integration.
- Write a security vulnerability repair plan
When a security vulnerability is discovered, developers need to develop a corresponding repair plan. Repair solutions may include but are not limited to patching the code, strengthening permission control, strengthening input validation, etc. The repair plan should be combined with specific vulnerability characteristics and project requirements to ensure the effectiveness and impact of the repair.
- Perform security testing
After the security vulnerability is repaired, developers should conduct security testing to ensure the effectiveness of the repair. Security testing can simulate various attack scenarios to check whether the repaired system still has potential security issues. Common security testing tools include OpenVAS and Nessus.
Summary:
Security vulnerability scanning and repair of Java development projects is an important part of ensuring project security. By understanding common security vulnerabilities, using static and dynamic code analysis tools, updating dependent libraries and frameworks in a timely manner, writing security vulnerability repair plans, and conducting security testing, the security of the project can be effectively improved. I hope that the introduction in this article will provide some help to Java developers when scanning and repairing security vulnerabilities.
The above is the detailed content of How to scan and repair security vulnerabilities in Java development projects. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
When logging into iTunesStore using AppleID, this error saying "This AppleID has not been used in iTunesStore" may be thrown on the screen. There are no error messages to worry about, you can fix them by following these solution sets. Fix 1 – Change Shipping Address The main reason why this prompt appears in iTunes Store is that you don’t have the correct address in your AppleID profile. Step 1 – First, open iPhone Settings on your iPhone. Step 2 – AppleID should be on top of all other settings. So, open it. Step 3 – Once there, open the “Payment & Shipping” option. Step 4 – Verify your access using Face ID. step
 How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
So, you took some great photos at your last party, but unfortunately, most of the photos you took were of red eyes. The photo itself is great, but the red eyes in it kind of ruin the image. Not to mention, some of those party photos might be from your friends’ phones. Today we'll look at how to remove red eye from photos. What causes the red eyes in the photo? Red-eye often occurs when taking photos with flash. This is because the light from the flash shines directly into the back of the eye, causing the blood vessels under the eye to reflect the light, giving the effect of red eyes in the photo. Fortunately, with the continuous advancement of technology, some cameras are now equipped with red-eye correction functions that can effectively solve this problem. By using this feature, the camera takes pictures
 Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
In the field of technological innovation, artificial intelligence (AI) is one of the most transformative and promising developments of our time. Artificial intelligence has revolutionized many industries, from healthcare and finance to transportation and entertainment, with its ability to analyze large amounts of data, learn from patterns, and make intelligent decisions. However, despite its remarkable progress, AI also faces significant limitations and challenges that prevent it from reaching its full potential. In this article, we will delve into the top ten limitations of artificial intelligence, revealing the limitations faced by developers, researchers, and practitioners in this field. By understanding these challenges, it is possible to navigate the complexities of AI development, reduce risks, and pave the way for responsible and ethical advancement of AI technology. Limited data availability: The development of artificial intelligence depends on data
 How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
When a Win11 user uses credentials to log in, he or she receives an error message stating that your credentials cannot be verified. What is going on? After the editor investigated this problem, I found that there may be several different situations that directly or indirectly cause this problem. Let's take a look with the editor.
 Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
A Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis, and Fixes During PHP development, we often encounter errors with HTTP status code 500. This error is usually called "500InternalServerError", which means that some unknown errors occurred while processing the request on the server side. In this article, we will explore the common causes of PHP500 errors, how to diagnose them, and how to fix them, and provide specific code examples for reference. Common causes of 1.500 errors 1.
 An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
Many friends always encounter blue screens when using computer operating systems. Even the latest win11 system cannot escape the fate of blue screens. Therefore, today I have brought you a tutorial on how to repair win11 blue screens. No matter whether you have encountered a blue screen or not, you can learn it first in case you need it. How to fix win11 blue screen method 1. If we encounter a blue screen, first restart the system and check whether it can start normally. 2. If it can start normally, right-click "Computer" on the desktop and select "Manage" 3. Then expand "System Tools" on the left side of the pop-up window and select "Event Viewer" 4. In the event viewer, we will You can see what specific problem caused the blue screen. 5. Then just follow the blue screen situation and events
 How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
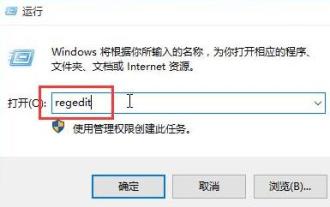
1. Press win+r to open the run window, enter [regedit] and press Enter to open the registry editor. 2. In the opened registry editor, click to expand [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun]. In the blank space on the right, right-click and select [New - String Value], and rename it to [systray.exe]. 3. Double-click to open systray.exe, modify its numerical data to [C:WindowsSystem32systray.exe], and click [OK] to save the settings.
 iPhone stuck in airplane mode: How to fix it
Jun 15, 2024 pm 02:16 PM
iPhone stuck in airplane mode: How to fix it
Jun 15, 2024 pm 02:16 PM
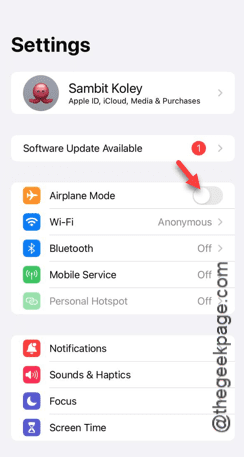
Airplane mode is very convenient in some situations. However, the same airplane mode may give you a headache if your iPhone suddenly gets stuck on it. In this article, we have designed this set of solutions to get your iPhone out of airplane mode. Quick fix – 1. Try disabling Airplane Mode directly from Control Center. 2. If you are unable to disable Airplane Mode from Control Center, you can disable Airplane Mode directly from the Settings tab – If these tips don’t work, follow the fixes below to resolve the issue. Fix 1 – Force Restart Your Device The process of force restarting your device is very simple. All you have to do is follow these step-by-step instructions. Step 1 – You can start the process by pressing and releasing the Volume Up button. step




