 Technology peripherals
Technology peripherals
 AI
AI
 The cybersecurity industry can draw inspiration from 'Musk's algorithm'
The cybersecurity industry can draw inspiration from 'Musk's algorithm'
The cybersecurity industry can draw inspiration from 'Musk's algorithm'
Today, we have entered an era of disruptive innovation driven by artificial intelligence and digital transformation. In this era, network security is no longer just the "cost and friction" of enterprise IT. On the contrary, it has become a key fulcrum for building the next generation of digital infrastructure and information order, as well as all technological innovations (from drug research and development to military intelligent manufacturing) necessary elements. This means that traditional network security technology research and development, program implementation, defense system design and operation all need to undergo a revolution in methods and concepts. Agility and intelligence have become the two main themes of network security evolution

In short, network security requires a Musk-style "out of the circle" revolution.
From electric cars to rockets to Starlink and even Twitter (X), Musk shows us how to use "first principles" to create a unique and efficient corporate culture and working methods - with the minimum People, infrastructure and processes achieve competitive advantage and maximize profits.
The "Musk Biography" written by Walter Isaacson refined and summarized the "Musk Algorithm" for the first time. For the cybersecurity industry that also faces complexity and cost challenges, we can draw wisdom from Musk’s way of thinking to strengthen our cybersecurity defenses and technological innovation.
At the same time, the Musk algorithm is also a concise and powerful working method and the condensation of corporate culture, providing a new perspective for network security companies and corporate security teams (and IT departments) to examine and optimize networks Security policies and practices. The following are the implications of the five important principles of Musk’s algorithm for the cybersecurity industry:
1. Musk’s algorithm emphasizes “questioning every need”
In the context of cybersecurity, this means We need to continually question and evaluate the effectiveness and necessity of security policies and measures. We should avoid rigid rules and excessive complexity and instead pursue simple, straightforward and practical security solutions. Cybersecurity is a field with highly complex technology stacks and methods, which can easily lead to the phenomenon of "pluralistic ignorance" - employees are afraid to express their ideas or question a tool, process, or framework because of fear of making a fool of themselves or a herd mentality. , decision-making or effectiveness of requirements
2. "Delete any tools or processes that you can delete"
In network security management, we need to regularly review and optimize security policies and tools, clear Those parts that are no longer necessary or ineffective to keep security defenses simple and efficient. At present, the proliferation of tools has caused the network security defense system to become bloated and inefficient, and the operating costs remain high. However, the technology that really needs innovation and upgrades lacks budget
3. "Simplification and optimization" is Musk's Another core principle of the algorithm
When executing network security policies, we should strive to maximize effectiveness and efficiency and avoid unnecessary complexity and redundancy. After Musk took over Twitter, he cut three-quarters of redundant personnel and migrated data processing tasks from the Amazon cloud to local servers. This move saved X 60% of cloud costs every year
In addition , Musk’s engineering team also made drastic optimizations:
Rebuilt the API middleware layer in the technology stack, simplified the architecture, and deleted more than 100,000 lines of code and thousands of unused internal endpoints and idle client services. This reduces metadata retrieval delays by 50% and global API timeout errors by 90%. Compared with 2022, the system blocks bots and content scraping 37% faster
4. Musk’s emphasis on “reducing cycle times” also applies to the cybersecurity field, because cybersecurity defense is a Dynamic and continuous process
Time is life, time is safety! We should quickly respond to new threats and challenges and quickly update and optimize security policies and measures. Design, implement and operate network security solutions around shortening key time cycle indicators such as MTTD (Mean Time to Detection), MTTR (Mean Time to Response) and MTTC (Mean Time to Contain).
5. Automation
One goal of cybersecurity operations is to achieve a “black light SoC”. Through the automation of technology, tools and processes, we can automate security management, thereby significantly reducing operating costs and improving the efficiency and effectiveness of security defense
In this digital era full of challenges and opportunities, by learning from and By applying Musk's algorithm, enterprises can build a more flexible, efficient and powerful network security defense system.
Finally, we need to realize that no one method or strategy is perfect. In practice, we also need to flexibly adjust and optimize security policies according to our own actual conditions and needs to achieve the best security defense effect. We must build a more secure and reliable network environment with an innovative and pragmatic attitude
The above is the detailed content of The cybersecurity industry can draw inspiration from 'Musk's algorithm'. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
This site reported on June 27 that Jianying is a video editing software developed by FaceMeng Technology, a subsidiary of ByteDance. It relies on the Douyin platform and basically produces short video content for users of the platform. It is compatible with iOS, Android, and Windows. , MacOS and other operating systems. Jianying officially announced the upgrade of its membership system and launched a new SVIP, which includes a variety of AI black technologies, such as intelligent translation, intelligent highlighting, intelligent packaging, digital human synthesis, etc. In terms of price, the monthly fee for clipping SVIP is 79 yuan, the annual fee is 599 yuan (note on this site: equivalent to 49.9 yuan per month), the continuous monthly subscription is 59 yuan per month, and the continuous annual subscription is 499 yuan per year (equivalent to 41.6 yuan per month) . In addition, the cut official also stated that in order to improve the user experience, those who have subscribed to the original VIP
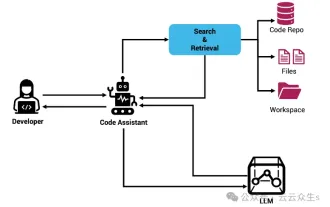 Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Improve developer productivity, efficiency, and accuracy by incorporating retrieval-enhanced generation and semantic memory into AI coding assistants. Translated from EnhancingAICodingAssistantswithContextUsingRAGandSEM-RAG, author JanakiramMSV. While basic AI programming assistants are naturally helpful, they often fail to provide the most relevant and correct code suggestions because they rely on a general understanding of the software language and the most common patterns of writing software. The code generated by these coding assistants is suitable for solving the problems they are responsible for solving, but often does not conform to the coding standards, conventions and styles of the individual teams. This often results in suggestions that need to be modified or refined in order for the code to be accepted into the application
 Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Large Language Models (LLMs) are trained on huge text databases, where they acquire large amounts of real-world knowledge. This knowledge is embedded into their parameters and can then be used when needed. The knowledge of these models is "reified" at the end of training. At the end of pre-training, the model actually stops learning. Align or fine-tune the model to learn how to leverage this knowledge and respond more naturally to user questions. But sometimes model knowledge is not enough, and although the model can access external content through RAG, it is considered beneficial to adapt the model to new domains through fine-tuning. This fine-tuning is performed using input from human annotators or other LLM creations, where the model encounters additional real-world knowledge and integrates it
 Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
To learn more about AIGC, please visit: 51CTOAI.x Community https://www.51cto.com/aigc/Translator|Jingyan Reviewer|Chonglou is different from the traditional question bank that can be seen everywhere on the Internet. These questions It requires thinking outside the box. Large Language Models (LLMs) are increasingly important in the fields of data science, generative artificial intelligence (GenAI), and artificial intelligence. These complex algorithms enhance human skills and drive efficiency and innovation in many industries, becoming the key for companies to remain competitive. LLM has a wide range of applications. It can be used in fields such as natural language processing, text generation, speech recognition and recommendation systems. By learning from large amounts of data, LLM is able to generate text
 To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
Editor |ScienceAI Question Answering (QA) data set plays a vital role in promoting natural language processing (NLP) research. High-quality QA data sets can not only be used to fine-tune models, but also effectively evaluate the capabilities of large language models (LLM), especially the ability to understand and reason about scientific knowledge. Although there are currently many scientific QA data sets covering medicine, chemistry, biology and other fields, these data sets still have some shortcomings. First, the data form is relatively simple, most of which are multiple-choice questions. They are easy to evaluate, but limit the model's answer selection range and cannot fully test the model's ability to answer scientific questions. In contrast, open-ended Q&A
 Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Machine learning is an important branch of artificial intelligence that gives computers the ability to learn from data and improve their capabilities without being explicitly programmed. Machine learning has a wide range of applications in various fields, from image recognition and natural language processing to recommendation systems and fraud detection, and it is changing the way we live. There are many different methods and theories in the field of machine learning, among which the five most influential methods are called the "Five Schools of Machine Learning". The five major schools are the symbolic school, the connectionist school, the evolutionary school, the Bayesian school and the analogy school. 1. Symbolism, also known as symbolism, emphasizes the use of symbols for logical reasoning and expression of knowledge. This school of thought believes that learning is a process of reverse deduction, through existing
 SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
Editor | KX In the field of drug research and development, accurately and effectively predicting the binding affinity of proteins and ligands is crucial for drug screening and optimization. However, current studies do not take into account the important role of molecular surface information in protein-ligand interactions. Based on this, researchers from Xiamen University proposed a novel multi-modal feature extraction (MFE) framework, which for the first time combines information on protein surface, 3D structure and sequence, and uses a cross-attention mechanism to compare different modalities. feature alignment. Experimental results demonstrate that this method achieves state-of-the-art performance in predicting protein-ligand binding affinities. Furthermore, ablation studies demonstrate the effectiveness and necessity of protein surface information and multimodal feature alignment within this framework. Related research begins with "S
 Laying out markets such as AI, GlobalFoundries acquires Tagore Technology's gallium nitride technology and related teams
Jul 15, 2024 pm 12:21 PM
Laying out markets such as AI, GlobalFoundries acquires Tagore Technology's gallium nitride technology and related teams
Jul 15, 2024 pm 12:21 PM
According to news from this website on July 5, GlobalFoundries issued a press release on July 1 this year, announcing the acquisition of Tagore Technology’s power gallium nitride (GaN) technology and intellectual property portfolio, hoping to expand its market share in automobiles and the Internet of Things. and artificial intelligence data center application areas to explore higher efficiency and better performance. As technologies such as generative AI continue to develop in the digital world, gallium nitride (GaN) has become a key solution for sustainable and efficient power management, especially in data centers. This website quoted the official announcement that during this acquisition, Tagore Technology’s engineering team will join GLOBALFOUNDRIES to further develop gallium nitride technology. G



