 Web Front-end
Web Front-end
 JS Tutorial
JS Tutorial
 Node.js development: How to implement user rights management functions
Node.js development: How to implement user rights management functions
Node.js development: How to implement user rights management functions

Title: Node.js Development: User Rights Management Function Implementation and Code Examples
Abstract: As the complexity of web applications and systems continues to increase, user rights Management becomes an important function that cannot be ignored. This article will introduce how to implement user rights management functions in Node.js development and give specific code examples.
Introduction:
As an efficient and lightweight development platform, Node.js has a wide range of application scenarios. In the development of many Node.js applications, user rights management is often one of the essential functions. Through user rights management, we can perform operations such as identity authentication, access control, and permission configuration on users to ensure the security and stability of the system.
1. Basic principles of user rights management
- Authentication: When users access the system or application, they need to undergo authentication to identify their identity.
- Access control: Grant different access rights based on different user identities.
- Permission configuration: Grant or deprive users of permissions to achieve fine-grained control.
2. Implementation of user rights management function
In Node.js development, we can use some third-party modules to implement user rights management functions, such as: Express.js, Passport.js and Mongoose.js, etc.
-
Install the required modules
First, install the required modules in the project. Open the terminal, switch to the project directory, and execute the following command:$ npm install express passport passport-local mongoose
Copy after login - Create database model
Use Mongoose.js to connect to the database and create the user model and permission model. Create a folder namedmodelsin the project root directory, and create two filesuser.jsandpermission.jsin it.
user.js file code example:
const mongoose = require('mongoose'); const Schema = mongoose.Schema; const UserSchema = new Schema({ username: String, password: String, permissions: [{ type: Schema.Types.ObjectId, ref: 'Permission' }] }); module.exports = mongoose.model('User', UserSchema);Copy after loginpermission.js file code example:
const mongoose = require('mongoose'); const Schema = mongoose.Schema; const PermissionSchema = new Schema({ name: String, description: String }); module.exports = mongoose.model('Permission', PermissionSchema);Copy after login
- Create Routes and Controllers
Create a folder namedroutesin the project root directory and createusers.jsandpermissions.jsTwo files.
users.js file code example:
const express = require('express'); const router = express.Router(); const User = require('../models/user'); // 用户登录 router.post('/login', (req, res) => { // 验证用户身份 // ... }); // 用户注册 router.post('/register', (req, res) => { // 创建新用户 // ... }); // 获取用户信息 router.get('/:id', (req, res) => { // 获取指定用户信息 // ... }); module.exports = router;Copy after loginpermissions.js file code example:
const express = require('express'); const router = express.Router(); const Permission = require('../models/permission'); // 获取所有权限 router.get('/', (req, res) => { // 获取所有权限信息 // ... }); // 创建新权限 router.post('/', (req, res) => { // 创建新权限 // ... }); module.exports = router;Copy after login
- Configuring the application
Create a file namedapp.jsin the project root directory and configure routing and middleware in it.
app.js file code example:
const express = require('express'); const app = express(); const mongoose = require('mongoose'); const userRoutes = require('./routes/users'); const permissionRoutes = require('./routes/permissions'); // 连接数据库 mongoose.connect('mongodb://localhost/your_database'); // 配置中间件 app.use(express.json()); app.use('/users', userRoutes); app.use('/permissions', permissionRoutes); // 启动应用程序 app.listen(3000, () => { console.log('Server is running on port 3000'); });Copy after login
3. Summary
Through the above example code, we can see How to implement user rights management function in Node.js development. Of course, actual applications may involve more details and complexities, such as user authentication methods, permission grouping, permission inheritance, etc. But the basic principles and implementation methods are similar.
By using appropriate tools and modules, we can easily implement user rights management functions in Node.js and ensure system security and stability. I hope this article will help you understand and use the user rights management function in Node.js development. Happy coding!
The above is the detailed content of Node.js development: How to implement user rights management functions. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1359
1359
 52
52
 How to use Laravel to implement image processing functions
Nov 04, 2023 pm 12:46 PM
How to use Laravel to implement image processing functions
Nov 04, 2023 pm 12:46 PM
How to use Laravel to implement image processing functions requires specific code examples. Nowadays, with the development of the Internet, image processing has become an indispensable part of website development. Laravel is a popular PHP framework that provides us with many convenient tools to process images. This article will introduce how to use Laravel to implement image processing functions, and give specific code examples. Install LaravelInterventionImageInterven
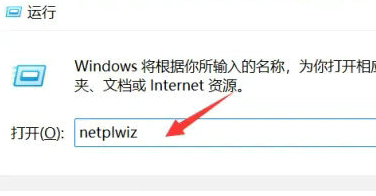 Win11 user permissions setting tutorial: How to configure Win11 user permissions
Jan 29, 2024 pm 08:33 PM
Win11 user permissions setting tutorial: How to configure Win11 user permissions
Jan 29, 2024 pm 08:33 PM
Some users will create multiple accounts when using computers, but some users' accounts do not have permissions, which means some operations cannot be performed directly? How to set user permissions in Win11? Users who are not sure can come to this site to see related strategies. How to set user permissions in Win11 1. Directly create the run function through the shortcut key combination [win+R], then enter [netplwiz] in the search box and click OK. 3. In the properties window that opens, click Group Members in the upper menu bar. 5. A window prompt will appear. Just click [Yes] to log out and restart the account to complete the settings.
 Use uniapp to implement image rotation function
Nov 21, 2023 am 11:58 AM
Use uniapp to implement image rotation function
Nov 21, 2023 am 11:58 AM
Using uniapp to implement image rotation function In mobile application development, we often encounter scenarios where images need to be rotated. For example, the angle needs to be adjusted after taking a photo, or an effect similar to the rotation of a camera after taking a photo is achieved. This article will introduce how to use the uniapp framework to implement the image rotation function and provide specific code examples. uniapp is a cross-platform development framework based on Vue.js, which can simultaneously develop and publish applications for iOS, Android, H5 and other platforms. Implemented in uniapp
 PHP development: How to implement the image verification code function
Sep 20, 2023 pm 04:00 PM
PHP development: How to implement the image verification code function
Sep 20, 2023 pm 04:00 PM
PHP development: How to implement the image verification code function In WEB development, in order to prevent robots or malicious attacks, it is often necessary to use verification codes to verify the user's identity. Among them, picture verification code is a common type of verification code, which can not only effectively identify users, but also improve user experience. This article will introduce how to use PHP to implement the image verification code function and provide specific code examples. 1. Generate verification code images First, we need to generate verification code images with random characters. PHP provides the GD library to easily generate images. the following
 How to use WordPress plug-in to implement instant query function
Sep 06, 2023 pm 12:39 PM
How to use WordPress plug-in to implement instant query function
Sep 06, 2023 pm 12:39 PM
How to use WordPress plug-ins to achieve instant query function WordPress is a powerful blog and website building platform. Using WordPress plug-ins can further expand the functions of the website. In many cases, users need to perform real-time queries to obtain the latest data. Next, we will introduce how to use WordPress plug-ins to implement instant query functions and provide some code samples for reference. First, we need to choose a suitable WordPress plug-in to achieve instant query
 How to implement user login and permission control in PHP?
Jun 29, 2023 pm 02:28 PM
How to implement user login and permission control in PHP?
Jun 29, 2023 pm 02:28 PM
How to implement user login and permission control in PHP? When developing web applications, user login and permission control are one of the very important functions. Through user login, we can authenticate the user and perform a series of operational controls based on the user's permissions. This article will introduce how to use PHP to implement user login and permission control functions. 1. User login function Implementing the user login function is the first step in user verification. Only users who have passed the verification can perform further operations. The following is a basic user login implementation process: Create
 PHP development: How to implement WeChat login function
Sep 21, 2023 pm 03:13 PM
PHP development: How to implement WeChat login function
Sep 21, 2023 pm 03:13 PM
PHP development: How to implement the WeChat login function, specific code examples are required Introduction: With the rapid development of the mobile Internet, WeChat, as one of China's largest social media platforms, plays an important role in application development. WeChat login is a common login method in many applications and websites, providing a convenient, fast and secure authentication method. This article will introduce how to use PHP to implement the WeChat login function and provide specific code examples. Step 1: Apply for a WeChat open platform account and create an application. Before starting, we need to apply first
 How to use go language to implement smart contract functions
Aug 26, 2023 am 10:19 AM
How to use go language to implement smart contract functions
Aug 26, 2023 am 10:19 AM
How to use Go language to implement the functions of smart contracts. Smart contracts are a form of contract based on blockchain technology. It runs on the blockchain and can automatically execute the agreements in it. In recent years, smart contracts have received widespread attention and application and can be used to implement automated business logic in a variety of scenarios. This article will introduce how to use Go language to implement smart contract functions and provide corresponding code examples. 1. Blockchain development library in Go language. Before using Go language to develop smart contracts, we need to choose a suitable blockchain development library. Head



